- Policies
- Refund Policy
- Privacy policy
- Company
- About M3 Software

This post covers all you need know about the partition in Windows operating system, such as what it does, and if we can be extend or delete it, etc.
This post explains what disk partition is in the Windows operating system, and it also tells you why to partition a disk and how to check disk partition in Windows.
This post illustrates what the Disk tab in Task Manager reveals, what each metric (eg., disk usage, disk active time ) means, and how you can use this data to maintain performance.

This article helps understand the Windows recovery partition. Though invisible on a daily basis, we can bring it into full play to restore the Windows system. It can also be deleted and created.

This post primarily explores primary vs extended vs logical partition on Windows and the connections between them.

This post elaborates on the difference between system partition and boot partition on a Windows computer.

This post elaborates on the phrase Drive 0 Partition 1: Recovery on Windows operating systems.

This post revolves around the Encrypting File System (EFS) on Windows. It also shows how to encrypt a file or folder with the Encrypting File System.

This post illustrates the unallocated partition's disadvantages and solutions if you want to use it as a normal partition on Windows.

This post introduces what is RAW partition is, why it is formed, and the step-by-step fixes or solutions. iBoysoft Data Recovery is the master of all; let it fix your RAW drive and recover data.

This post illustrates the Windows feature -the Run dialog. It can rapidly execute commands and open programs via simple shortcuts (Win+R). And the Run dialog as an administrator gives higher access.

This article discusses RAM (Random Access Memory), which is different from a hard disk. It serves as temporary memory that stores data the computer is currently using, and it is the fastest.
This article dives into Pagefile.sys file and discusses whether the Pagefile.sys file can be safely deleted on Windows.

This post revolves around the clipboard on Windows, discussing what it is, how it works, and how to access it on Windows.

This post focuses on Windows Clean Boot vs Safe Mode, making it easy for users to decide which on to choose based on difference situations.

This post revolves around hot backup vs cold backup and discusses which one to choose based on different situations.
This post primarily summarizes the full backup advantages and disadvantages, and it also shows the efficient way to complete a full disk backup on a Windows PC.

This post gives details on incremental backup and briefly explains the difference between incremental and differential backup.

This post explains what Windows disk defragmentation does and shows how to perform disk defragmentation in Windows 10/11.

This post elaborates on incremental backup vs different backup on Windows.
This post introduces everything you need to know about Windows temporary files and shows how to clear Windows temporary files in Windows 10/11 using different methods.
This post explains what Windows Command Prompt is and shows how to open a Command Prompt in Windows.
This post offers an overview of Device Manager in Windows, its key functions and common uses. It also shows different ways to access Windows Device Manager.

This post elaborates on Windows Storage Sense and shows how to turn on Storage Sense in Windows 10.

This post introduces what system information in Windows contains and how to access system information in Windows 10.

A brief introduction to Windows Disk Cleanup and the way to use it to free disk space on Windows.

This post introduces Volume Shadow Copy Service and the key role it plays in the Windows operating system.

This article gives an overview of Windows Recycle Bin and tells you where to find Recycle Bin in Windows 10. Useful tips on using Recycle Bin are provided.
This article delves into the role, types, and functioning of device drivers in Windows, and the role, types, and functioning of device drivers in Windows.
This post demonstrates the fallacy in the BitLocker folder and clarifies folder-level encryption. Admirably, iBoysoft DiskGeeker for Windows offers an alternative to BitLocker.
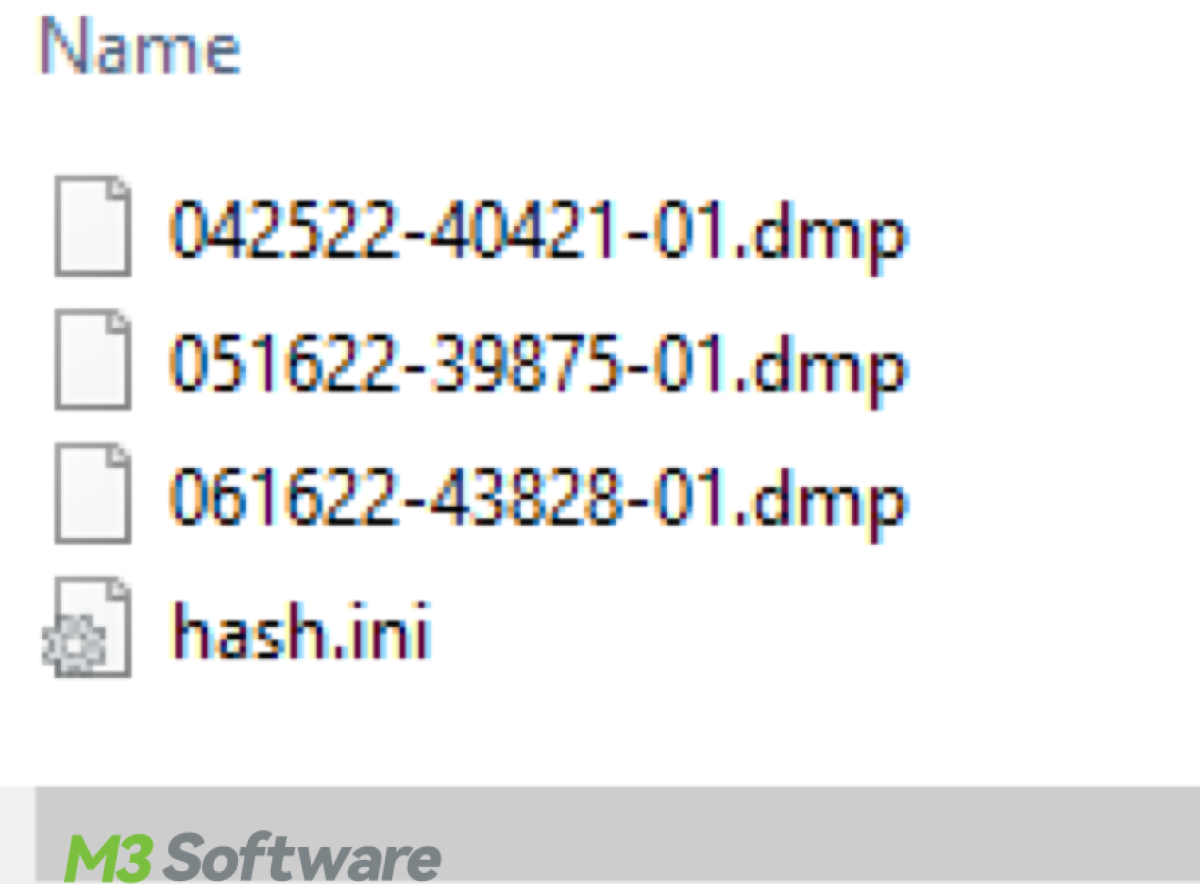
This article defines memory.dmp consisting of its location and specific types, explains why we should delete it on Windows devices. Note that iBoysoft DiskGeeker helps filter memory.dmp.
This post briefly explains what the Winver is in Windows OS and how to use Winver in different ways.
This post discusses winver command, a direct tool to check Windows version. systeminfo, wmic can also achieve that. But it cannot be used remotely. Its limitations are overcome by PowerShell commands.

This post discusses what clipboard sync is in Windows settings. The clipboard sync extension and apps are involved if you need synchronization between Android and Windows or other platforms.

This post primarily discusses the quick format vs full format in the Windows operating system, focusing on the main differences between them.

This post illustrates what God Mode in Windows is. Windows God Mode is a special folder that grants quick access to a centralized list of system settings and administrative tools, offering convenience

This article explains that Windows Sandbox is an isolated environment for testing suspicious software or browsing risky websites without affecting main system, also offers how to get and us Sandbox.
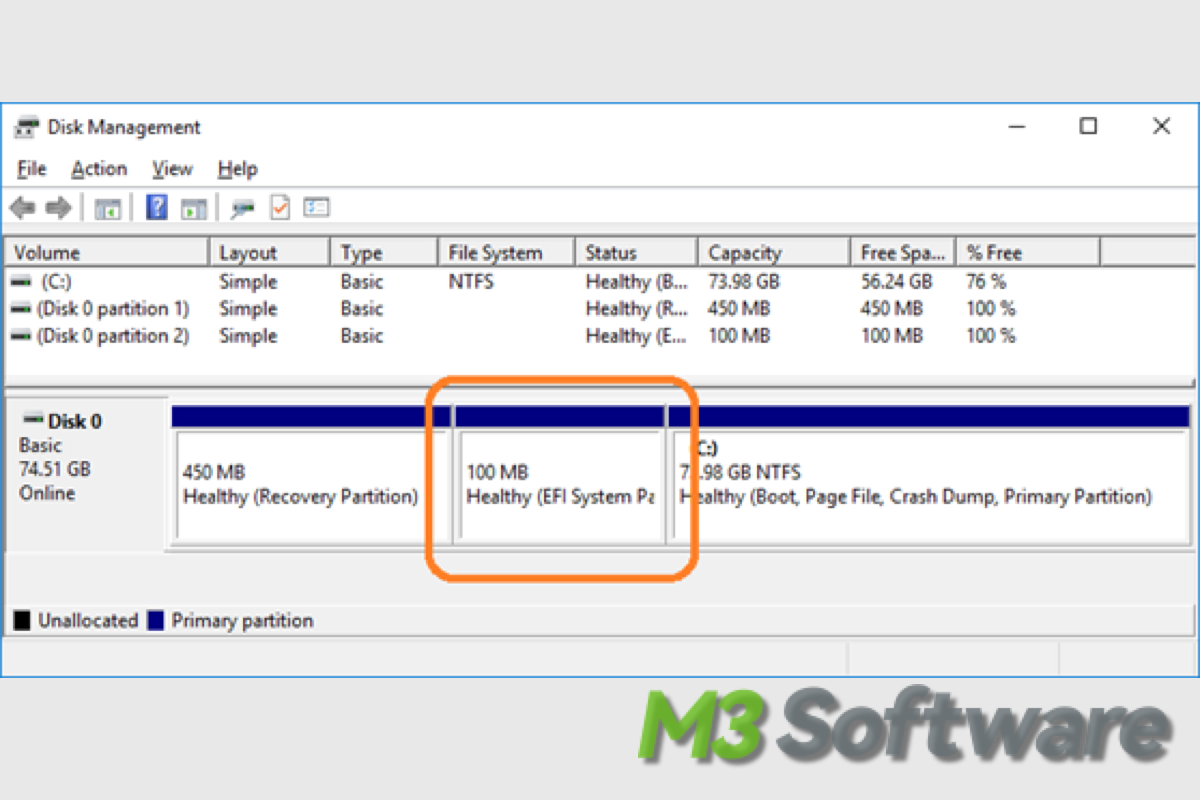
This post explains the EFI system partition on Windows startup disk, you will know what the EFI partition is used for, and it also answers whether you can delete the EFI system partition.

This article defines how to use CHKDSK for repairing disks, clarifying the key CHKDSK commands containing chkdsk, chkdsk /f, chkdsk c:/f /r, chkdsk /f /r /x, and steps to take to resolve errors.
A brief introduction to Data Execution Prevention, including its advantages and disadvantages, and how to enable and disable it on Windows.

What is overwriting in computer? This post dives into this question and tells everything you want to know about data overwriting.

This post articulates what System File Checker is, what it does, whether it actually works, common misconceptions (like /f /r), and how it connects with DISM to fully restore system health.
This post primarily discusses what the file compression is, how it works, and why we need it.
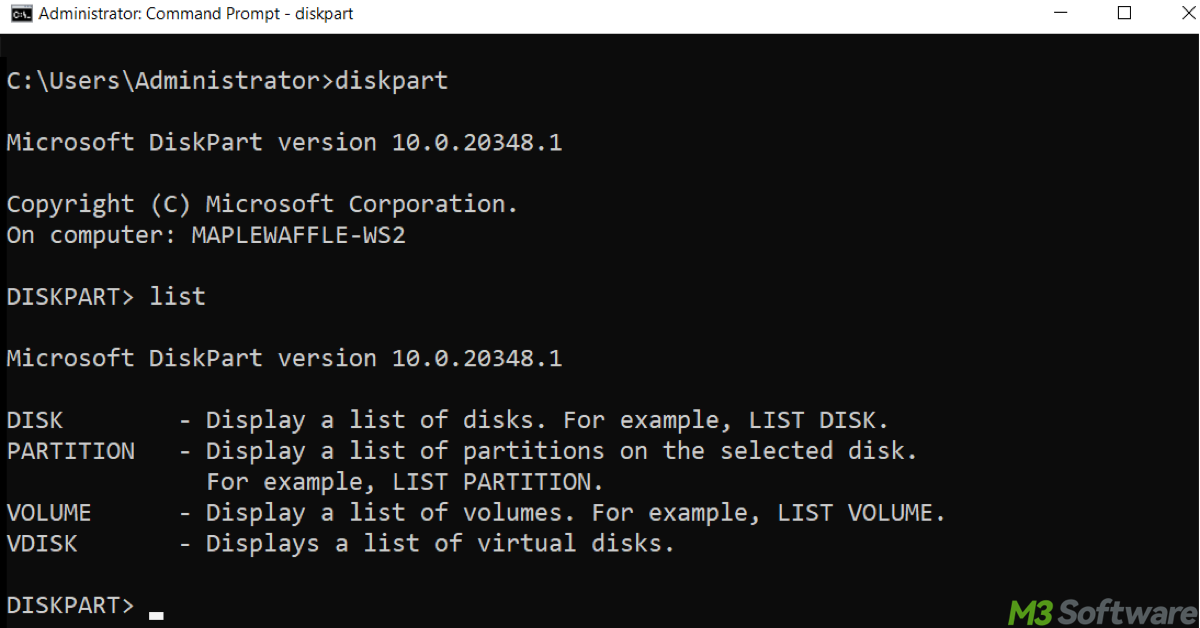
This article introduces DiskPart, lists its core commands, and guides you through two practical use cases — formatting a USB drive and cleaning an SD card- with streamlined steps.
Does a factory reset delete everything on Windows 10? This post revolves around the question and discusses when we need a factory reset.
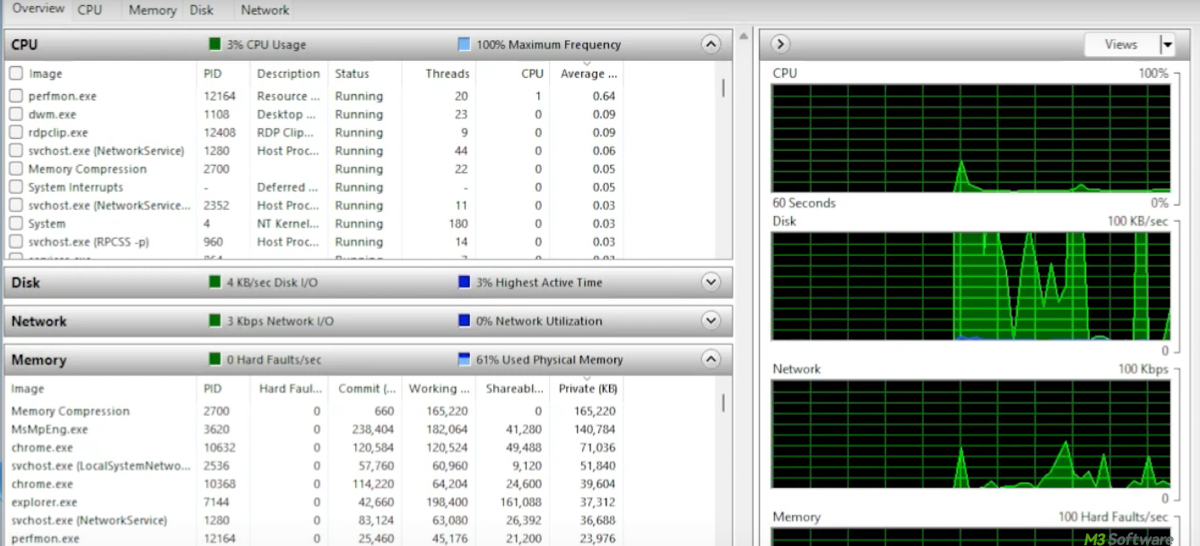
This post exposes what the Resource Monitor of Windows is, including its traits and uses. It provides real-time data on CPU, memory, disk, and network usage, helping identify resource hogs.
This article summarizes the evolution of widgets from Windows 10 to Windows 11, highlighting their features, access methods, and customization options.

This article pinpoints whether you can use BitLocker in Linux and how to access/unlock the BitLocker encrypted drive in Linux.
This post explores what WSL is, how to enable, use, and uninstall it, its GUI capabilities, and how to choose the best WSL version.
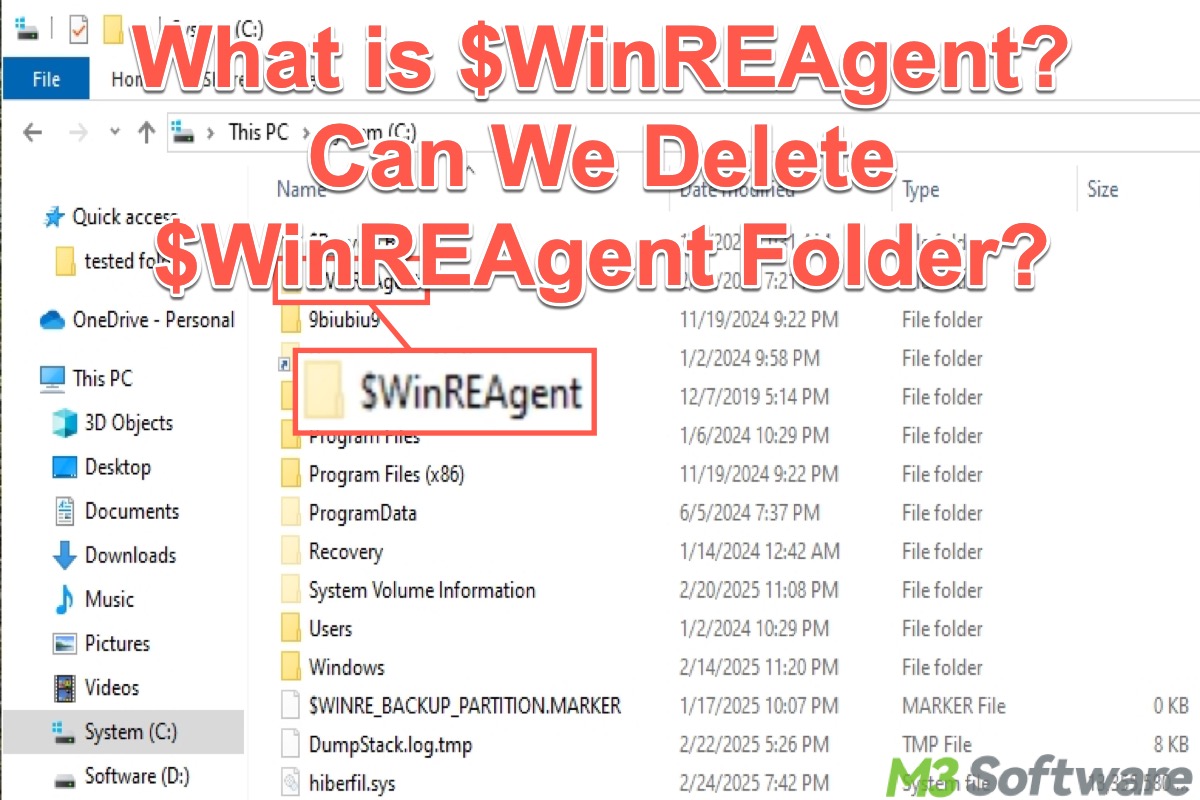
This post explains what the $WinREAgent folder is on Windows OS and discusses whether you can delete it.
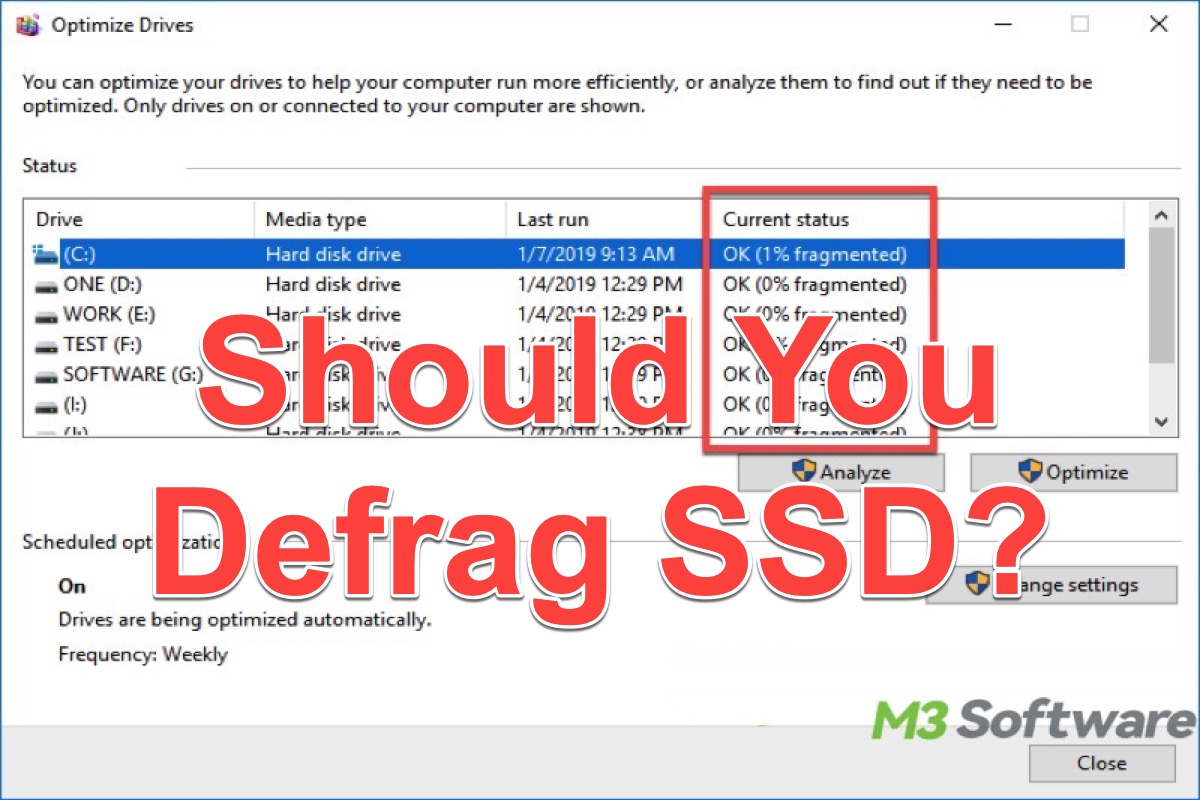
This post primarily discusses whether we should defrag SSD on a Windows PC and explains why.
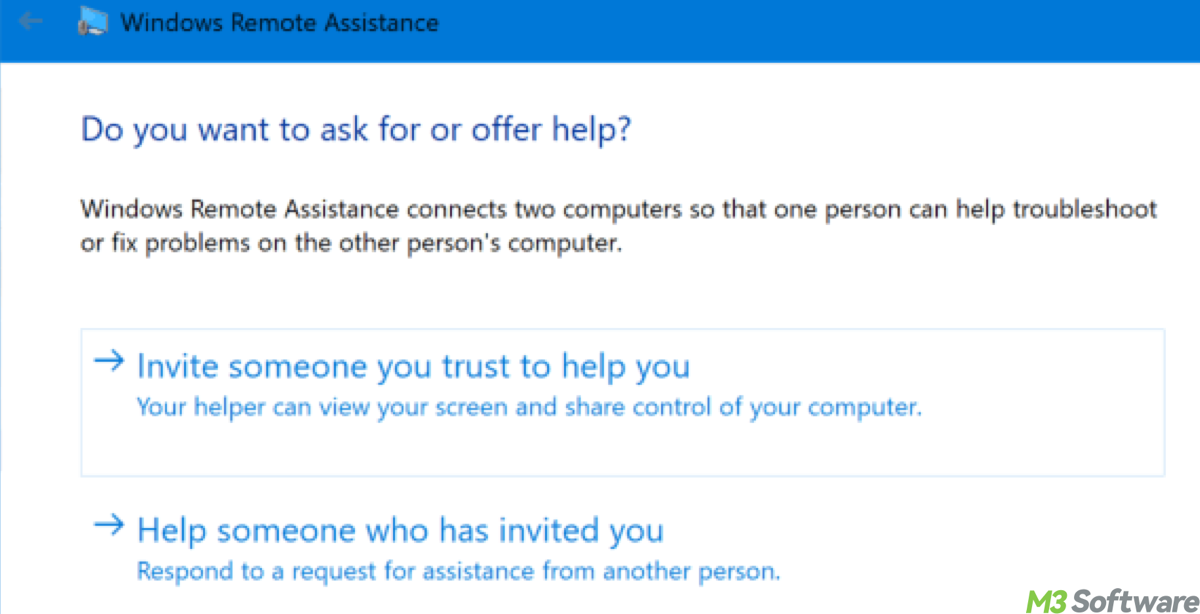
This article explains Windows Remote Assistance and compares it with another common feature, Quick Assist. It also includes how to enable Remote Assistance and disable it.
This article lists common file name extensions and what we should know to discern them for Mac and Windows.

This post pivots on RAR vs ZIP compression and primarily elaborates the top differences between them.
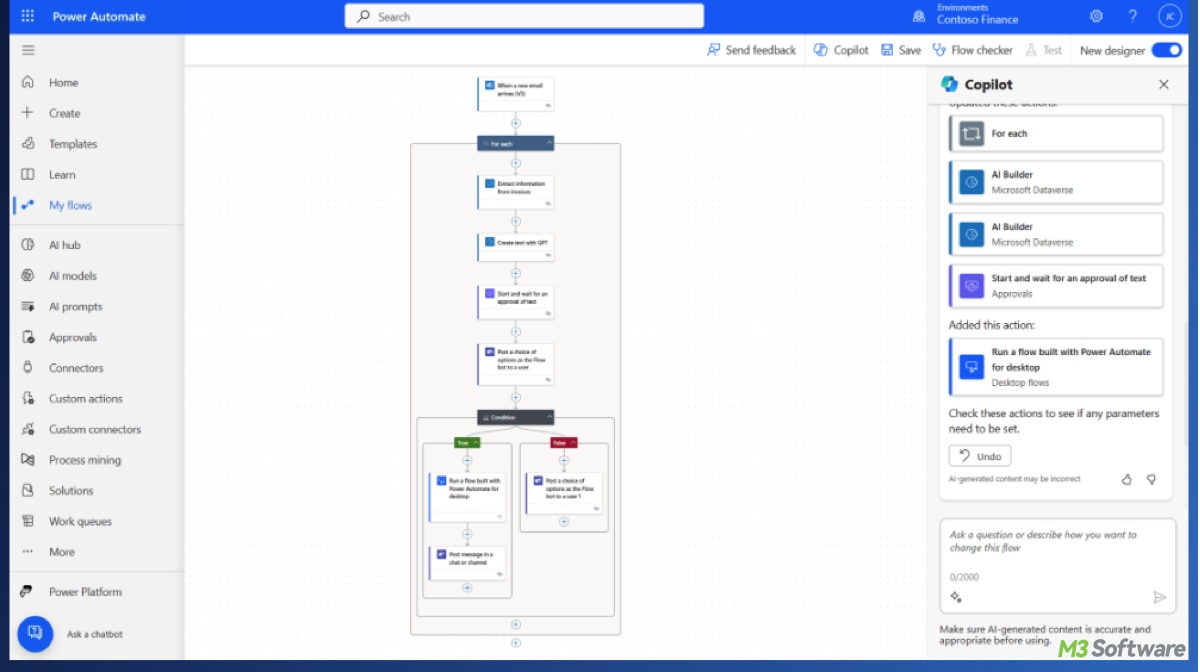
This post defines Microsoft Power Automate including its different types of flows, common use cases, and when to use it so as to drive productivity and digital transformation.
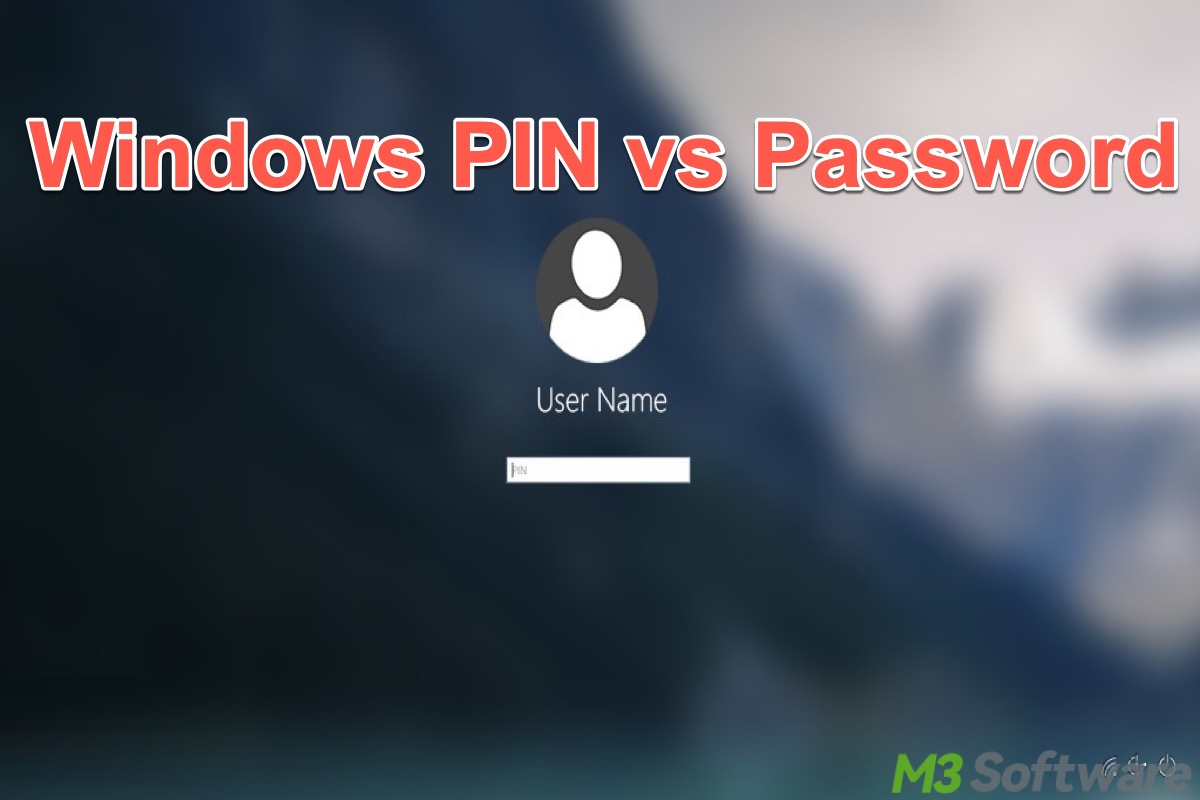
This post primarily discusses the Windows PIN vs Password and tells the main differences between them.
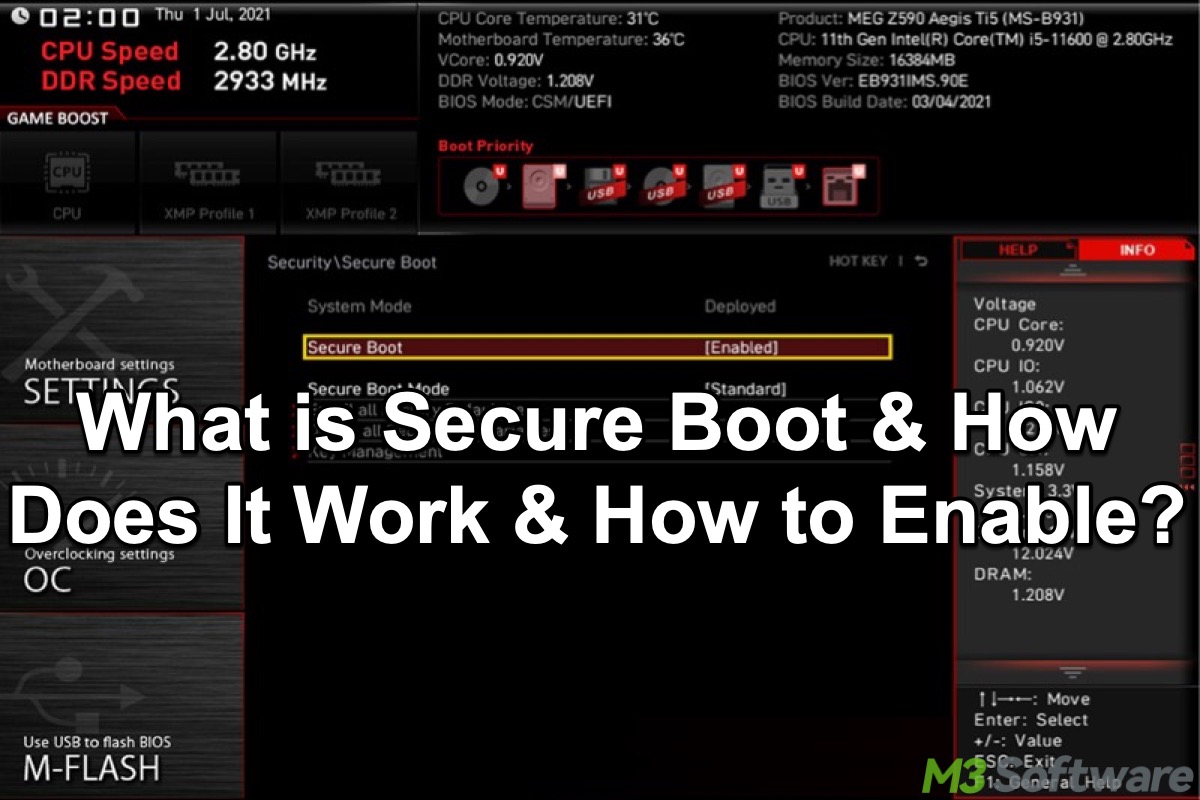
This post revolves around the Secure Boot feature on Windows OS, which explains what Secure Boot is, how it works, and how to enable Secure Boot on Windows 11.
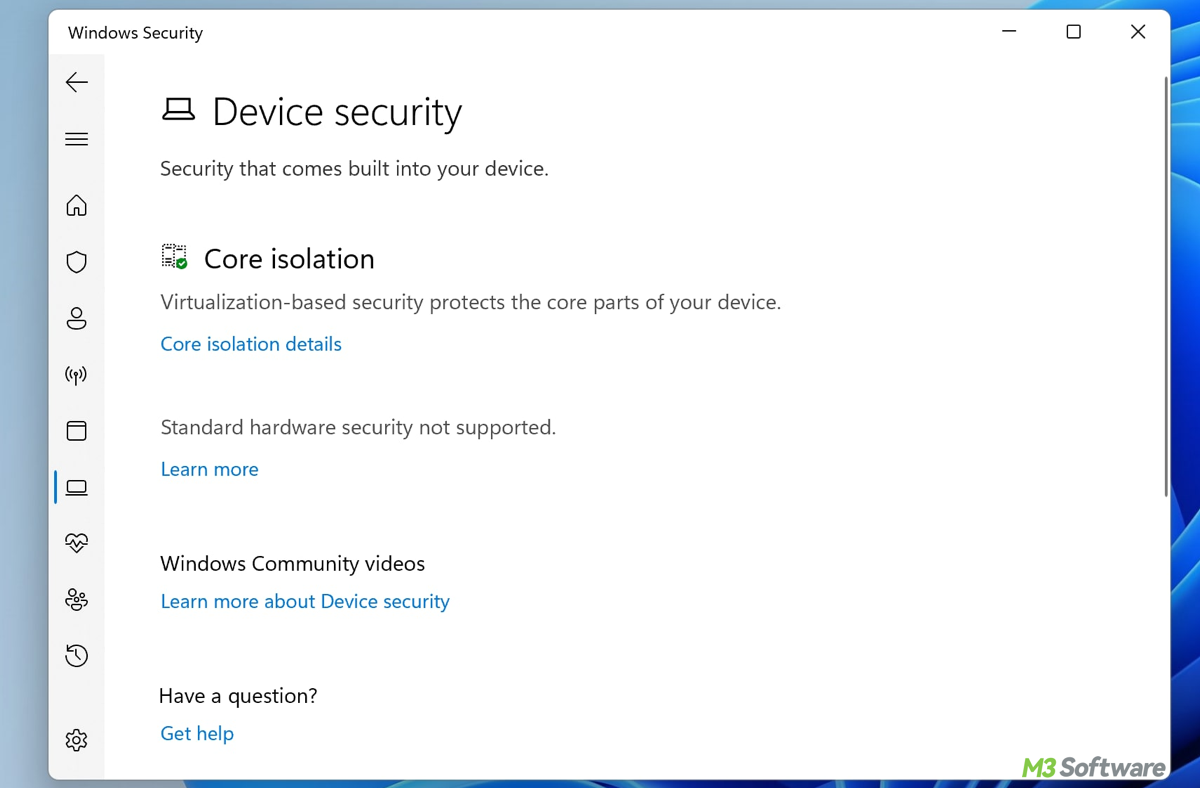
This post elaborates on VBS, an advanced security feature that leverages hardware virtualization to isolate critical parts of the system.

This post helps comprehend Windows Defender Application Guard, how to enable it to defend your PC including its extension and Managed Mode. If it's unavailable, its alternatives are covered here.
This post makes clear of BitLocker in dual boot whether it's BitLocker dual boot for two Windows or for Windows & Linux and their caveats and step-by-step guide to set up BitLocker in dual boot.
This post primarily explains the Windows.old folder in Windows OS and discusses whether it can be deleted.
This article provides a sketchy description of Task Scheduler, its usage, and how to make the most of it. We'll also cover the potential risks of disabling it and how to manage the scheduled tasks eff
This post primarily explains what the Windows.edb file is and whether you can delete windows edb file in Windows OS.

This post briefly introduces Windows File History and how it works in Windows, and steps to enable it are also involved.

This article scrapes more about Windows Defender including ways to control, whitelist, and reinstall Microsoft Defender Antivirus, covering third-party options.
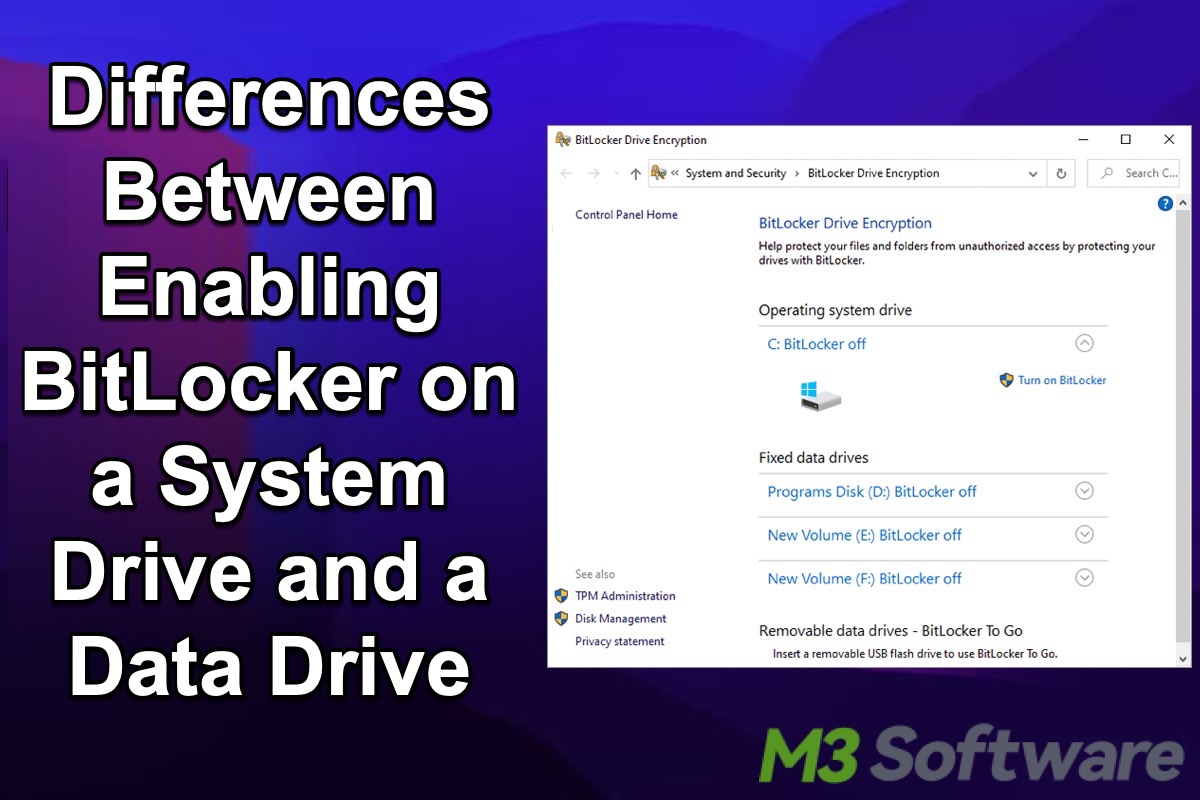
This post shows the main differences in BitLocker encryption between the system drive and the data drive on Windows.
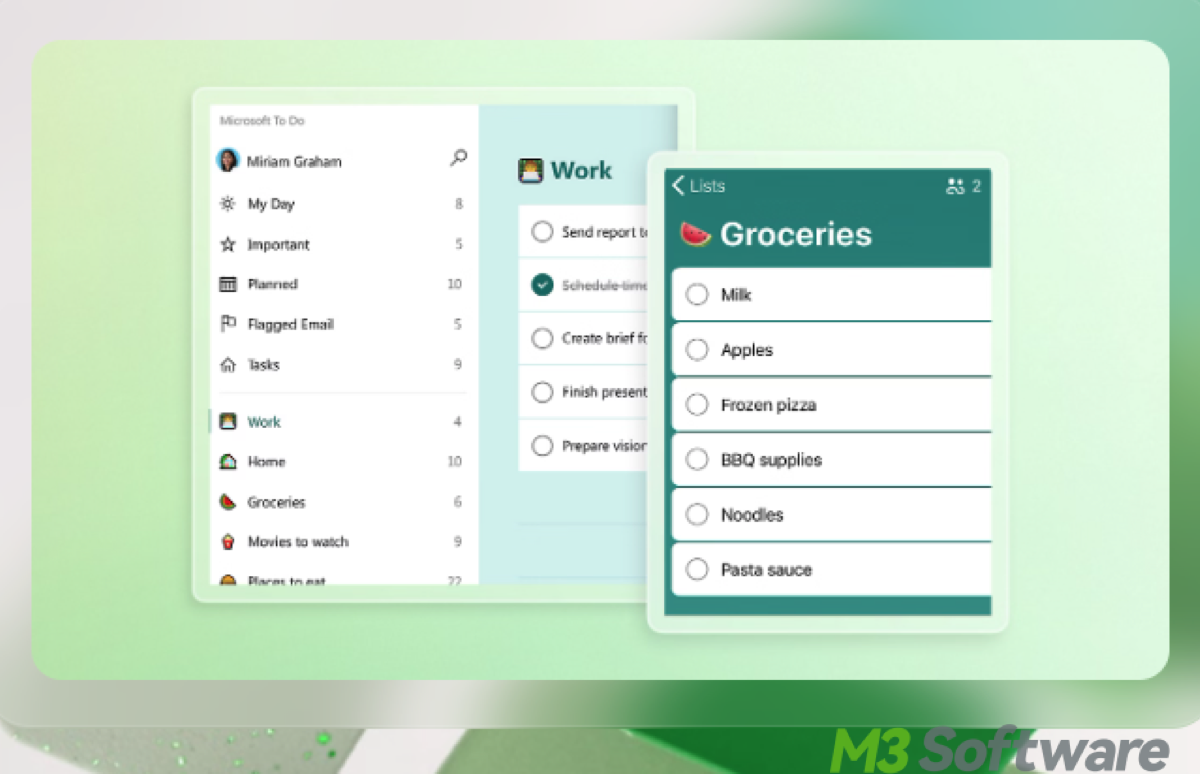
This article explores everything you need to know about Microsoft To Do: how to download and use it across various devices, the app's key features, and how it integrates with Microsoft 365 tools.
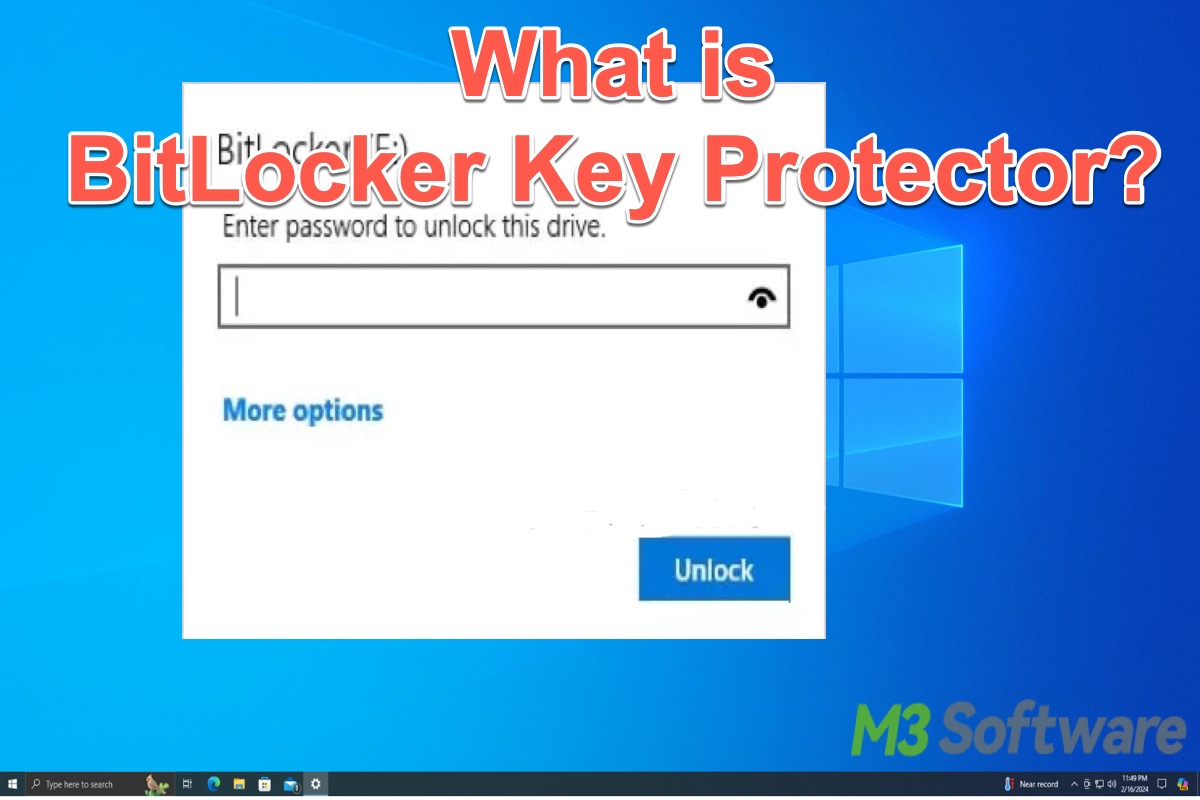
This post primarily explains what the BitLocker key protector is and how to understand BitLocker key protectors.
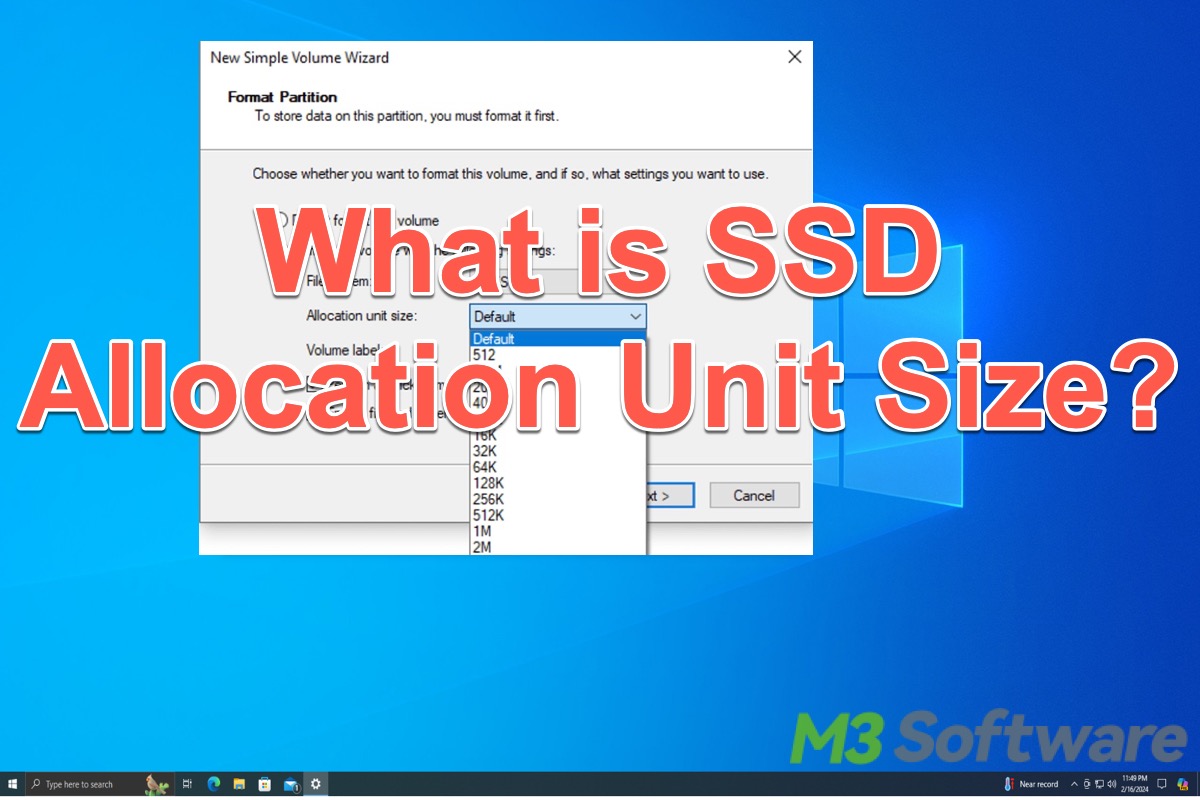
This post outlines SSD allocation unit size on Windows OS and how it affects SSD performance. The steps of checking and adjusting SSD allocation unit size are involved.
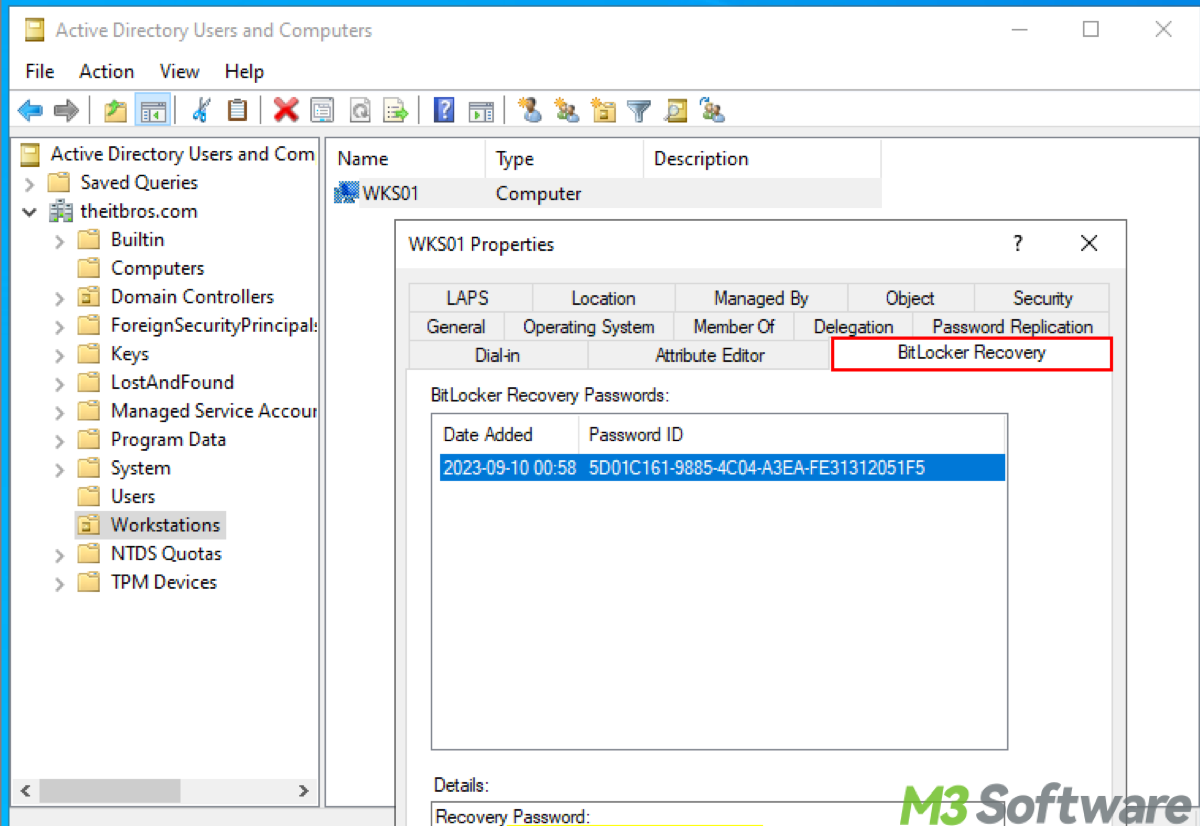
This post explains the BitLocker Recovery Key Active Directory and how to access the BitLocker Recovery Key in it.
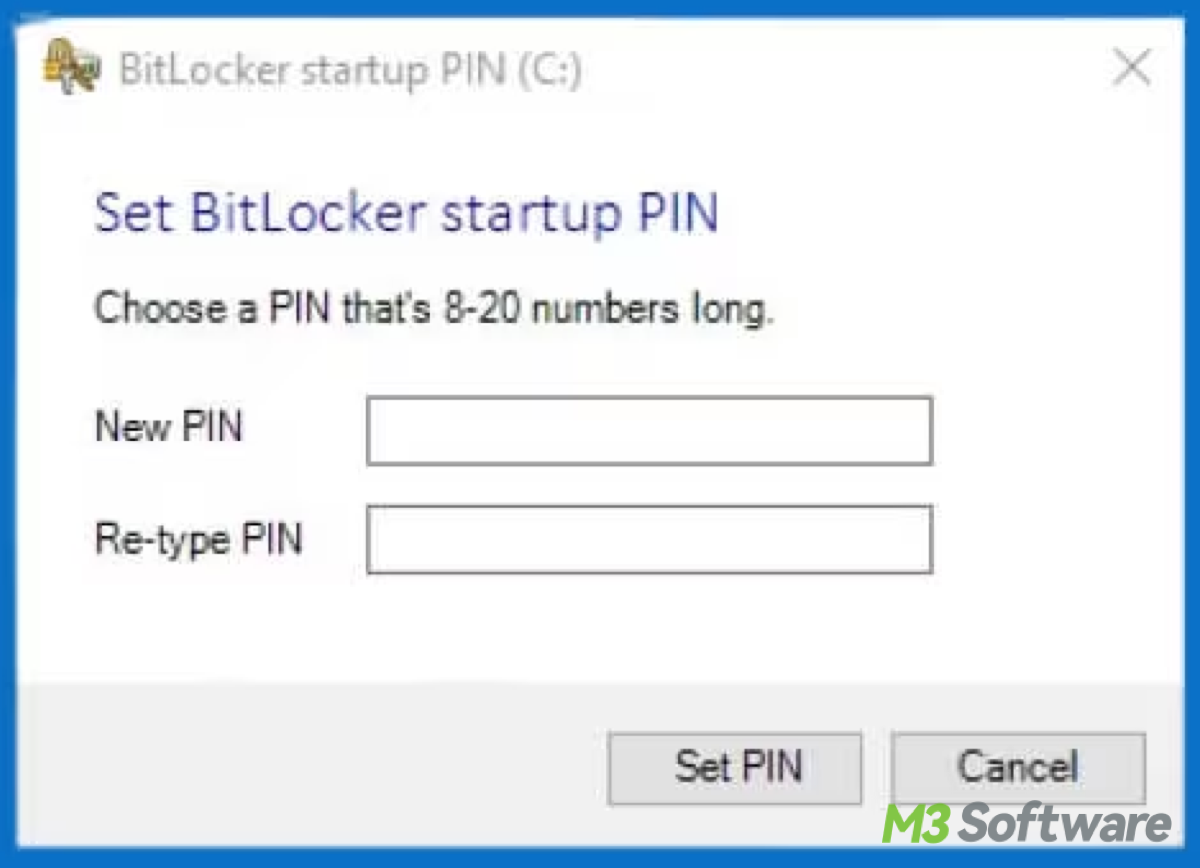
This article provides a crystal-clear description of the BitLocker PIN and how to set BitLocker PIN in three ways, how to change BitLocker PIN without old PIN.
This post introduces the BitLocker benefits and why it is so secure.
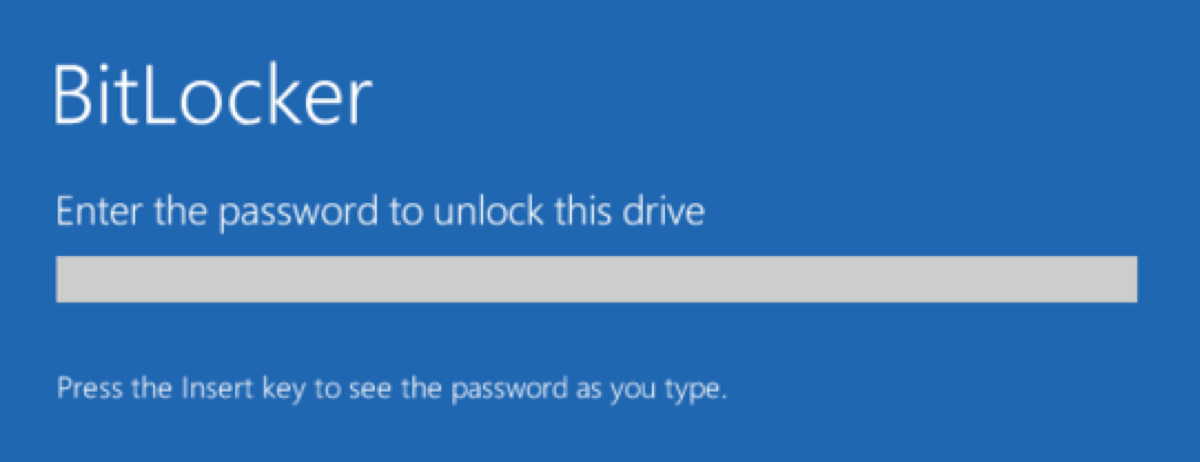
This post sheds light on the BitLocker password requirements and offers recommended practices to satisfy corresponding demands.
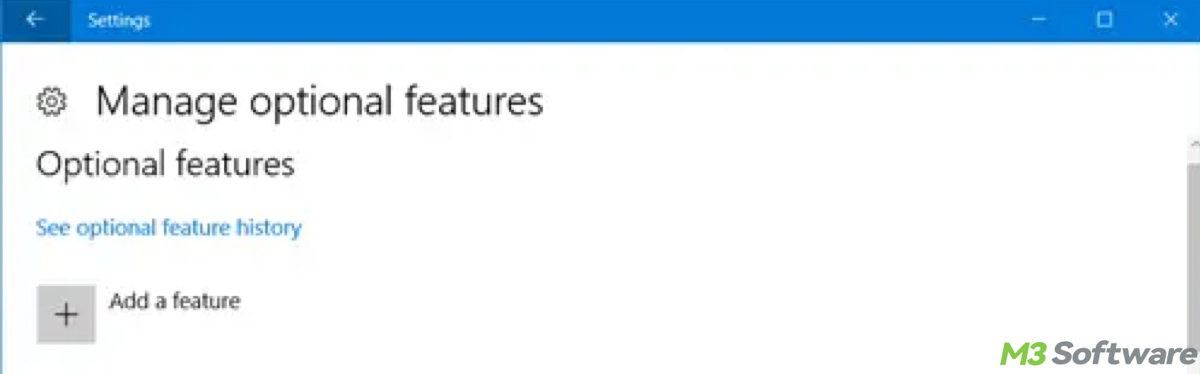
This article explores the relationship between RSAT tools, focusing on their use and installation in Windows.
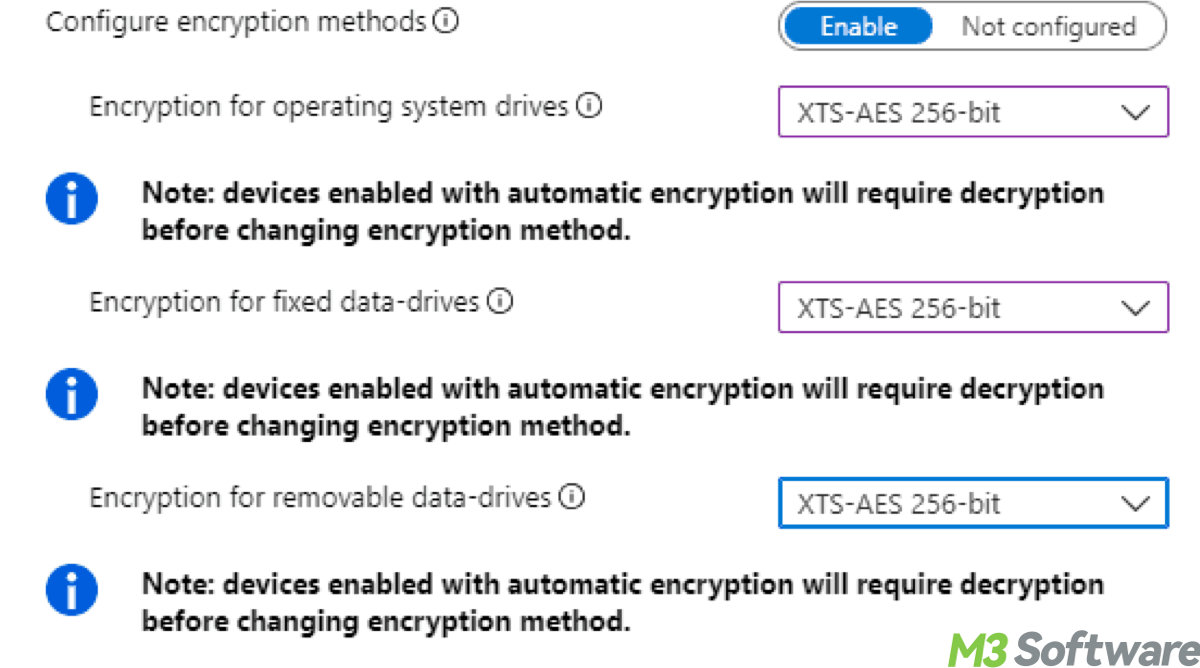
This post delves into how AES(Advanced Encryption Standard) works in BitLocker, its encryption levels, and demonstrates its strength.
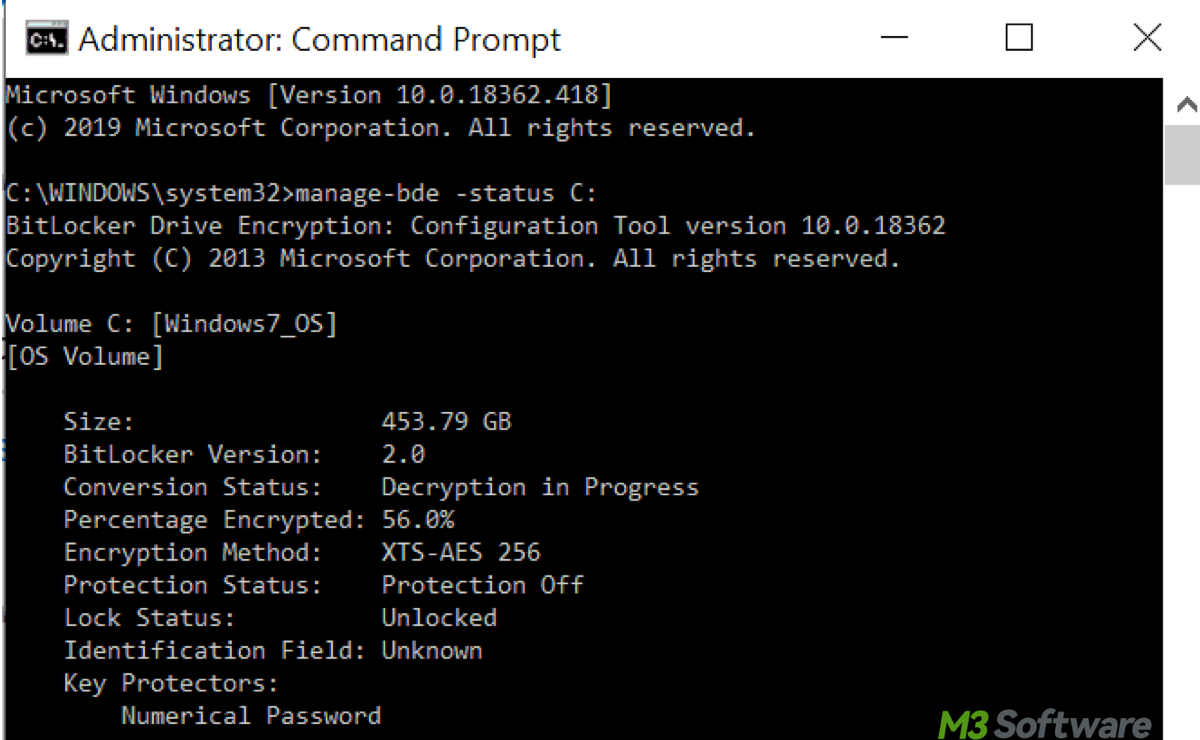
This post article deciphers how to manage BitLocker with command line, which is all about a series of Manage-bde commands. Remember that Manage-bde is the key command-line tool.
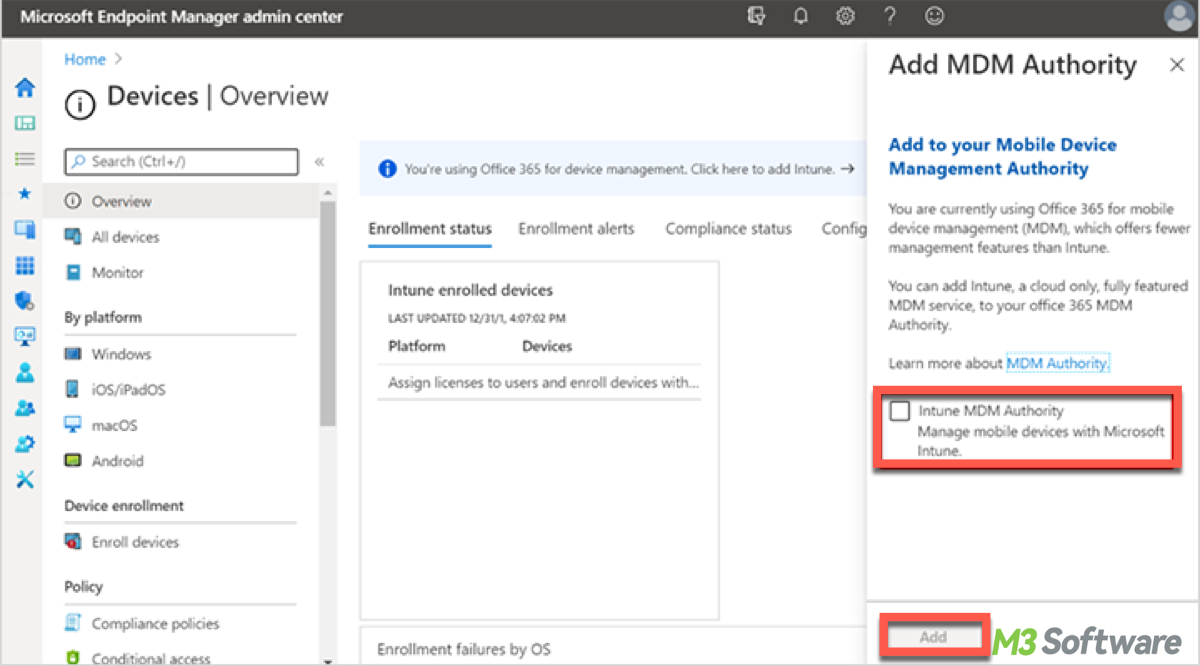
This post explores what BitLocker CSP is, its capabilities, and how it can be used to enforce encryption policies.
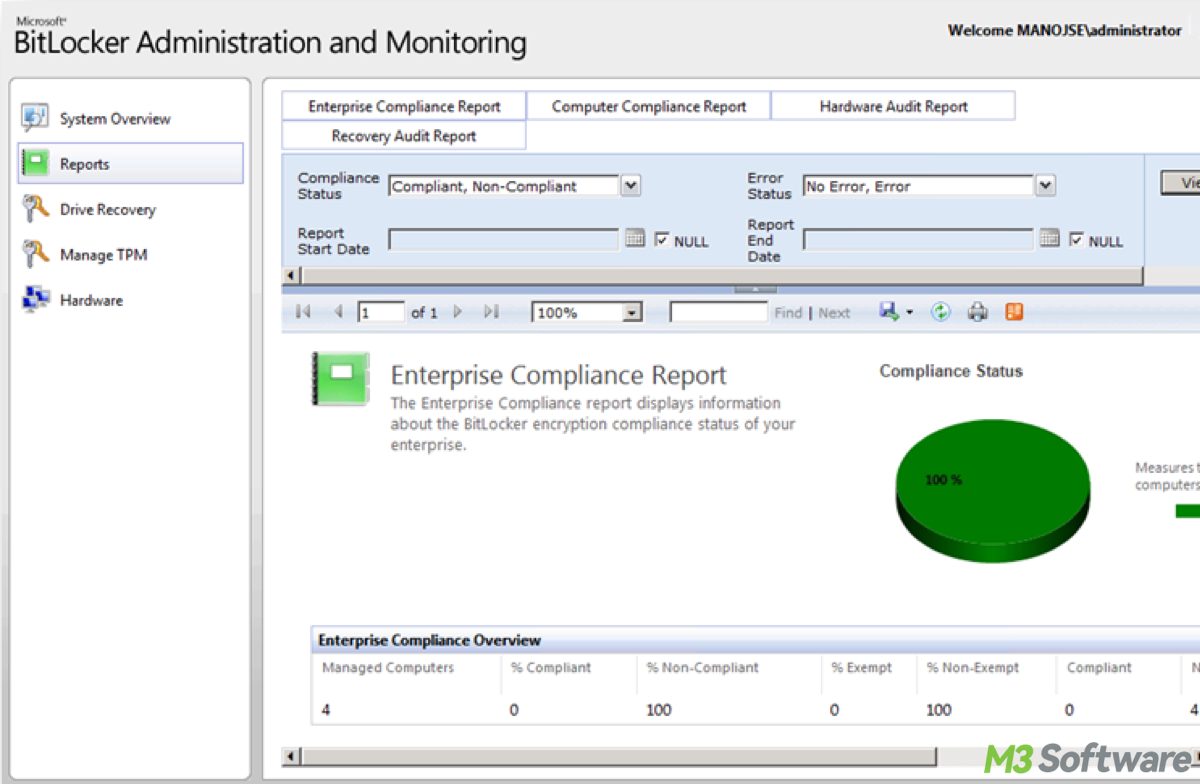
This article explains MBAM's (Microsoft BitLocker Administration and Monitoring) efficacy for BitLocker drive encryption, which avails itself of centralized management of BitLocker.
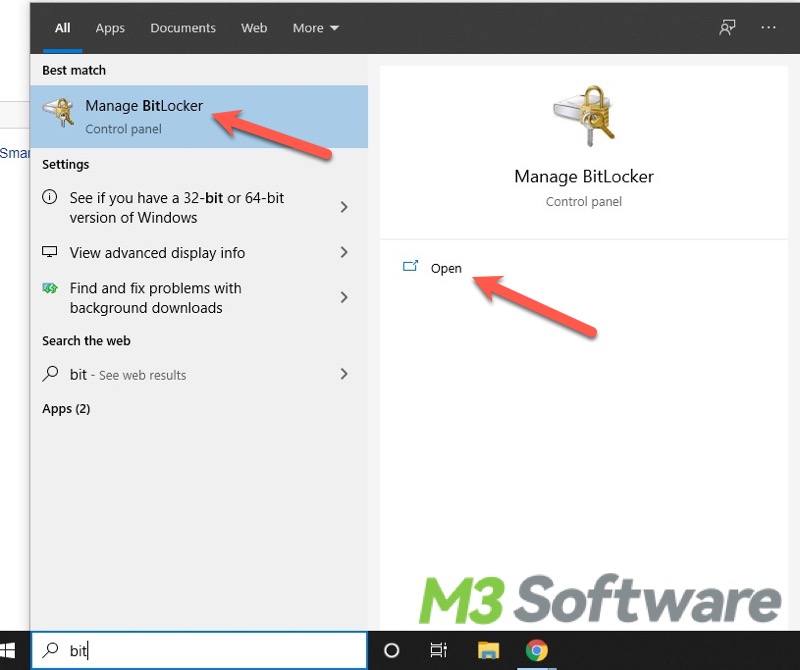
This post accounts for BitLocker Manager by definition and further guides to use it. A BitLocker Manager tool, iBoysoft DiskGeeker is involved, too.
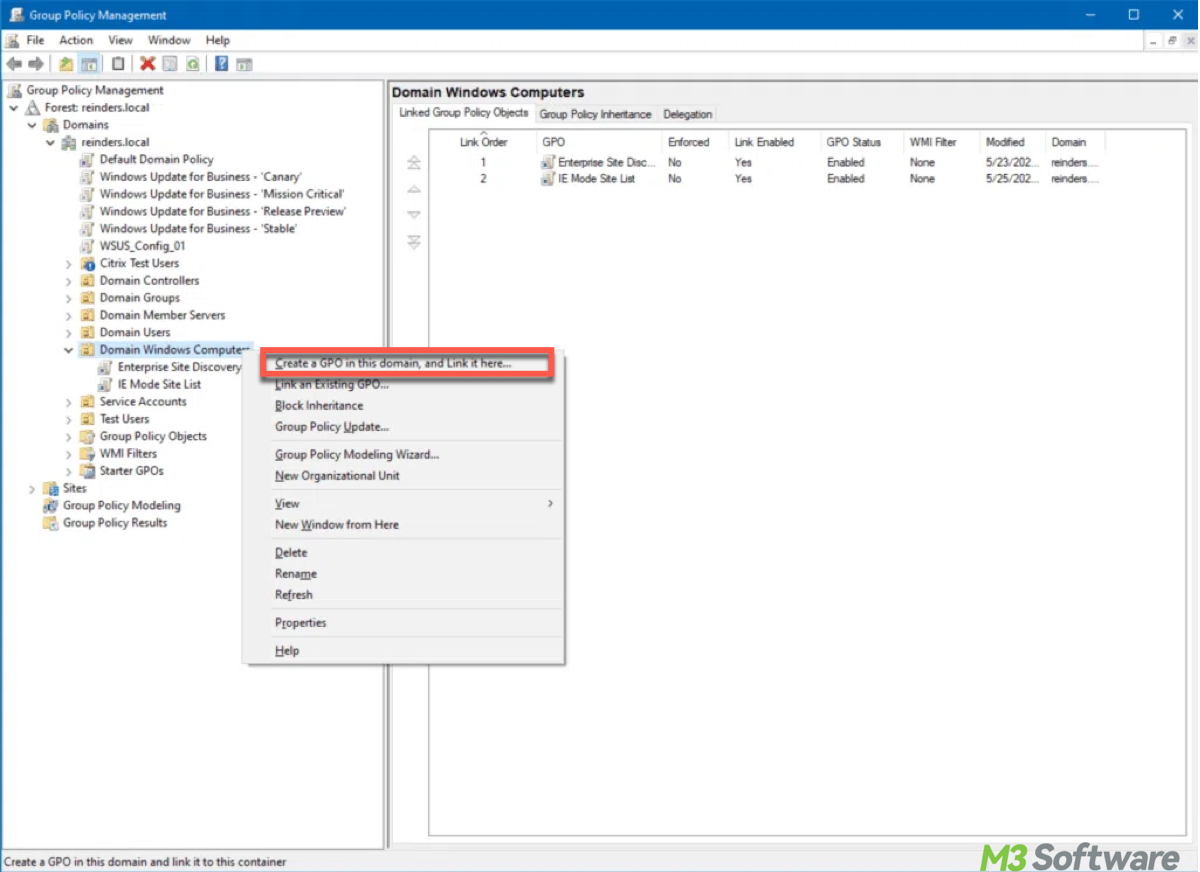
This article explains what is GPO BitLocker, especially BitLocker GPO settings. We also offer detailed tutorials to configure GPO, turn on or disable BitLocker via GPO, and so on.
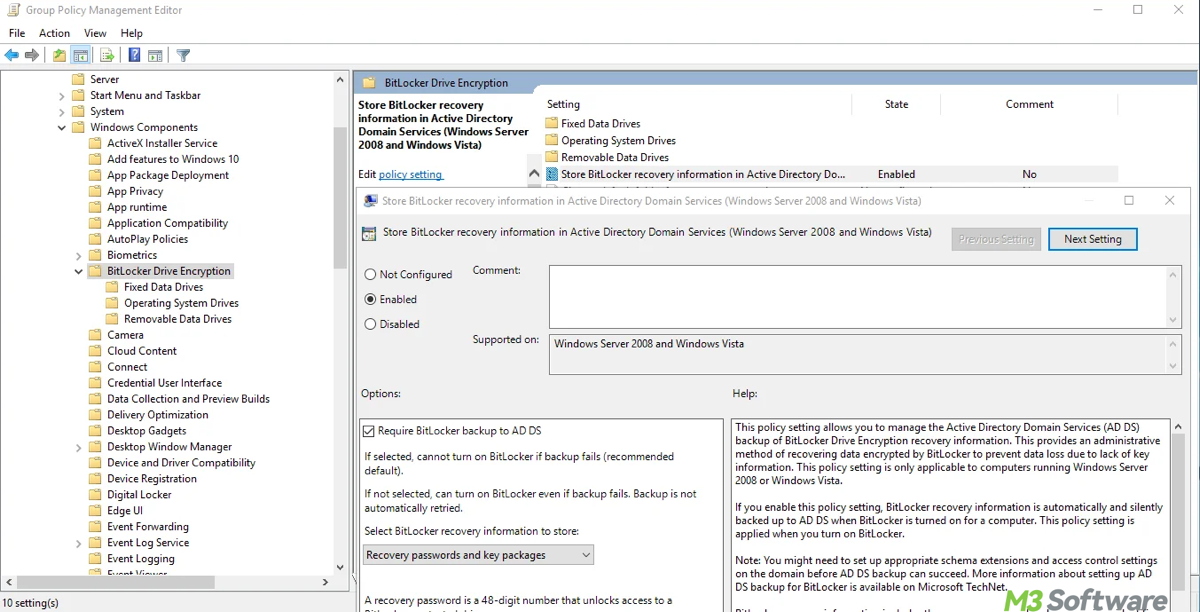
This article guides you through BitLocker key rotation, including how it works, the Group Policy settings involved, how to use PowerShell to manage keys, and how to automate the process using Intune
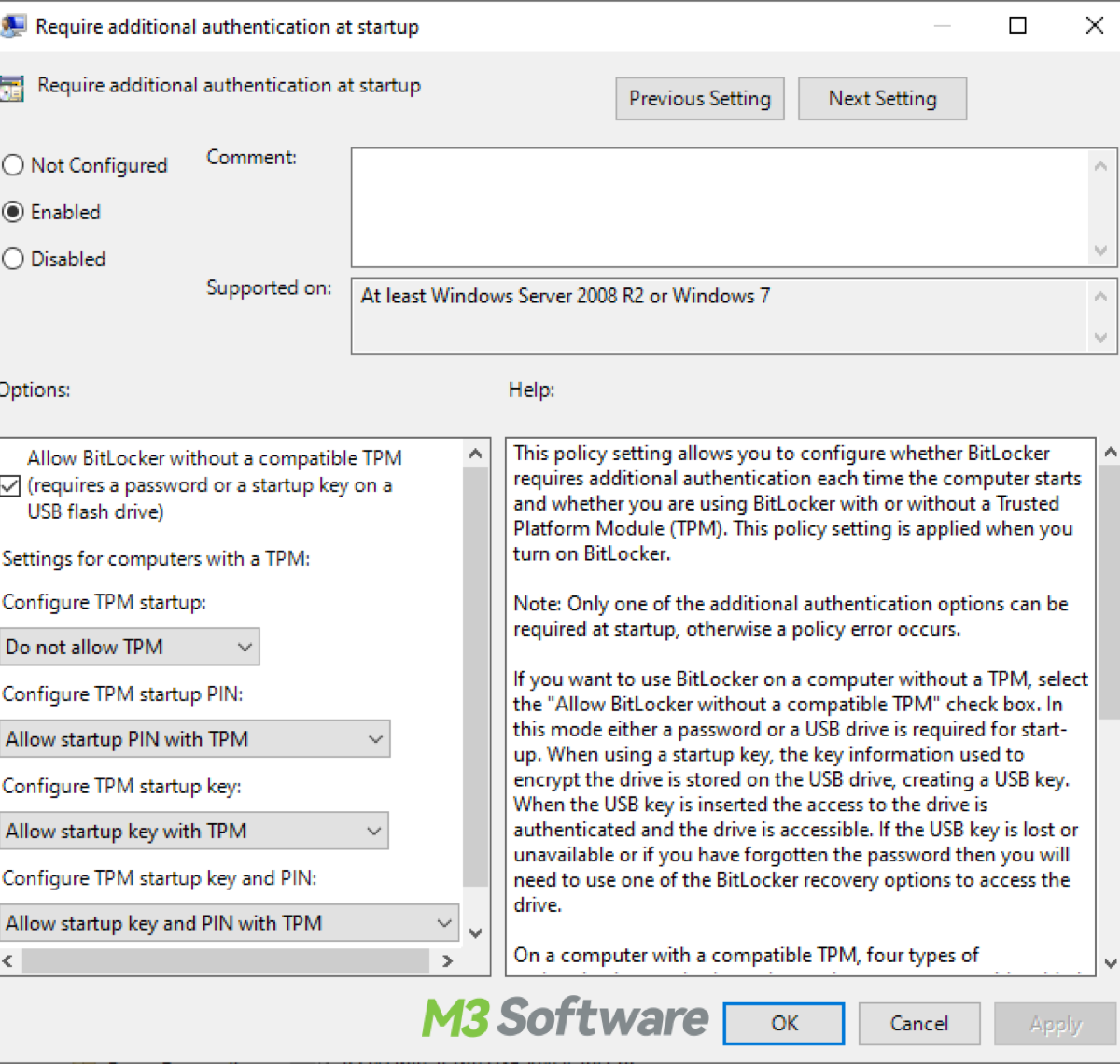
This post explains BitLocker pre-boot authentication by definition and offers guides on how to enable, configure, and disable BitLocker pre-boot authentication.
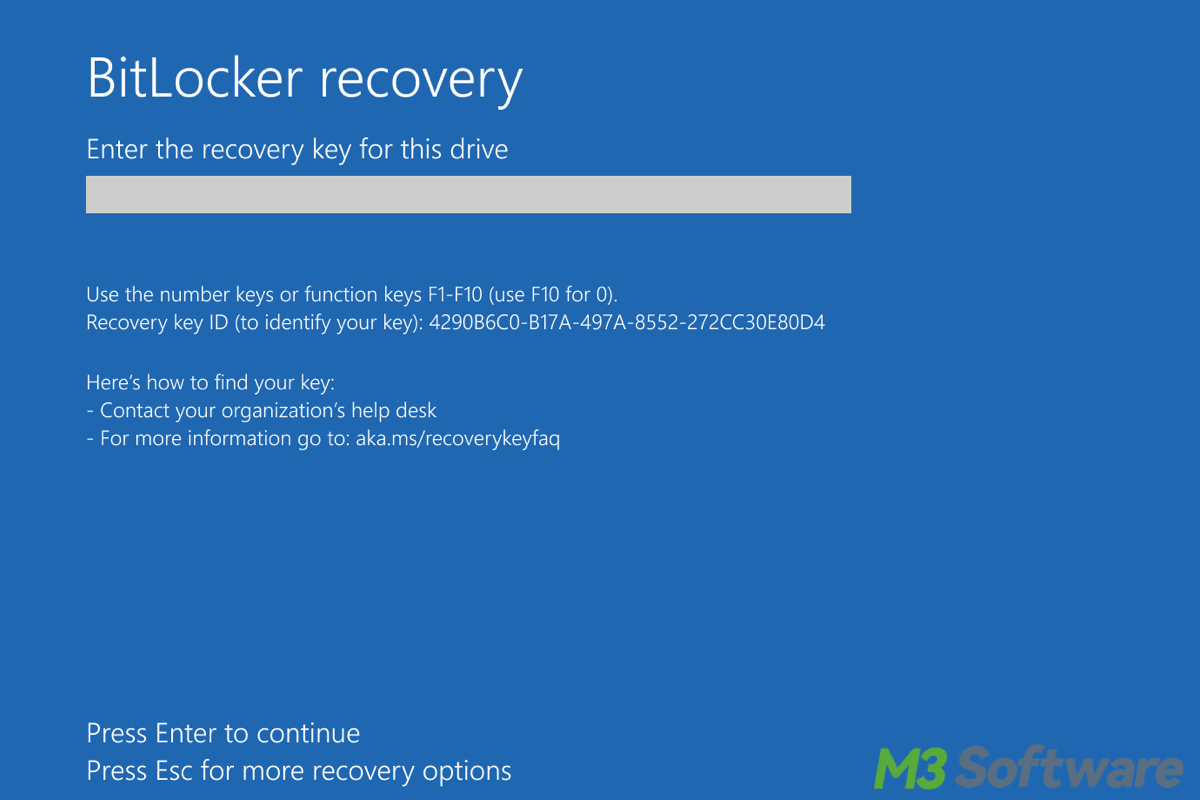
This post mystifies what services the Windows BitLocker feature provide including disk encryption and so forth, plus how to take advantage of them in real-life practice.
This post differentiates BitLocker from Antivirus. These two tools' distinctions, roles, and interrelationships help you make informed security decisions.

In this article, we'll discuss why Bitlocker may automatically encrypt your SSD, its impact on SSD performance and lifespan, and how to fix issues when your SSD gets locked by Bitlocker.
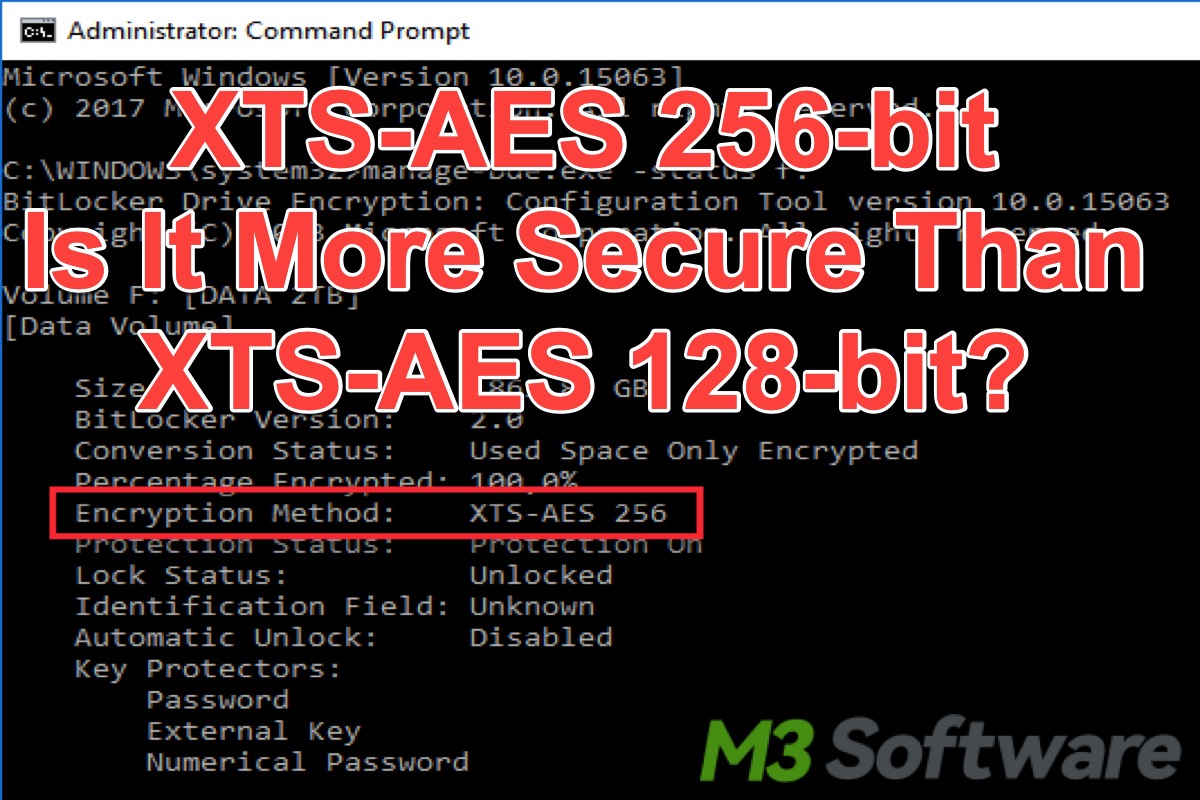
This post explains whether BitLocker AES 256 is more secure than BitLocker AES 128, and shows the steps to change BitLocker encryption method from 128 to 256.
This post discusses BitLocker and Secure Boot and whether BitLocker require Secure Boot on Windows.

This post tells you what a Local Disk D is and its main purposes in the Windows operating system. The post also shows how to clean your Local Disk D via the Disk Cleanup tool.
This article gives an overview of Local Disk C and describes the significance of it as well. The article also shows how to manage Local Disk C, including disk cleanup, storage optimization, and more.
This article relates to what Windows Update and Windows Update for Business are, and their common usage.

This post discusses some common BitLocker problems on Windows that users should be concerned about before use.

This post introduces the common BitLocker issues when you attempt to enable BitLocker or while you are using BitLocker.
A brief introduction to Hibernation Mode on Windows, including the differences between it and Sleep Mode, how to enable and disable it on Windows.

This post shows how to enable the BitLocker smart card option, which can enable you to unlock the BitLocker encrypted drive with a smart card.

This post discusses what the BitLocker To Go is and how to use BitLocker To Go on Windows.
This post discusses BitLocker virus and how ransomware related to BitLocker drive encryption feature work.
This post explains what BitLocker startup key is and shows how to enable it on Windows computer.

This post explains what BitLocker auto unlock is and how BitLocker auto unlock works in Windows operating system. It also shows how to turn on auto unlock BitLocker.
This post explains what BitLocker recovery blue screen is and what may cause the blue screen to show up frequently.
This post talks about the connection between BitLocker and TPM chip and explains how TPM works with BitLocker.

This post briefly explains what the BitLocker is and how BitLocker works on Windows. It mainly discusses the pros and cons of BitLocker and the primary way to turn it on.
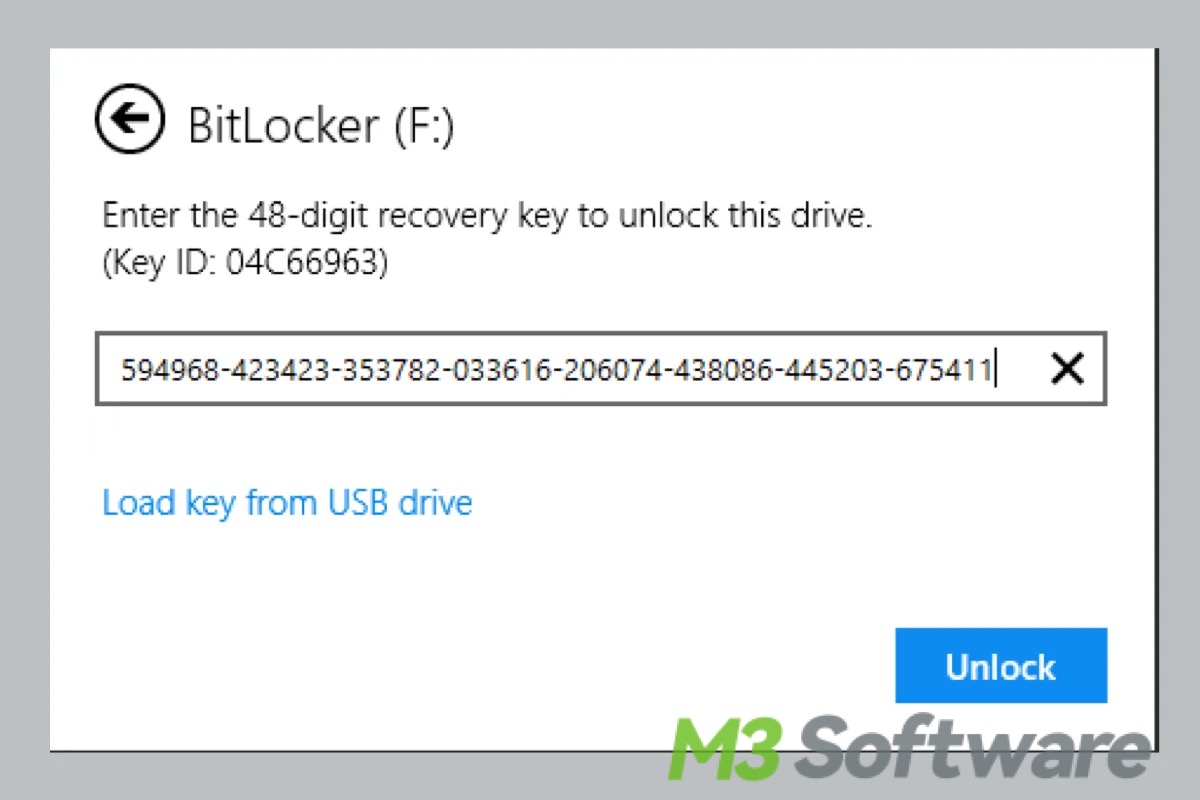
This post introduces what and how long the BitLocker recovery key is on Windows. Other frequently asked questions related to BitLocker recovery key are also involved.
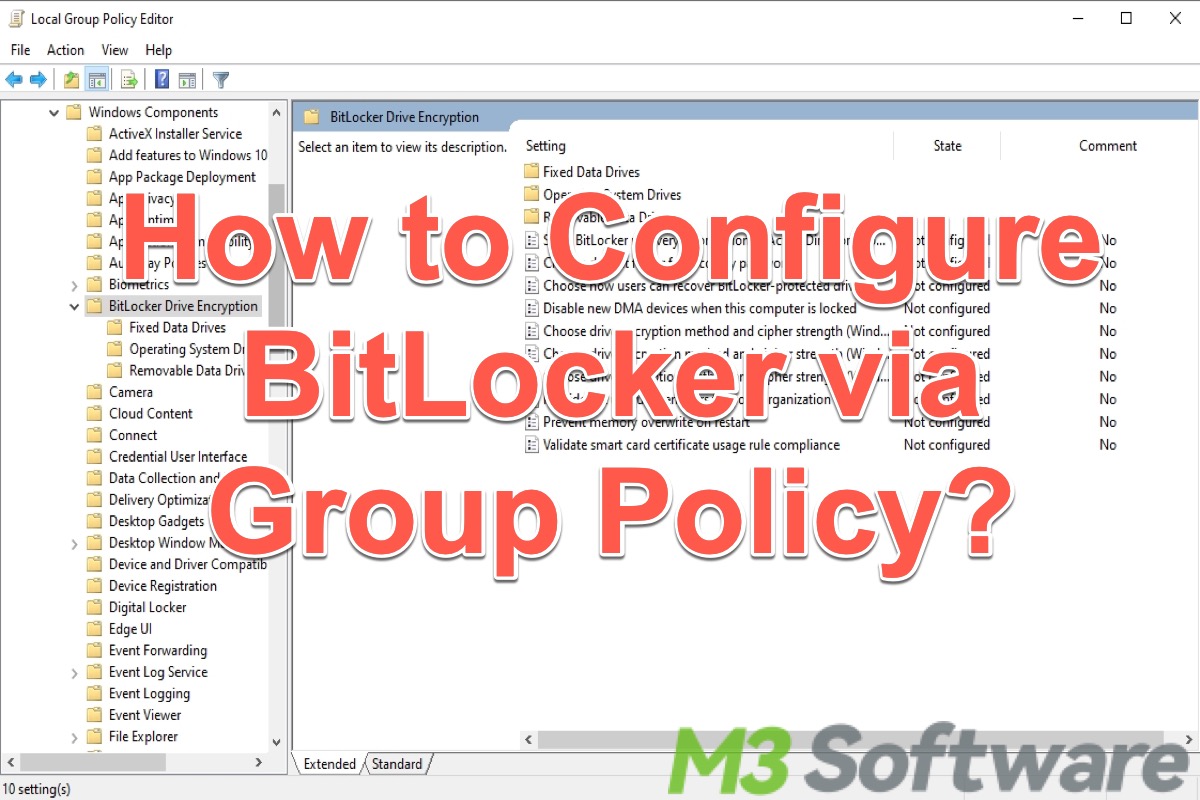
This article explains what Group Policy is on Windows and how to deploy BitLocker with Group Policy.
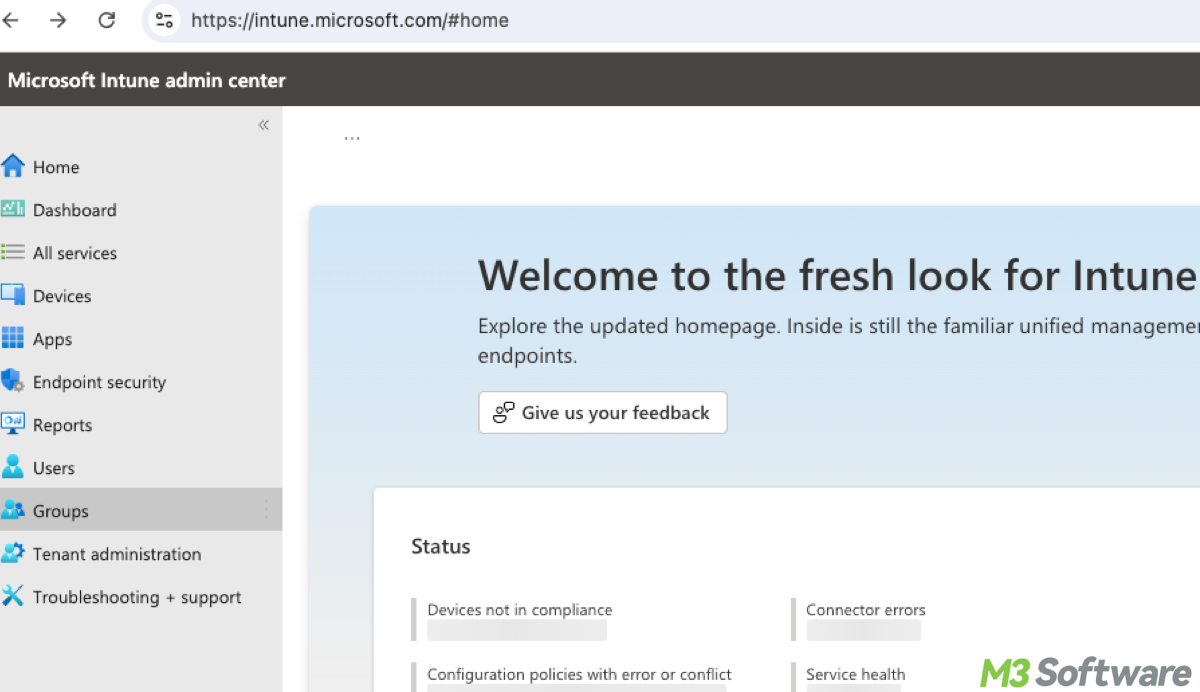
This post offers a lucid definition of Intune BitLocker and elucidates Intune BitLocker best practices including managing Intune BitLocker policy and Intune BitLocker recovery key.

This post explains what BitLocker Password is and its difference from BitLocker Recovery Key. As well as how to set up or change BitLocker Password in practice.
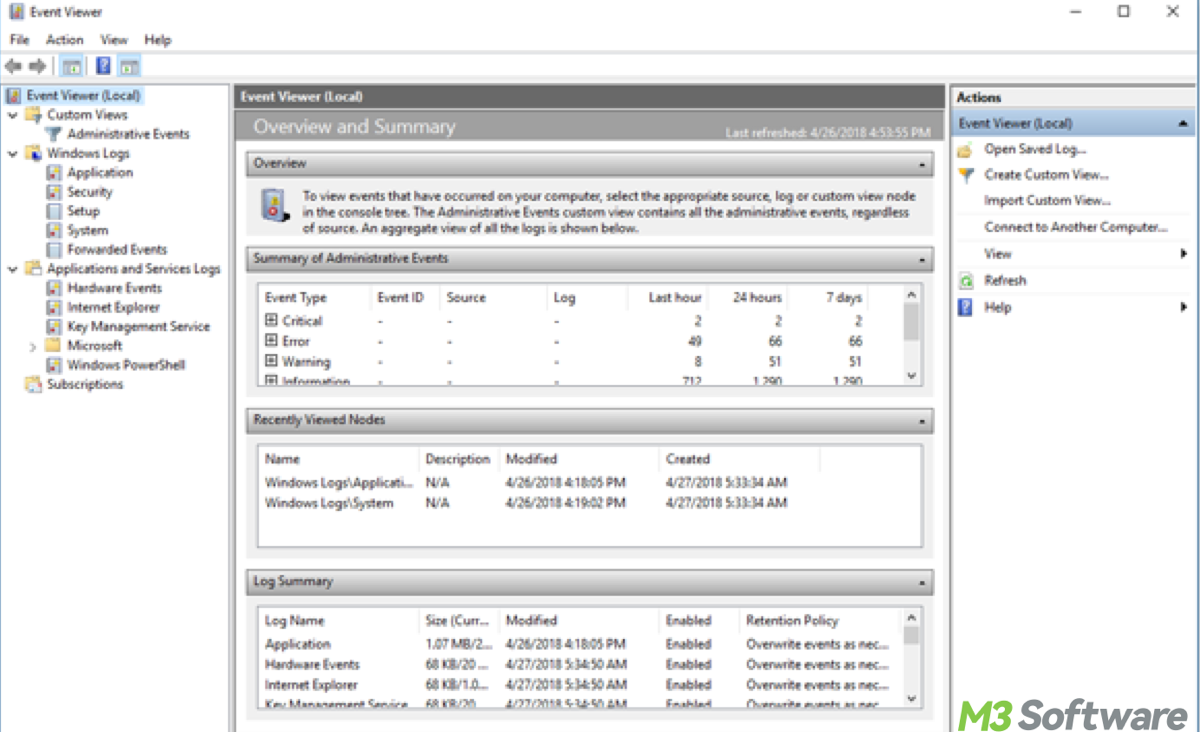
This post provides a concrete explanation of Event Viewer, the purpose or benefits of using Event Viewer, and how to use it in practice in depth. You can also spot common Event Viewer commands here.
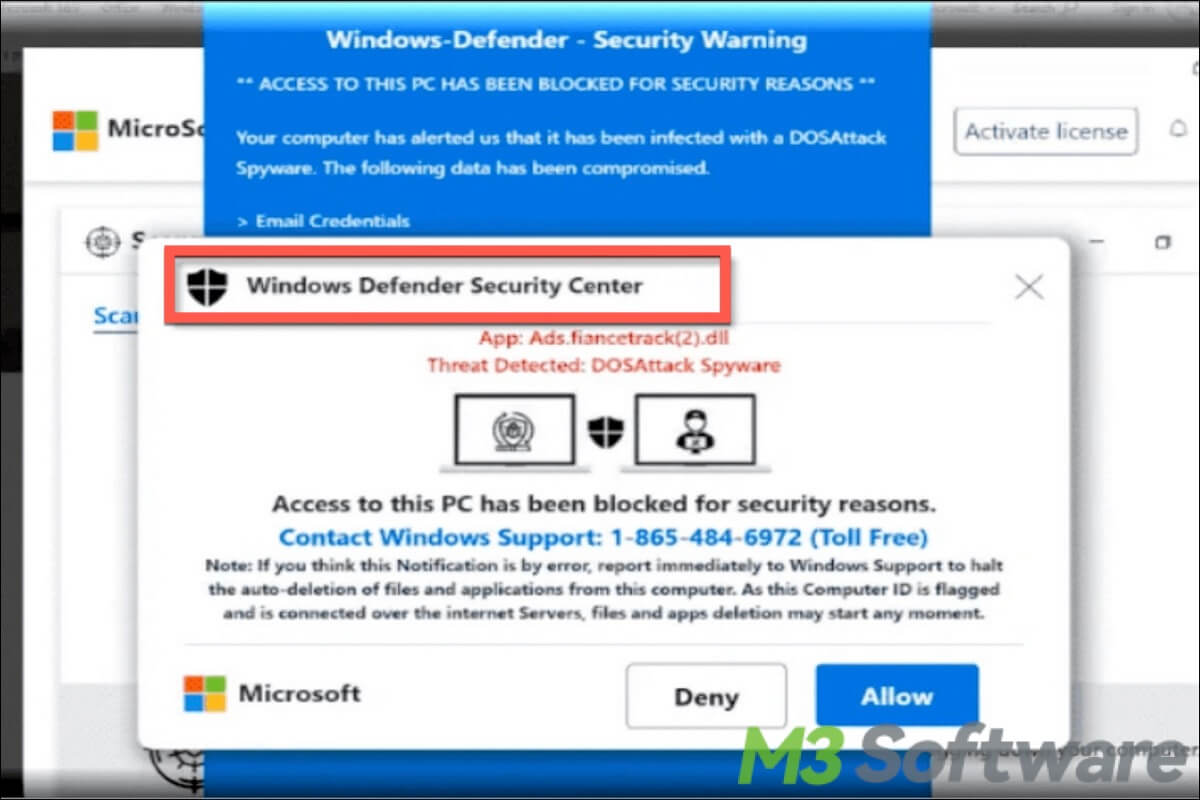
This article explains Windows Defender Security Warning scam, and also shows how to remove Windows Defender Security Warning scam with different ways.
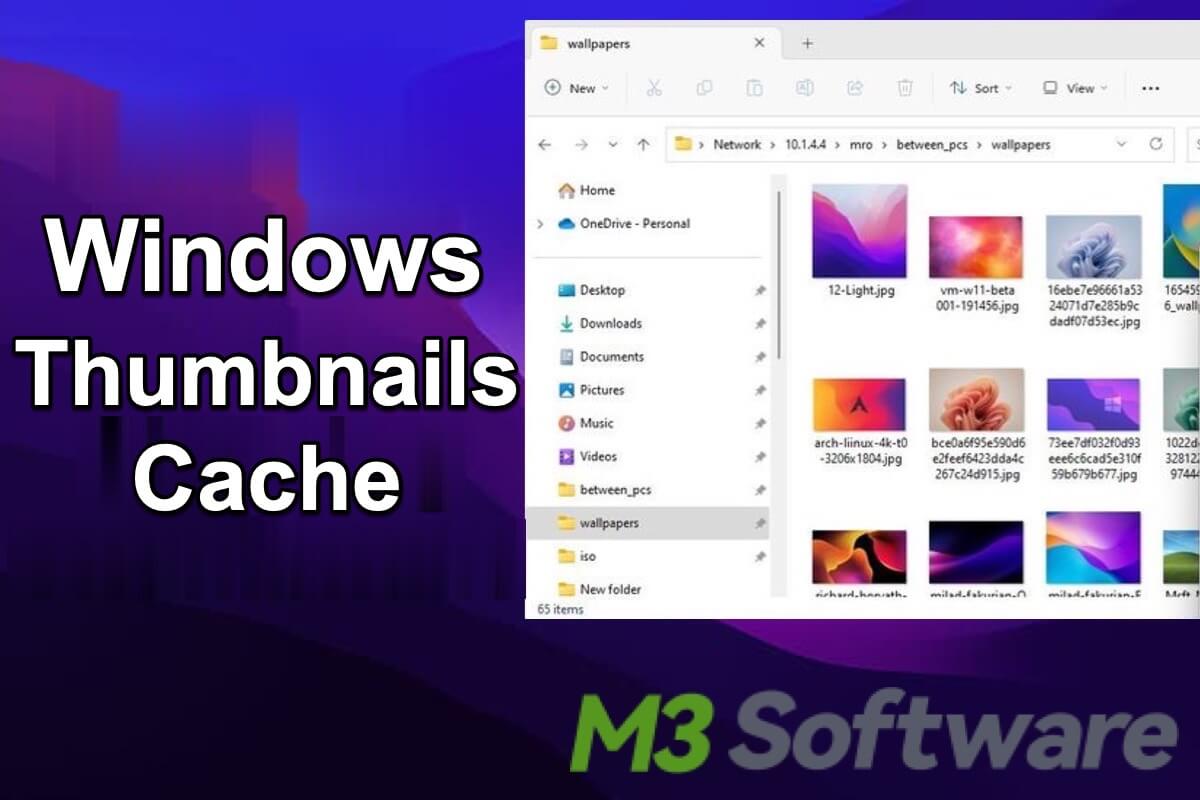
This article explains Windows Thumbnail Cache and shows how to clear Windows Thumbnail Cache Windows 10.
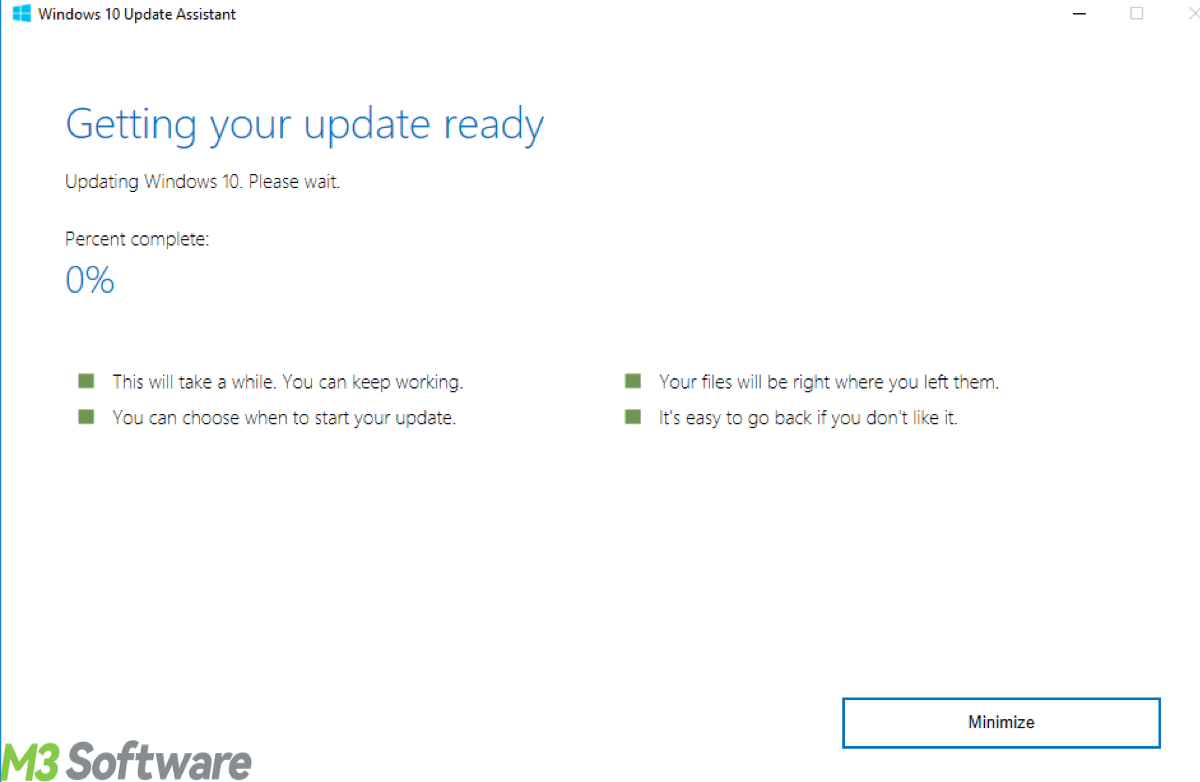
This post imparts to readers what Windows Update Assistant is and how to solve Windows Update Assistant stuck at 0 installing or 99 installing.
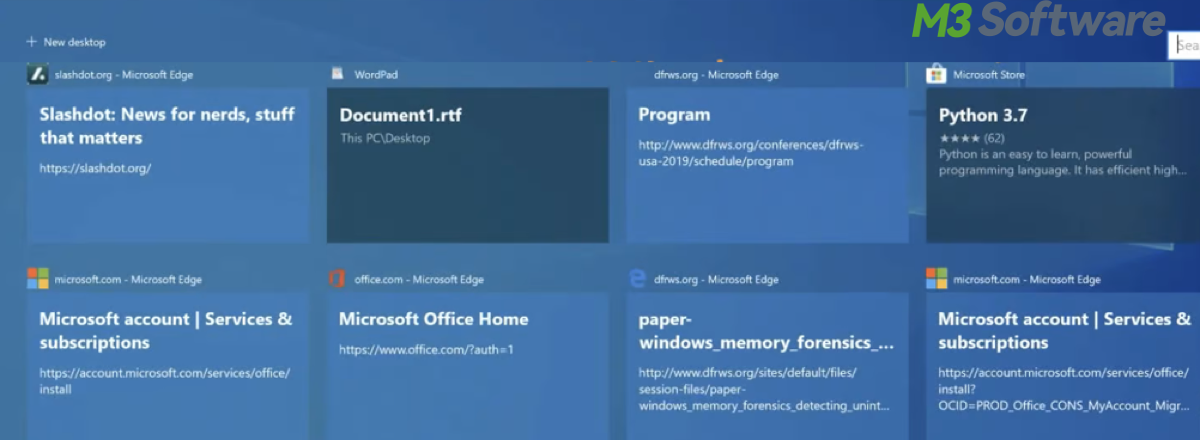
This post clarifies what is Windows Timeline and how to put it into practice especially using Windows Timeline history.
This post gives an account of the Start Menu and its recommended efficient usage.
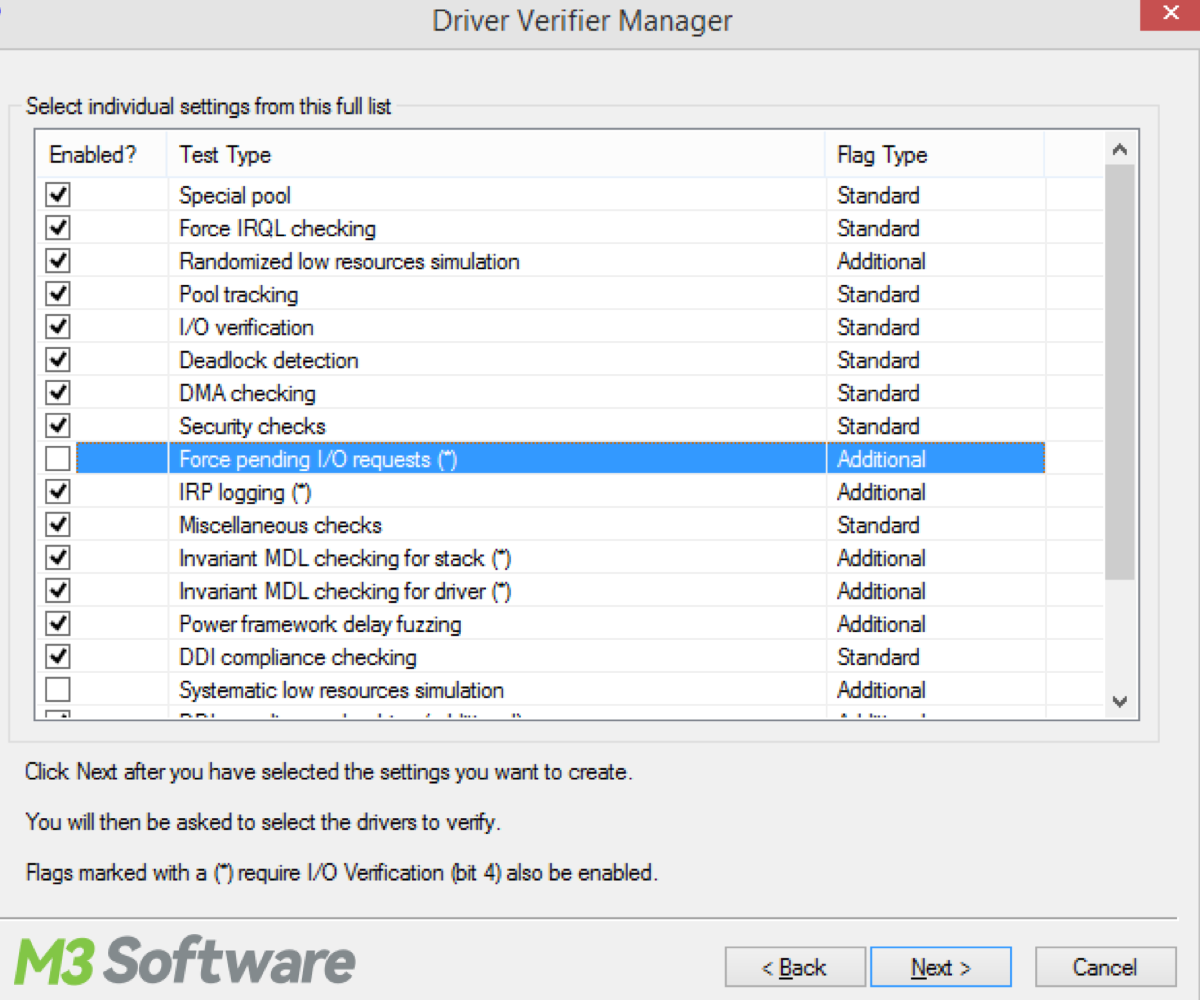
This post elaborates on what is Driver Verifier in Windows, how to use it exactly and how to solve the DMA violation error.
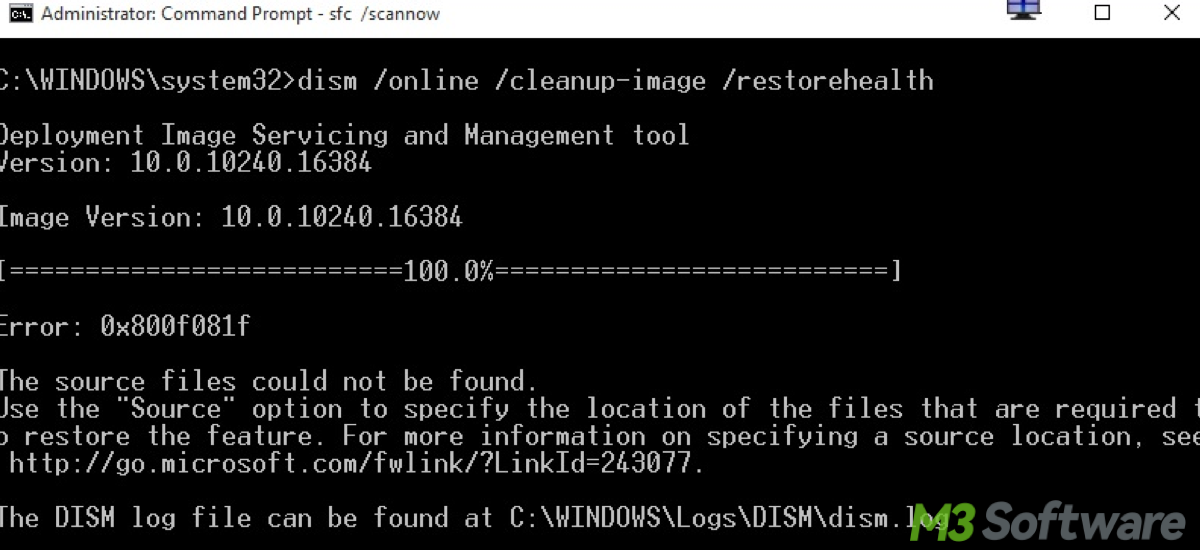
This post interprets what DISM is in Windows and its common usage including image cleanup and system file repair.
This article explains what Windows Disk Management is and what it can do in Windows operating system, and it also shows how to open Disk Management on Windows.

This article explains what the Windows File Explorer is and shows you how to open Windows File Explorer. Useful tips for using Windows File Explorer is particularly mentioned in this post.

This article briefly interprets what Fast Startup is on Windows 10 and shows how to disable Windows 10 Fast Startup in detail.

This article briefly explains the definition of Windows BitLocker and provides ways to turn off BitLocker on Windows