Written by
Yuri ZhangSummary: This post offers a lucid definition of Intune BitLocker and elucidates Intune BitLocker best practices including managing Intune BitLocker policy and Intune BitLocker recovery key.
Have you ever used Intune? Intune can do lots of things such as remote management beyond BitLocker. There is a doubt that since I own BitLocker, why should I involve Intune BitLocker?
Using BitLocker through Microsoft Intune offers several advantages over managing BitLocker manually or without a centralized management solution. Here are some reasons why integrating BitLocker with Intune can be beneficial like comprehensive reporting and auditing, as well as integration with broader endpoint management. Now let's get more details about Intune BitLocker.
What is Intune BitLocker
Microsoft Intune is a cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM). It is part of Microsoft's Enterprise Mobility + Security (EMS) suite and is designed to help organizations manage the devices employees use to access company data, ensuring security and compliance while providing a seamless user experience.
BitLocker is a full-disk encryption feature included with Microsoft Windows designed to protect data by providing encryption for entire volumes. Relating "Intune" and "BitLocker" refers to using Microsoft Intune to manage and enforce BitLocker encryption policies on devices within an organization.
The features of Intune BitLocker
Here's what this combination typically means, Intune provides IT administrators with the ability to manage BitLocker encryption across all devices in an organization from a single console. This includes deploying encryption policies, monitoring compliance, and managing recovery keys.
Using Intune, organizations can create and enforce BitLocker policies to ensure that all devices meet specific security requirements, such as requiring encryption on all corporate-owned devices or ensuring that removable drives are encrypted with BitLocker To Go.
Intune simplifies the process of managing BitLocker recovery keys. Administrators can store and access these keys centrally, which helps in situations where users forget their passwords or when devices need to be recovered after hardware changes.
Intune provides reporting and auditing capabilities to ensure that devices are compliant with BitLocker policies. This helps organizations identify and remediate non-compliant devices quickly. Intune, combined with Azure Active Directory, allows for conditional access policies that ensure only compliant, encrypted devices can access corporate resources.
By leveraging Intune to manage BitLocker, organizations can enhance their security posture by ensuring that all devices are properly encrypted and that encryption keys are securely managed. This integration streamlines the deployment and management of BitLocker, making it easier to enforce security policies and protect sensitive data.
Share this post to gain more cyber-interaction with others.
How to use Intune to manage BitLocker encryption
Use Intune to manage BitLocker or enable BitLocker Intune involves several steps to configure policies, deploy them to devices, and monitor compliance. //Steps to use Intune with BitLocker
Step 1. Prerequisites to use Intune BitLocker
Your devices should be Azure AD or hybrid Azure AD-joined. Ans ensure devices are enrolled in Intune. This can be done automatically for Azure AD-joined devices or manually by users. Also ensure the devices support BitLocker and meet hardware requirements, such as having a TPM (Trusted Platform Module) chip.
Step 2. Configure Intune BitLocker policies
Creating and managing a BitLocker policy using Microsoft Intune involves defining specific settings to control how BitLocker encryption is applied to devices within your organization. Here's a detailed guide on how to create a BitLocker policy in Intune.
- Sign in to the Intune portal by going to the Microsoft Endpoint Manager admin center: https://endpoint.microsoft.com.
- Create a device configuration profile by navigating to Devices > Configuration profiles > Create profile.
- Select profile settings, specifically select Windows 10 and later for the platform, and select Templates > Endpoint protection for the profile type.
- In the Configuration settings section, expand Windows Encryption.
- Configure the necessary BitLocker settings, such as enabling BitLocker, setting encryption methods, and specifying key recovery options.
- Example settings include as follows:Encrypt storage: Choose between "Require" or "Not configured."
BitLocker base settings: Specify whether to require a startup PIN or use a TPM.
Fixed data-drive settings: Configure settings for BitLocker To Go.
OS drive settings: Define settings for the operating system drive encryption.
Recovery options: Specify how recovery keys are backed up. - Click Assignments. Assign the BitLocker profile to user groups or device groups in your organization, click Next and then Create to finalize the profile.
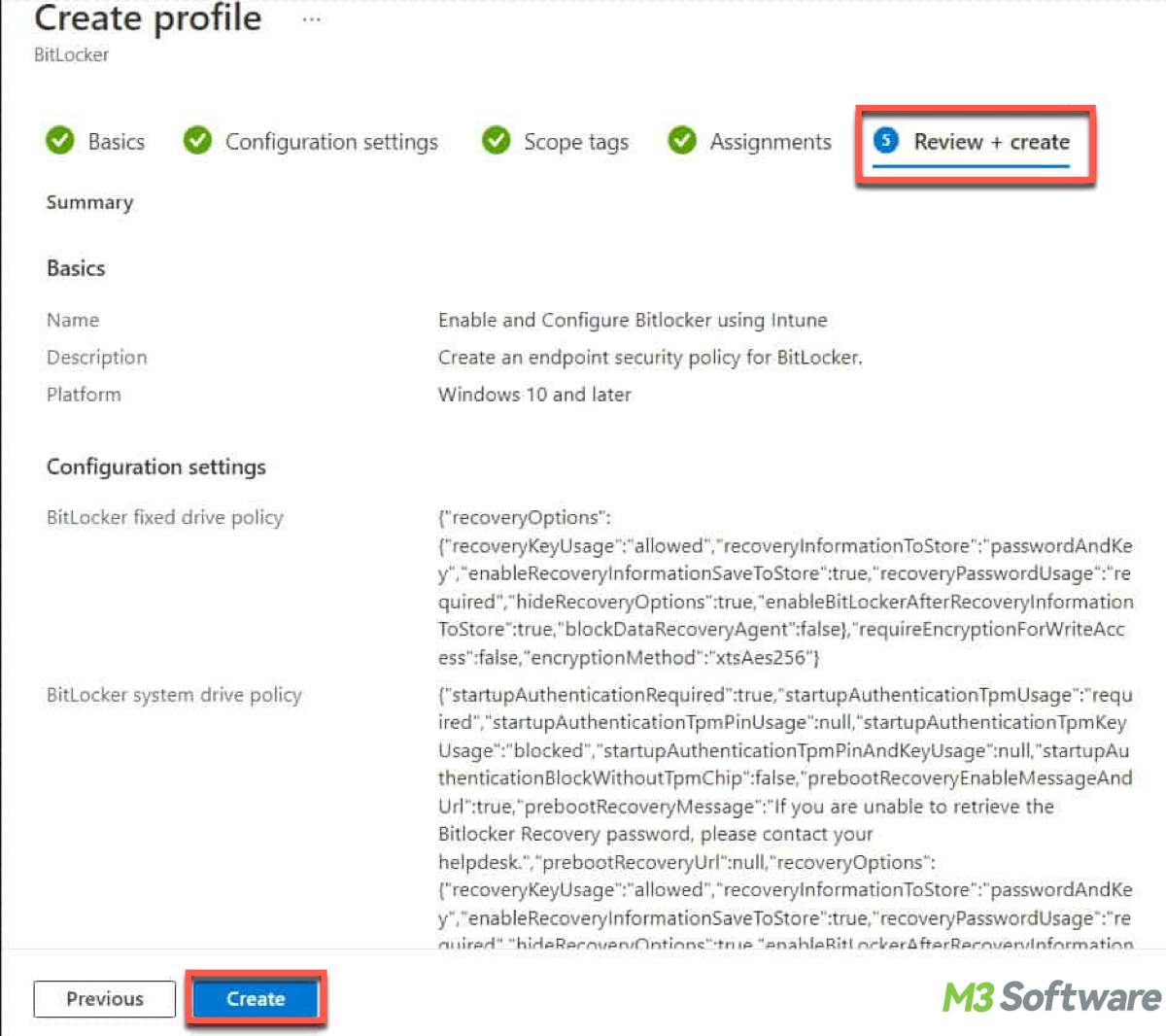
Note: Once devices are enrolled and assigned the BitLocker policy, the encryption settings are automatically applied. Users may need to restart their devices for the policy to take effect.
Step 3. Monitor BitLocker compliance and Recovery Key
By monitoring BitLocker compliance and recovery keys with Intune, organizations can maintain a strong security posture, protect sensitive data, streamline IT operations, and ensure compliance with security policies and regulations. This proactive approach helps mitigate risks and enhances overall data protection, and it is where the phrase “Intune BitLocker recovery key” comes from.
- In the Endpoint Manager, navigate to Devices > Monitor > Encryption report to view the status of BitLocker encryption on managed devices, this report provides details on encryption compliance, allowing you to identify any non-compliant devices.
- To manage the Intune BitLocker recovery key, navigate to Devices > All devices and select a specific device. Then view the Recovery keys section to manage and retrieve BitLocker recovery keys for that device.
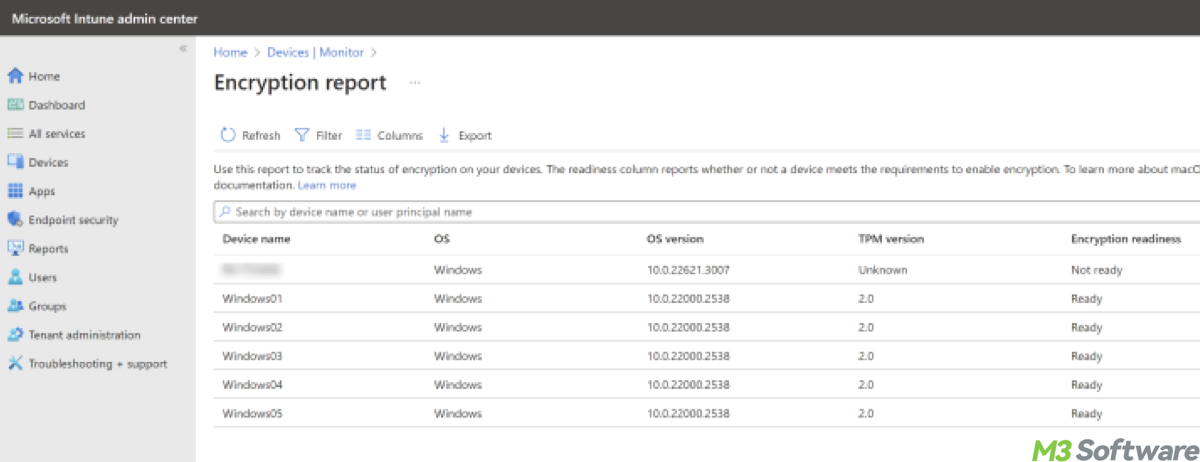
Tips: Remember to continuously monitor encryption reports to ensure all devices comply with organizational policies. And as security requirements change, update BitLocker policies in Intune and reapply them to ensure devices remain secure.
Share this post so that you and others can effectively use Intune to manage BitLocker encryption, enhancing the security of your organization's devices and data.
