Written by
Wilsey YoungSummary: This post briefly discusses Group Policy on Windows and shows what BitLocker-related changes you can make in Group Policy. It's also a step-by-step guide on how to configure BitLocker Group Policy.
BitLocker, in general, can be set up and configured through File Explorer, BitLocker Drive Encryption panel, or the Command Prompt tool on Windows. Few people know about BitLocker Group Policy and there are various and personalized settings for you to configure BitLocker to enhance security and personalize encryption.
In this guide, we briefly introduce the Group Policy feature on Windows and we also discuss what changes you can make to BitLocker via Group Policy.
You can share this post and tell your friends how to configure BitLocker Group Policy!
What is Group Policy on Windows?
Group Policy is a feature included in Windows. It allows administrators to manage and configure operating systems, applications, and user settings in an Active Directory environment. In other words, Group Policy empowers administrators to enforce policies on a wide range of settings, ensuring secure configurations across all computers in the domain.
You can keep reading the following contents and learn how to configure BitLocker Group Policy.
How to configure BitLocker Group Policy?
Here we show how to open Group Policy through the “Run dialog box” and configure BitLocker group policy in the Group Policy.
- Press the “Windows+R” keys to open the “Run dialog box,” type “gpedit.msc” in the box, and click “OK” or hit the “Enter” key on your keyboard.
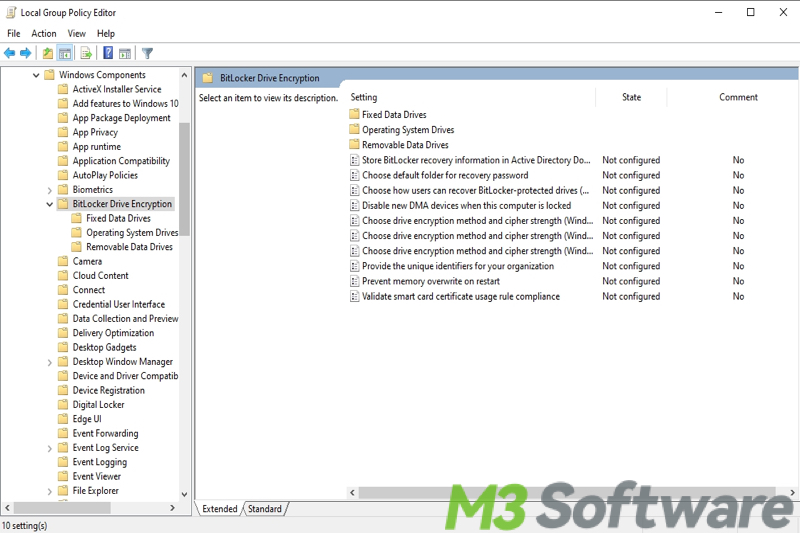
- Expand the folder on the left side panel according to the path: Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption. You will enter the page as follows
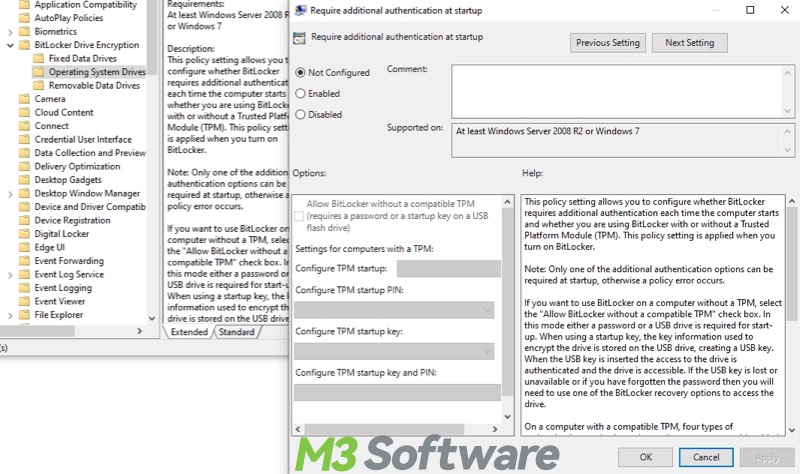
- Double-click the setting you want to configure and click “Enabled”, as shown in the picture:
- Click “Apply” and “OK” to let the modification take effect.
What can we configure for BitLocker via Group Policy?
You can enhance security and manage encryption behavior by configuring BitLocker in versatile settings provided by Group Policy. Here we list some interesting and practical BitLocker Group Policy settings that may arouse your interest.
Require additional authentication at startup
This BitLocker Group Policy setting decides whether BitLocker requires additional authentication each time the computer boots up.
- Follow the steps above to open the Local Group Policy Editor
- Follow the path to expand the folder and double-click the setting item at last: Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives > Require additional authentication at startup.

- Click “Enabled” and adjust the settings in the “Options” section.
- Click “Apply” and “OK.”
Configure minimum PIN length for startup
This BitLocker Group Policy setting means you can adjust the minimum length for a TPM startup PIN (from a minimum length of 4 digits to a maximum length of 20 digits).
- Follow the path to expand the folder and double-click the setting item at last: Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives > Configure minimum PIN length for startup.
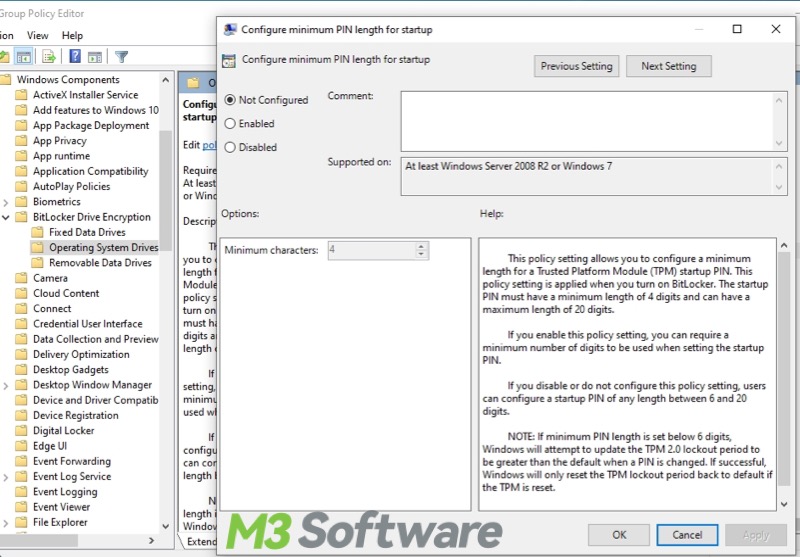
- Switch to “Enabled,” and adjust the minimum characters in the “Options” section.
- Click “Apply” and “OK.”
Choose drive encryption methods and cipher strength
With this BitLocker Group Policy setting, you can configure the encryption algorithm and cipher strength, aligning with your organization's security requirements.
- Go to the path: Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Choose drive encryption method and cipher strength. Note: You should notice the Windows versions this setting requires.
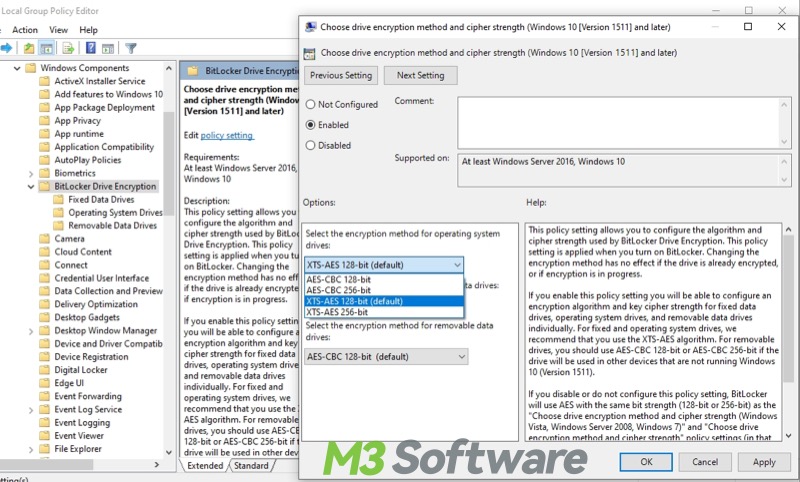
- Enable the setting and choose the encryption algorithm in the “Options” section.
- Click “Apply” and “OK.”
Deny write access to fixed drives not protected by BitLocker
When you enable this BitLocker Group Policy setting, all fixed data drives that are not protected by BitLocker will be mounted as read-only.
- Go to: Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Fixed Data Drives > Deny write access to fixed drives not protected by BitLocker.
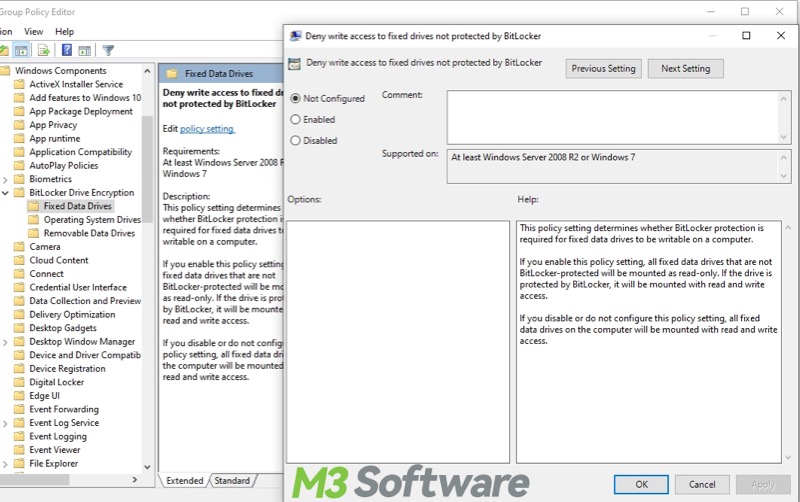
- Click “Enabled,” “Apply,” and “OK.”
Control use of BitLocker on removable drives
Removable disk drives, by default, can be encrypted by BitLocker on your PC. You can make changes to determine whether users can use BitLocker on removable disk drives.
- Policy path: Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Removable Data Drives > Control use of BitLocker on removable drives.
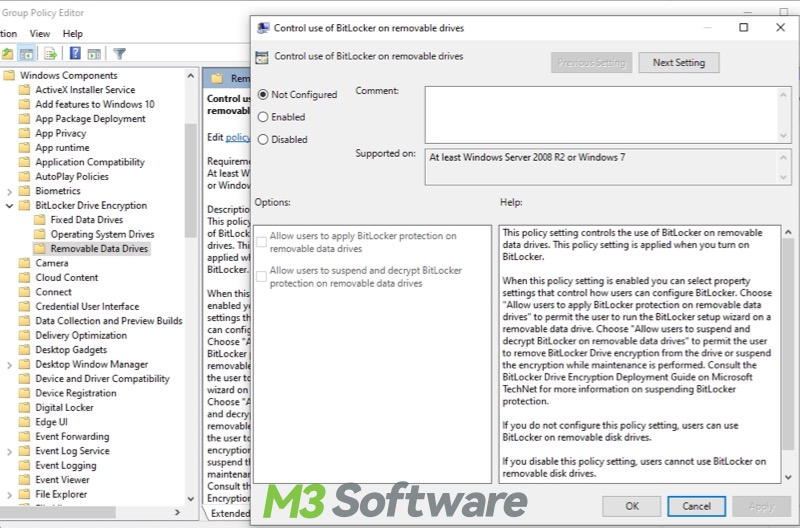
- If you disable this setting, users cannot use BitLocker on removable disk drives.
- Click “Apply” and “OK” if any changes have been made.
You can click the buttons below to share this post!
