Written by
Sherry SongSummary: Have you used Data Execution Prevention on PC? Should we turn it on or off if we feel it is unsafe? Today, let us give you a brief introduction to Data Execution Prevention, including how to use it on Windows.
Data Execution Prevention (DEP) is a critical security feature built into Windows. It is designed to prevent malicious code from executing in certain areas of system memory that are not intended to run programs or scripts.
DEP plays a vital role in protecting your system from exploits and buffer overflow attacks, which are often used by malware to gain unauthorized access or control over a computer.
In this article, we'll explore how DEP works, its different types and applications, and how users can configure or disable it when necessary.
How Data Execution Prevention works
DEP works by marking specific regions of memory as non-executable. This means that code cannot run from those marked memory segments. If a program tries to execute code from a protected area, DEP intervenes and shuts it down, thereby preventing the execution of potentially harmful code.
DEP operates in two modes:
- Hardware-enforced DEP: Utilizes the CPU's No-Execute (NX) bit feature to mark memory locations as non-executable.
- Software-enforced DEP: Provides protection for certain Windows system binaries, even on processors that do not support hardware-based DEP.
If malware tries to run shellcode injected into a program's stack, DEP immediately halts the process and triggers a system alert, preventing the attack from succeeding.
Applications, pros, and cons of DEP
Data Execution Prevention Windows is widely implemented across both personal and enterprise-level systems to reinforce overall cybersecurity. Its key applications include:
- Preventing memory-based attacks: DEP is particularly effective against buffer overflow attacks.
- Securing core system processes: DEP helps protect critical Windows services and system files from being exploited by malicious software.
- Legacy system protection: DEP adds a layer of defense to older software applications that may not have been developed with modern security practices in mind.
Let's see the advantages and disadvantages of DEP:
| Benefits | Weakness |
| Enhance security in code injection attacks | Some older apps may not support it |
| Run effectively without heavily taxing system resources | Require manual configuration if there is something wrong |
| Automatic protection | Limited protection scope |
So be careful to use it, and don't be afraid of its security; you can use it and disable it. Why not share our post?
How to set and disable Data Execution Prevention
While DEP is beneficial, some legacy or custom applications may not function properly with DEP enabled. In such cases, users might need to disable DEP on Windows:
How to configure DEP in Windows
- Open Control Panel > System and Security > System.
- Select Advanced system settings > Settings (under Performance).
- Navigate to the Data Execution Prevention tab.
- Choose: Turn on DEP for essential Windows programs and services only (OptIn) or Turn on DEP for all programs and services except those I select (OptOut).
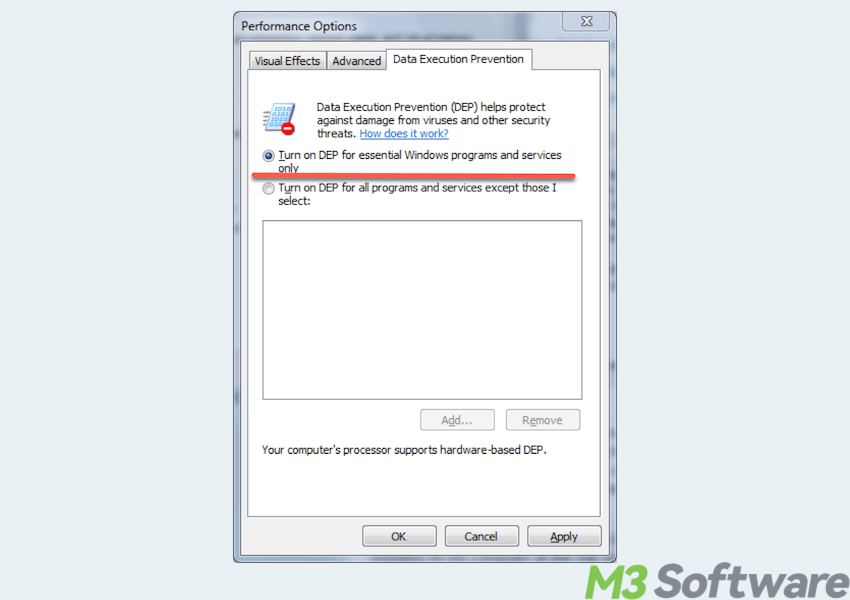
- Click Add to include programs that should be exempt from DEP.
You can open Command Prompt to enable it by: "bcdedit.exe /set {current} nx OptIn # OptIn mode" and disable it by "bcdedit.exe /set {current} nx OptOut # OptOut mode".
How to disable DEP (Not recommended)
Disabling DEP entirely is not advised due to the security risks. However, for advanced troubleshooting, this can be done via Command Prompt:
- Open Command Prompt as Administrator.
- Run “bcdedit.exe /set {current} nx AlwaysOff” and press the Enter key.
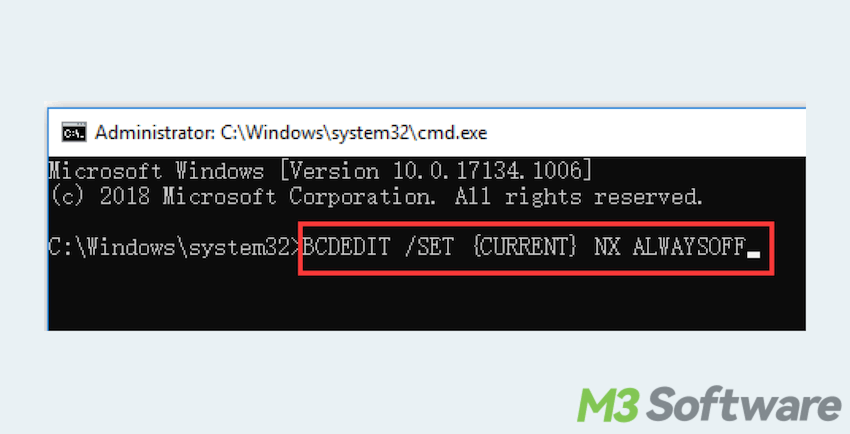
- If you regret, restart your computer, and use the command “bcdedit.exe /set {current} nx AlwaysOn”.
Please share these steps to help others.
Data Execution Prevention is a powerful tool that significantly improves the security posture of Windows systems. By preventing the execution of unauthorized code in protected memory regions, DEP reduces the risk of malware attacks and system exploitation.
While it's best to keep DEP enabled for maximum protection, users have the flexibility to configure or disable it when compatibility issues arise.
