Written by
Wilsey YoungSummary: This post gives an overview of the BitLocker virus and how BitLocker ransomware works. Most importantly, this post also shows how to find the BitLocker recovery key after your PC suffers from BitLocker ransomware attacks.
BitLocker is a special encryption tool developed by Microsoft and built into certain versions of Windows operating systems. BitLocker is designed to protect your precious data by encrypting the entire drive or partition, making the data inaccessible without the correct password, recovery key, or other authentications.
BitLocker is useful for securing sensitive information and preventing unauthorized access. However, despite its legitimate purpose, BitLocker can be misused by cybercriminals in what is called BitLocker virus or BitLocker ransomware attacks.
This post briefly explains what the BitLocker virus is and how the BitLocker ransomware attacks work. You can also learn how to get the BitLocker recovery key after your PC falls for the BitLocker ransomware.
What is the BitLocker virus?
BitLocker virus refers to a type of ransomware attack where cybercriminals abuse the BitLocker encryption tool to encrypt users' hard drives or partitions. Instead of using custom malware to encrypt files, attackers misuse the legitimate BitLocker encryption feature against the user.
Once the system is encrypted, the users cannot access their data and attackers demand a ransom in exchange for the decryption key that can unlock the data.
You can share this post and tell your friends what BitLocker virus is
How does the BitLocker virus work?
BitLocker ransomware (BitLocker virus) works by first gaining unauthorized access to a victim's computer through phishing emails, malicious downloads, or exploiting system vulnerabilities. Once the ransomware infiltrates the system, the attacker does whatever it takes to gain administrative access and activate the BitLocker to encrypt the entire disk or partition.
The victim is then locked out of their computer and prompted to a ransom message that demands payment in exchange for the decryption key that can unlock BitLocker and regain access to the system. The attacker provides the decryption key only after the ransom is paid, although there is no guarantee they will follow through.
How to find the BitLocker recovery key after the BitLocker virus attack?
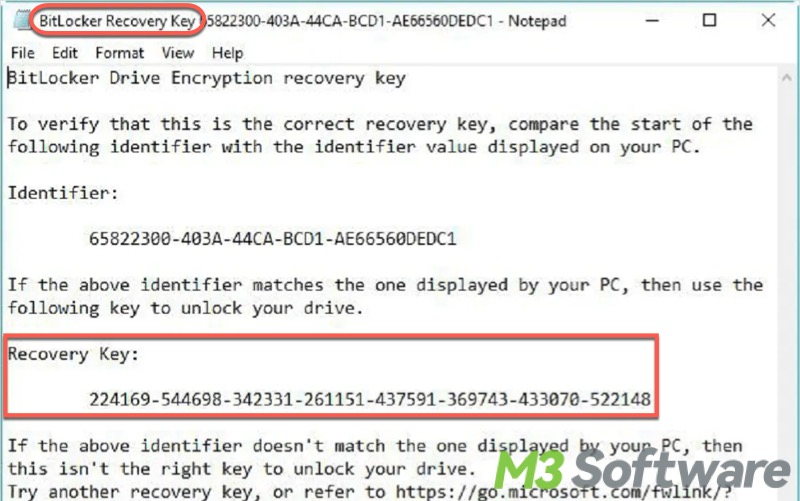
BitLocker recovery key is a 48-digit code automatically generated when you enable BitLocker encryption on a drive or partition. It can be used to unlock your BitLocker encrypted drive or partition, especially when you forget the password or normal authentication fails.
Without the recovery key, accessing the encrypted drive or partition is nearly impossible. As mentioned above, attackers misuse the legitimate BitLocker to encrypt, so a BitLocker recovery key will be generated and saved on your PC. You can follow the steps below to learn how to find it:
- Press the Windows key + R to open the Run dialog box, type "eventvwr.msc", and hit the Enter key.
- Expand the "Windows Logs" folder in the left side panel and click "System."
- Select all the BitLocker-related log entries, right-click to choose "Save Selected Events."
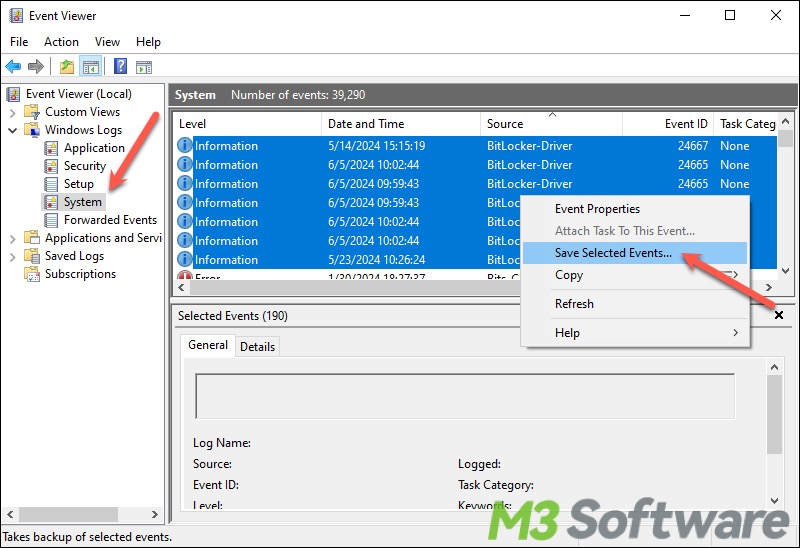
- Double-click the saved file to open it in the Event Viewer.
- Review the entries to check BitLocker encryption activity and pay attention to the logged time.
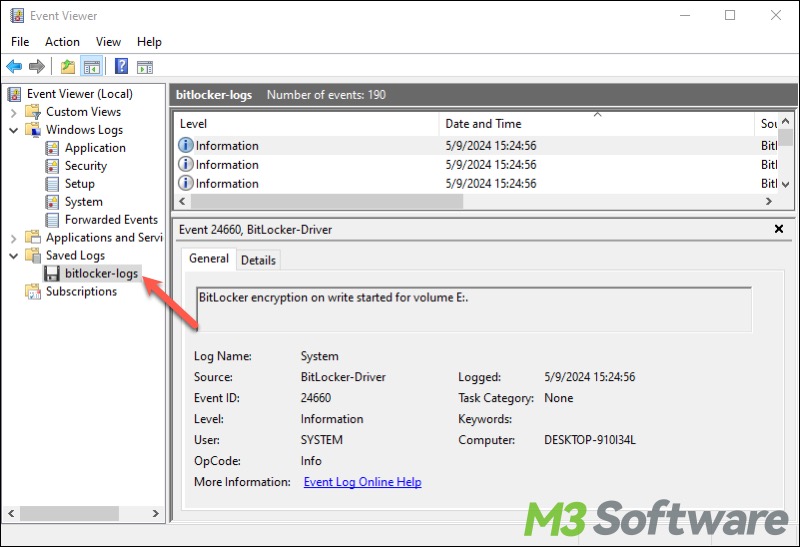
- Search for all .txt files in File Explorer and see if there's a BitLocker recovery key text file that is created by the time ransomware enables BitLocker.
Conclusion
To protect yourself from BitLocker virus (BitLocker ransomware), follow good security practices, such as using strong passwords, maintaining frequent backups of important data, keeping your system updated, and avoiding suspicious links or downloads.
Why not share this post with your friends if you find it helpful?
