Written by
Yuri ZhangSummary: This post explains BitLocker pre-boot authentication by definition and offers guides on how to enable, configure, and disable BitLocker pre-boot authentication.
BitLocker pre-boot authentication is a security feature that helps only authorized users access an encrypted Windows device by requiring authentication before the operating system even starts.
This authentication can take the form of a PIN, password, or even a USB key, adding an additional layer of protection beyond the standard system login process. Let's master what it is, how to enable, configure, and disable BitLocker pre-boot authentication now.
What is BitLocker pre-boot authentication?
BitLocker is a disk encryption feature available in Windows that helps protect data on your system drive by encrypting it. Pre-boot authentication is a security measure that requires the user to authenticate themselves before the system even begins to load Windows. This ensures that unauthorized users cannot access the encrypted drive, even if they have physical access to the machine.
Common types of pre-boot authentication include:
Pre-boot authentication ensures that even if someone steals our device, they cannot access our sensitive data unless they pass an authentication step before the system boots up. Different types of pre-boot authentication provide varying levels of security. Here are the typical types:
- TPM-only: Uses the Trusted Platform Module (TPM) to unlock the system drive automatically at boot. No additional authentication (PIN or password) is required.
- TPM + PIN: Requires both TPM and a user-defined PIN to unlock the system drive at boot.
- TPM + Password: Requires both TPM and a user-defined password at boot.
- USB Key: Requires an external USB key inserted at boot to unlock the system drive.
Share this to help more want protection from BitLocker pre-boot authentication.
How to enable BitLocker pre-boot authentication
Pre-boot authentication requires that a user must authenticate themselves before the operating system starts, thus adding an extra layer of protection to the system drive. To enable it, follow these steps.
- To enable TPM in BIOS/UEFI, restart your computer.
- Then access the BIOS/UEFI by pressing a designated key (e.g., F2(for most laptops),or Esc, or Delete (for many desktop systems), F10 (some HP systems) during the boot process.
- Locate the TPM or Security Chip setting and make sure TPM is enabled.
- Save the settings and exit BIOS/UEFI.
- Press Windows + R, type gpedit.msc, and press Enter to open the Group Policy Editor.
- Navigate to Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives.
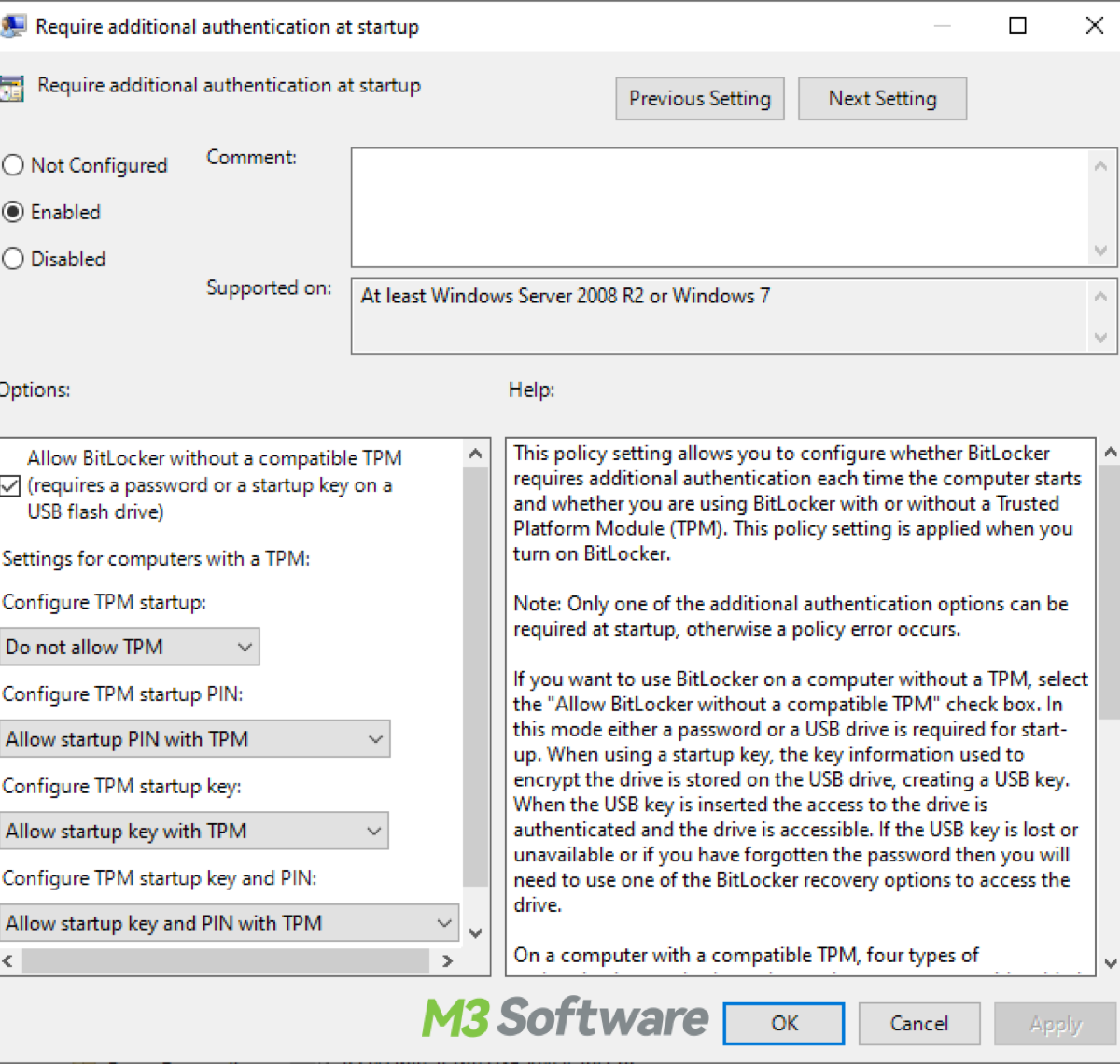
- Double-click on Require additional authentication at startup and set the policy to Enabled.
- Under Options, choose the appropriate authentication method: Allow BitLocker without a compatible TPM (if you do not want TPM required), TPM + PIN or TPM + Password, depending on your security preference.
- Click OK to save the changes.
- Open Control Panel and go to System and Security > BitLocker Drive Encryption.
- Click Turn on BitLocker for the system drive (usually C:).
- Choose how you want the drive to be unlocked at startup: TPM only/TPM + PIN/TPM + Password/USB key.
- Enter your PIN or Password when prompted.
- Save the Recovery Key to a secure location.
- BitLocker will begin encrypting the system drive.
- After BitLocker encryption is complete, restart your system. If you've configured TPM + PIN or TPM + Password, the system should prompt you to enter your PIN or password at boot before Windows starts.

Note: This enabling process requires you to first enable TPM in your system's BIOS/UEFI, then configure BitLocker settings to enforce pre-boot authentication. By the way, if you are looking for how to enable a pre-boot BitLocker Pin in Windows, just choose TPM + PIN in step 12 as above.
How to disable BitLocker pre-boot authentication
For environments where convenience and speed are more important than stringent security measures, such as devices in secure physical locations, personal devices, or devices used in controlled network environments, disabling pre-boot authentication makes sense. Additionally, for situations where users might forget their credentials, or when the devices are used in low-risk environments, disabling pre-boot authentication can reduce friction and improve user experience.
- Open Control Panel and navigate to System and Security > BitLocker Drive Encryption.
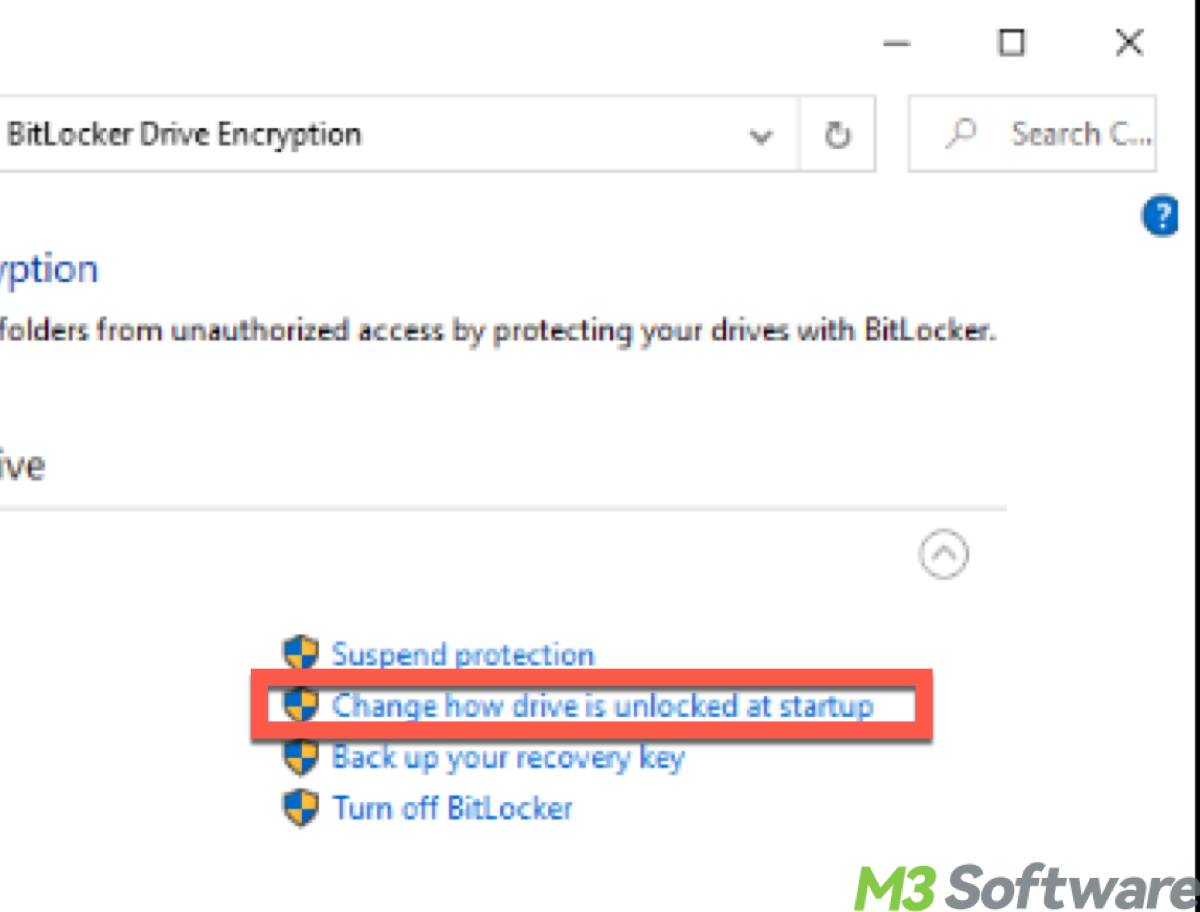
- Click on Change how drive is unlocked at startup (Under the Operating system drive (usually C:), you'll see the option "Change how drive is unlocked at startup." )
- Select TPM only and save the changes.
- BitLocker will remove the requirement for a PIN or password, and the system will use TPM-only authentication at boot.
- If you wish to completely remove BitLocker and all pre-boot authentication(optional), click Turn off BitLocker in BitLocker Drive Encryption.
Note: It is necessary to consider the security trade-offs before disabling this feature, as it removes an important barrier to unauthorized access in case of theft or tampering.
Advanced management with Intune or Group Policy
In enterprise environments, Microsoft Intune and Group Policy can be used to manage BitLocker configurations across multiple devices. Intune allows IT administrators to enforce BitLocker policies across an organization, including pre-boot authentication settings. Read this article: How to use Intune to manage BitLocker encryption.
Group Policy can be used to centrally manage and enforce BitLocker configurations for multiple machines, ensuring consistent security standards. This is especially useful for organizations that need to enforce strong security policies such as requiring a PIN at boot on all managed devices. Also read Understanding GPO BitLocker: Features and Capabilities.
Conclusion
BitLocker pre-boot authentication is a valuable security feature that ensures only authorized users can access encrypted systems, even before the operating system starts. By enabling TPM + PIN, TPM + Password, or USB key authentication, you can add significant layers of protection to your device.
Whether you're using BitLocker on a personal device or managing multiple systems in an enterprise, pre-boot authentication helps safeguard sensitive data. Conversely, if you prefer a more seamless startup, you can disable it and easily switch to TPM-only authentication or even disable BitLocker entirely.
Warning: Always remember to securely store the BitLocker recovery key for recovering access to your device lest you forget your PIN or password.
Share these insights if you find them useful.
