Written by
Yuri ZhangSummary: This article guides you through key concepts related to BitLocker key rotation, including how it works, the Group Policy settings involved, how to use PowerShell to manage keys, and how to automate the process using tools like Intune.
BitLocker is a full disk encryption feature built into Windows. While BitLocker doesn't have an explicit "key rotation" feature, administrators can take several steps to manage recovery key backup, re-encryption, and key protector policies effectively.
Let's dive into BitLocker key rotation by definition, including how to manage BitLocker key rotation employing Group Policy, PowerShell, and Intune.
Reddit discussion on BitLocker key rotation
In Microsoft Intune, BitLocker recovery key rotation is not automatic. Administrators must manually initiate the rotation for each device. The Intune documentation specifies that to rotate the BitLocker recovery key, an administrator needs to select the device and choose the rotate BitLocker recovery key option.
Bitlocker AUTOMATIC key rotation?
by u/Real_Lemon8789 in Intune
From the intensive discussion on Reddit, currently, there is no Microsoft documentation indicating that Intune-managed systems will automatically rotate BitLocker recovery keys without administrative intervention. Key rotation must be manually triggered by an administrator for each device as needed.
To straighten these things up. We devise this article to show a clear explanation of BitLocker key rotation based on real user reviews and assist you with a comprehensive guide to carry the rotation. Just keep reading.
What is BitLocker key rotation?
BitLocker key rotation refers to the process of refreshing or changing the BitLocker recovery key or encryption key. While there is no direct "key rotation" option in BitLocker itself, administrators can rotate keys by re-encrypting the drive, regenerating new recovery keys, or periodically updating key protectors. Key rotation is important for maintaining security, especially when drives are frequently encrypted, decrypted, or managed remotely.
How to manage BitLocker key rotation via Group Policy
Group Policy (GPO) can be used to enforce settings that indirectly support key rotation and ensure the recovery keys are properly managed and backed up to a secure location like Active Directory (AD). Below are key GPO settings related to BitLocker recovery key management:
1. Backing up BitLocker recovery keys to Active Directory (AD)
To ensure that BitLocker recovery keys are securely stored and accessible, administrators can configure Group Policy to automatically back up recovery information to Active Directory. This allows an administrator to retrieve the key in case of an emergency, such as when a user forgets their PIN or password.
Steps to configure Group Policy for backing up BitLocker recovery keys to AD:
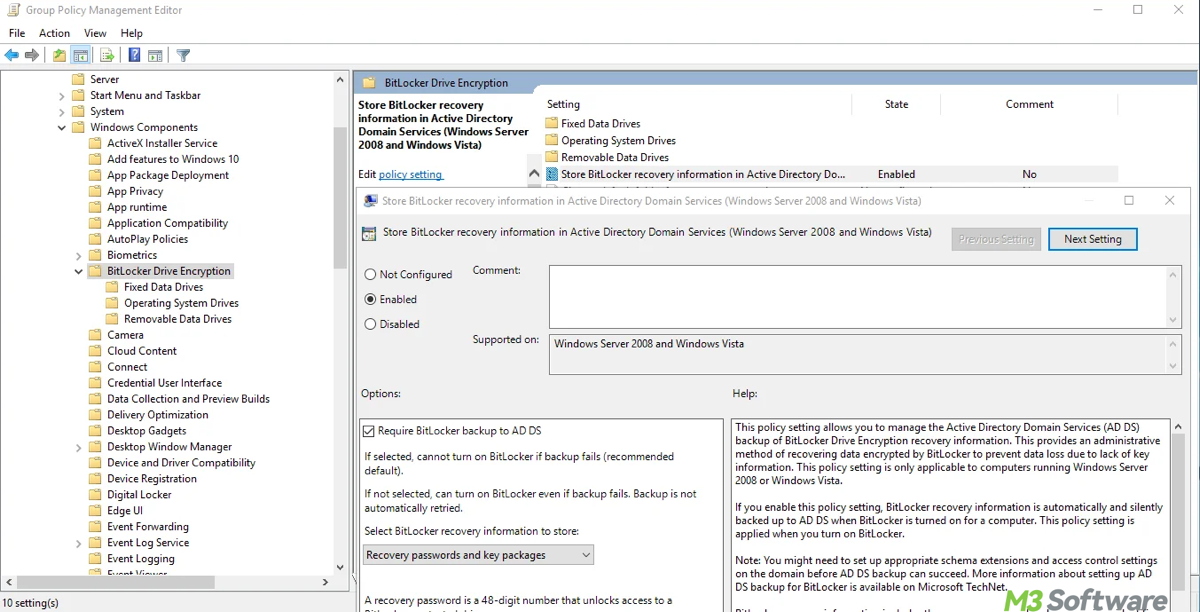
- Open Group Policy Management Console (GPMC) by pressing Windows + R, then type gpmc.msc and press Enter and create or modify a Group Policy Object (GPO).
- Navigate to Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption.
- Enable the policy "Store BitLocker recovery information in Active Directory Domain Services".
- Optionally, enable "Do not enable BitLocker until recovery information is stored in Active Directory" to enforce recovery key storage before encryption.
By enforcing this GPO, you ensure that every BitLocker-enabled device automatically saves its recovery key in AD, providing a secure backup mechanism for key management.

2. Triggering re-encryption to rotate the encryption key
While BitLocker does not have a built-in key rotation policy, re-encryption can be used as a workaround to regenerate a new encryption key. Re-encrypting the disk triggers the generation of a new encryption key, thus effectively rotating the key.
Re-encryption can be performed manually or through automated tools like PowerShell or Intune. Here's how you can force re-encryption of a drive via PowerShell (You can open it by pressing Windows + S, then type PowerShell and select Windows PowerShell, then type the following command and press Enter):# Re-encrypt the C: drive to trigger key rotation
Enable-BitLocker -MountPoint "C:" -EncryptionMethod Aes256 -UsedSpaceOnly
This action will create a new encryption key and may be required periodically based on your organization's security policies.
Share this and learn more about BitLocker key rotation.
Managing BitLocker key rotation via PowerShell
PowerShell provides a powerful way to manage BitLocker encryption and recovery keys. While Group Policy controls the key backup and encryption settings, PowerShell allows administrators to rotate and regenerate keys directly.
1. Retrieve the current BitLocker recovery key
To see the current recovery key for a drive, you can use the following PowerShell cmdlet:# Retrieve current BitLocker key protector for the C: drive
(Get-BitLockerVolume -MountPoint "C:").KeyProtector
2. Remove and add new key protectors
If you want to rotate the key by removing an old key protector and adding a new one, use the following commands as a whole:
# List all protectors for C: drive
Get-BitLockerVolume -MountPoint "C:" | Select-Object -ExpandProperty KeyProtector
# Remove an existing key protector
Remove-BitLockerKeyProtector -MountPoint "C:" -KeyProtectorId "ID_of_the_Key_Protector"
# Add a new recovery key protector
Add-BitLockerKeyProtector -MountPoint "C:" -RecoveryPassword
3. Force re-encryption via PowerShell
To trigger re-encryption and force a key rotation, you can use the following PowerShell command:# Re-encrypt the C: drive to generate a new encryption key
Enable-BitLocker -MountPoint "C:" -EncryptionMethod Aes256 -UsedSpaceOnly
This forces the drive to re-encrypt, which regenerates the encryption key and ensures that the new recovery key is backed up (if configured).
BitLocker key management with Intune
For Azure AD-joined or domain-joined devices managed with Microsoft Intune, BitLocker key rotation can be more easily managed. Intune allows administrators to configure BitLocker settings, enforce recovery key backup, and even re-encrypt devices to rotate keys.
1. Configure BitLocker in Intune
In Intune, you can configure BitLocker settings, including policies for enabling encryption and storing recovery keys. Once devices are encrypted, re-encryption can be initiated to generate new keys. Here's how to configure BitLocker in Intune:
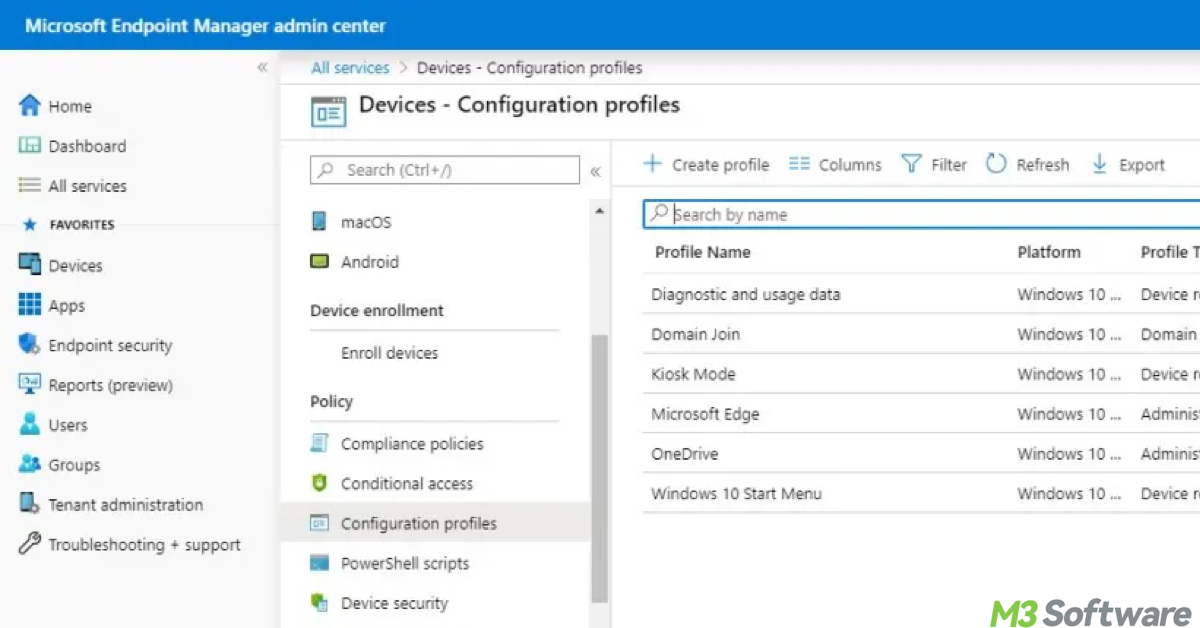
- Sign in to the Intune Admin Center and go to Endpoint Manager > Devices > Windows > Configuration profiles > Create profile.
- Select Windows 10 and later as the platform and BitLocker as the profile type
- Under BitLocker settings, enable Recovery Key Backup to Azure AD.
2. Automate BitLocker recovery key rotation in Intune
To automate the rotation of recovery keys, Intune can force a new recovery key or trigger re-encryption if needed. Intune's integration with Azure AD allows you to store recovery keys in the cloud, providing an additional layer of security and simplifying key management.
To enable automatic BitLocker recovery key rotation in Microsoft Intune, follow these steps:
- Go to https://endpoint.microsoft.com and log in with your administrative credentials.
- Navigate to Endpoint security > Disk encryption.
- Click Create Policy.
- Set Platform to Windows 10 and later.
- Choose the BitLocker profile.
- Click Create.
- In Configuration settings, expand BitLocker base settings. Set Enable client-driven recovery password rotation to Yes.
- Under Assignments, select the groups to apply the policy.
- Click Next, review the settings, and then click Create to deploy the policy.
By completing these steps, Intune will automatically handle the rotation of BitLocker recovery keys after they are used, enhancing the security of your devices.
Conclusion
While BitLocker key rotation isn't a built-in feature, administrators can effectively manage key rotation by using a combination of Group Policy, PowerShell, and Intune. Here's a summary of key techniques:
1. Ensure that recovery keys are backed up to Active Directory or Azure AD through Group Policy. 2. Trigger re-encryption via PowerShell or Intune to rotate the encryption key and generate a new recovery key. 3. There is automated key management by leveraging Intune to enforce policies and re-encrypt devices.
By combining these methods, you can ensure that your BitLocker encryption is properly managed and that recovery keys are securely stored and periodically rotated to maintain a high level of security. Also read How to Harness PowerShell to Enable BitLocker and Understanding GPO BitLocker: Features and Capabilities
Share this and become an expert in BitLocker key rotation.
