Written by
Wilsey YoungSummary: This post revolves around BitLocker benefits and explains what makes the BitLocker Drive Encryption feature so secure and reliable for Windows users. You can keep reading this post for greater insight into this built-in encryption feature on Windows.
Protecting important data and sensitive information against unauthorized access is extremely crucial in modern life, especially for those who store large amounts of data on their PC or storage devices.
When it comes to securing our data on Windows devices, the BitLocker Drive Encryption feature often comes into the spotlight and it has long been favored by most Windows users. This post focuses on introducing the benefits of BitLocker and interprets what makes BitLocker so secure in safeguarding the data.
Benefits of BitLocker
What encryption does BitLocker support? How secure is BitLocker? What is TPM and how does it work with BitLocker to provide maximum protection? The following contents will help you understand more about the benefits of using BitLocker on Windows.
BitLocker benefits 1: Full disk encryption with Advanced Encryption Standard
BitLocker allows users to encrypt the entire drive, including the operating system drive, fixed data drive, or removable data drive, ensuring that all files and data are protected from unauthorized access, particularly when devices are lost or stolen, as it ensures that the unauthorized users cannot access the data without the proper decryption key, such as password, recovery key, or more.
BitLocker encrypts the drive using the Advanced Encryption Standard (AES), a symmetric-key block cipher. It's widely considered one of the most powerful and secure encryption algorithms. For BitLocker, AES supports the key lengths of 128 bits and 256 bits.
The longer the key length, the higher the level of security against brute-force attacks. For instance, AES 256 bits is known for its extremely strong resistance to various cryptographic attacks, making it computationally infeasible for an attacker to try all possible keys even with powerful computing power.
BitLocker benefits 2: BitLocker works perfectly with TPM to maximize protection
TPM is a hardware chip embedded in most modern computers, and it securely stores authentication keys and plays critical role in encryption, authentication, and integrity verification.
TPM makes all the difference during the system boot, as TPM verifies that the system's integrity hasn't been compromised and ensures there aren't any unauthorized changes. Otherwise, TPM will not release the key and the user will encounter the BitLocker recovery blue screen which requires the BitLocker recovery key to let the system boot up normally.
You can check the following post for more details about BitLocker and TPM: BitLocker and TPM: How Does TPM Work with BitLocker?
Why not share this post with your friends?
BitLocker benefits 3: Enhanced protection against unauthorized users
If TPM detects possible unauthorized access, a BitLocker recovery blue screen will pop up during system boot and the user will be required to input the BitLocker recovery key before the system can boot up, ensuring that no unauthorized users can access and tamper with your hard drive or boot from the external device.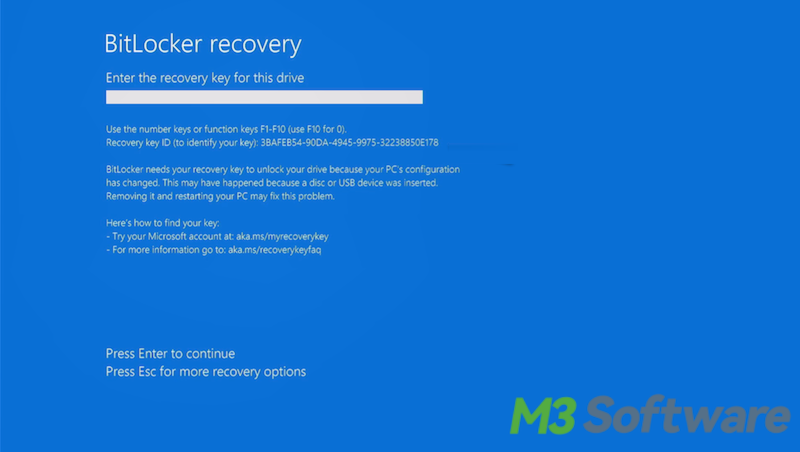
Here are the situations that may trigger the BitLocker recovery blue screen before the system can boot up:
- When TPM detects significant changes to the computer hardware, such as the motherboard, hard drive, or storage device.
- When TPM detects changes to system boot configuration, such as boot order or bootloader
- When TPM detects changes to the BitLocker group policies or settings.
- When TPM detects changes to UEFI or BIOS, including UEFI/BIOS update or reset, enabling or disabling features like Secure Boot.
- When TPM detects changes to password, PIN, or other authentication keys.
- When TPM detects TPM-related issues or changes.
- When TPM detects Windows update or reinstall.
- When TPM detects attempts to boot the system from an external device or bootable media.
- When a BitLocker user inputs the incorrect decryption key (e.g. password, PIN) several times.
When BitLocker keeps asking for the BitLocker recovery key during system boot, you can seek solutions in the following post: BitLocker Keeps Asking for Recovery Key: Causes & Solutions!
BitLocker benefits 4: Configurable group policy
Enterprises and users are allowed to configure and manage BitLocker using Group Policy for enhanced security or specific needs. For example:
- Require additional authentication at startup
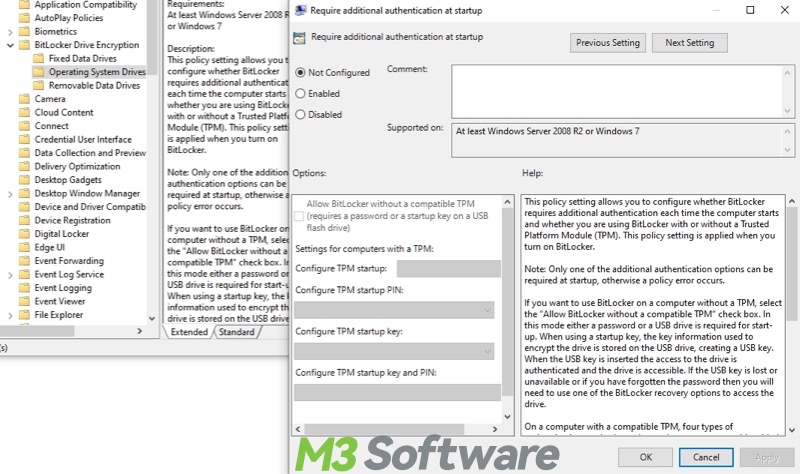
- Configure minimum PIN length for startup
- Choose drive encryption methods and cipher strength
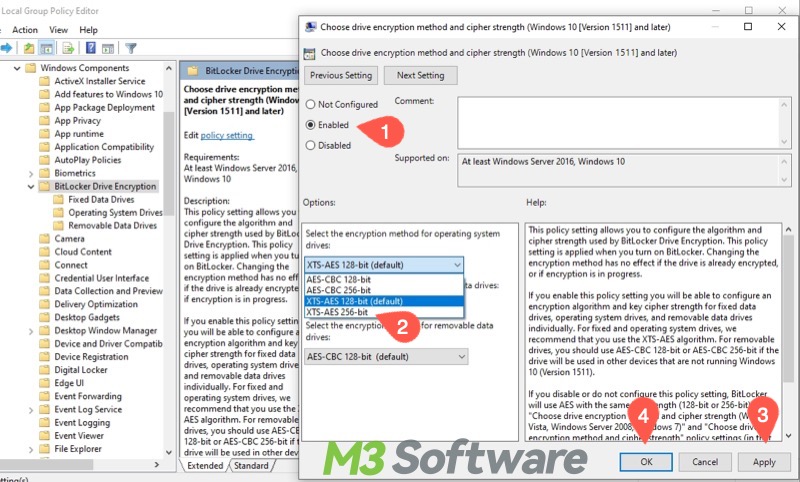
- Deny write access to fixed drives not protected by BitLocker
To configure BitLocker group policy settings, read this: BitLocker Group Policy: What Is It & How to Configure?
BitLocker benefits 5: Data protection for removable storage devices
Removable storage devices are particularly vulnerable to data theft or unauthorized access. BitLocker-To-Go feature extends the BitLocker drive encryption to removable storage devices, such as USB flash drives, external hard drives, etc.
The following post introduces the BitLocker-To-Go in detail: BitLocker To Go: What Is It & How to Use It on Windows?
BitLocker benefits 6: Remote management
BitLocker supports centralized management through Microsoft's enterprise tools, so enterprises can deploy, manage, and monitor BitLocker-encrypted devices across an organization, ensuring consistent security policies.
Conclusion
BitLocker is remarkably effective in protecting your data against unauthorized access. Whether you're a home, business, or enterprise user concerned about data security and privacy, BitLocker provides robust encryption and ensures no unauthorized users can access and tamper with your data stored on the encrypted drive.
You can click the buttons below to share the post!
