Written by
Yuri ZhangWhen setting up BitLocker Drive Encryption on a Windows machine, one of the fundamental questions that arise is: How many NTFS partitions does BitLocker require to operate properly?
In this article, we'll explore the requirements for using BitLocker with NTFS partitions, discuss the roles of the different partitions involved, and help you understand how the system partitions work together to ensure your data is encrypted and protected.
Comprehending BitLocker encryption partition
BitLocker is a full disk encryption feature included in Microsoft Windows. Its primary purpose is to protect data by encrypting entire volumes, and preventing unauthorized access in case the computer is lost or stolen. BitLocker works by encrypting the system drive where the operating system is installed and additional data drives (if configured).
However, to encrypt and protect the system volume, BitLocker requires a specific partition structure on the disk. This partitioning scheme is important because it determines how the encryption process will function, particularly regarding booting the system securely and unlocking the encrypted drive.
Partition structure and requirements
For BitLocker to operate correctly on an NTFS-formatted disk, at least two partitions are necessary. Here's a breakdown of these partitions:
1. System Reserved Partition (SRP)
The SRP is typically not visible to the user because it is a hidden partition, but it must be present for BitLocker to work.
- Size: Typically between 100 MB and 500 MB.
- File System: FAT32 (not NTFS).
- Location: This partition is created automatically during Windows installation and resides at the beginning of the disk.
Note: The System Reserved Partition (SRP) is essential for booting the system. It contains the Boot Manager (Bootmgr) and the Windows Boot Configuration Data (BCD) store, both of which are required to start the operating system. In addition, this partition holds the BitLocker metadata (e.g., encryption keys) that help unlock the drive during startup. While this partition is crucial for BitLocker, it typically does not get encrypted, as its primary purpose is to facilitate the boot process and enable security measures.
2. Primary partition (OS partition)
This partition is usually the largest partition on the disk and contains both the operating system files and user data.
- Size: Varies, typically several hundred GB (depending on the size of the drive and the system installation).
- File System: NTFS.
- Location: This is where the operating system (Windows) is installed and where BitLocker encryption takes place.
Note: The Primary Partition is where Windows is installed (the C: drive in most cases). This is the partition that is encrypted by BitLocker. Once encrypted, the files on this partition become protected, meaning that without the correct authentication method (password, TPM, PIN, etc.), access to the data will be denied.
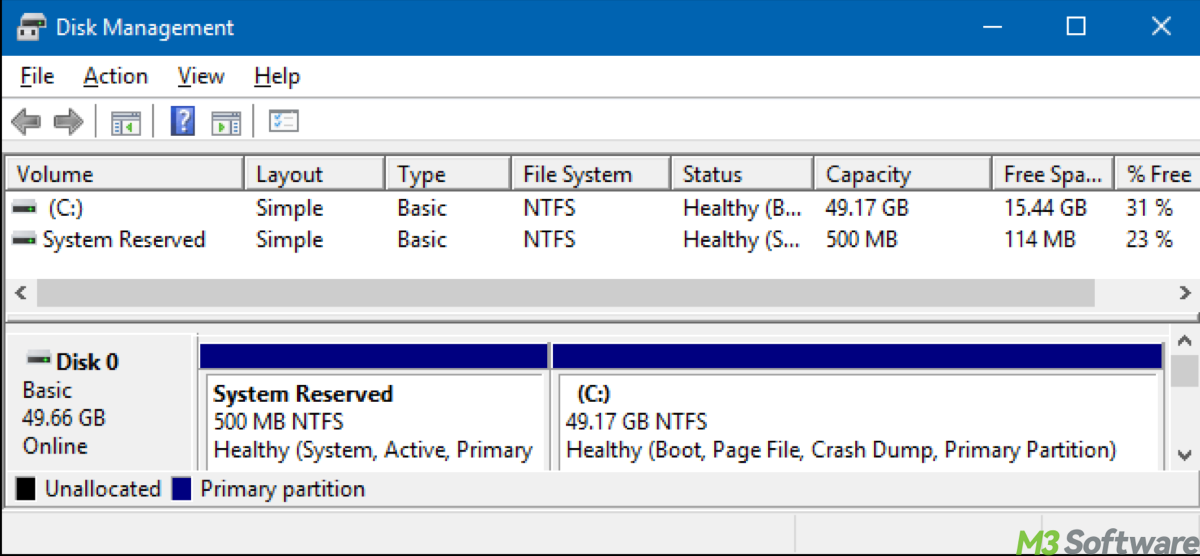
3. Additional data partitions (optional)
- Size: Varies depending on user configuration.
- File System: NTFS, exFAT, or other formats depending on usage.
Note: While the System Reserved Partition and the Primary Partition are mandatory, BitLocker can also encrypt additional data drives if they exist. These drives can be encrypted with the same encryption method used on the OS partition, but they do not require a separate, unique partitioning scheme. You can encrypt individual data partitions without impacting the boot process.
Share this with those who have no idea of BitLocker's requirement in NTFS partitions.
Why are two partitions needed to operate BitLocker?
The System Reserved Partition (SRP) is necessary because it holds the essential files for the Windows boot process. BitLocker needs to ensure that, even though the operating system partition is encrypted, the boot files remain accessible and can be authenticated using a TPM (Trusted Platform Module) or a PIN during the startup process. By keeping the boot files in a separate partition, BitLocker maintains the integrity and security of the system while allowing the operating system itself to be encrypted.
BitLocker stores encryption keys and other essential metadata in the System Reserved Partition, which is why this partition needs to remain unencrypted. This enables BitLocker to decrypt the OS partition at boot time without user intervention, as long as the authentication requirements (TPM, PIN, or password) are met.
By maintaining a separate System Reserved Partition, the operating system's boot process and encryption keys are isolated from the data partition. This design helps prevent potential attacks on the encryption system while also ensuring that the bootloader is protected and can function correctly without requiring direct access to the encrypted OS partition.
This two-part structure ensures BitLocker works seamlessly and securely without interfering with the boot process.
BitLocker encryption on non-NTFS partitions
BitLocker can encrypt partitions formatted with NTFS or exFAT, though the System Reserved Partition must always be formatted with FAT32 for compatibility with the boot process. If you're using BitLocker on an external drive, such as a USB thumb drive, BitLocker might format it as exFAT or NTFS, depending on your configuration.
For external drives that you wish to encrypt with BitLocker, the same principles apply: BitLocker requires at least one partition to store the data and, optionally, a second partition for recovery information or metadata.
Conclusion
BitLocker requires at least two NTFS partitions to operate:
- System Reserved Partition, this partition, which is typically FAT32, holds the essential boot files and BitLocker metadata. It's hidden and contains no user data.
- Primary Partition, this is the partition where Windows is installed and is encrypted by BitLocker. It is usually NTFS and contains both the operating system and user data.
If you have additional data drives, they can also be encrypted by BitLocker, but the key concept is that the primary OS partition and the System Reserved Partition must exist for BitLocker to work as intended. BitLocker uses the SRP to manage encryption keys and perform a secure boot, while the OS partition is where the encryption of sensitive data occurs.
Related articles
Put a Password on USB Flash Drive Without BitLocker, How?
Cloning a BitLocker-Encrypted Drive: How to Do It Right
Updating BIOS with BitLocker Enabled, Applicable?
Spread and know this expertise by heart.
