Written by
Yuri ZhangSummary: This article provides a detailed tutorial on how to retrieve the BitLocker recovery key using PowerShell, with the relevant cmdlet, you can get the BitLocker recovery key effortlessly and readily.
BitLocker is a popular encryption feature available in Windows that protects your data by encrypting entire volumes. In the event of an unexpected change to your system's hardware or software, such as a motherboard change or incorrect TPM configuration, BitLocker might prompt a recovery key to ensure data protection.
Retrieving the BitLocker recovery key can be done using several methods, but PowerShell provides a quick and powerful way to access this critical information. I will guide you through the process of using PowerShell to get the BitLocker recovery key for your encrypted drives in this article.
Prerequisites
Before you start retrieving the BitLocker recovery key using PowerShell, ensure that the following conditions are met:
Administrative access to the computer:
You must have administrator privileges to run PowerShell commands related to BitLocker. This ensures that you have the necessary permissions to access the BitLocker volume information and retrieve recovery keys.
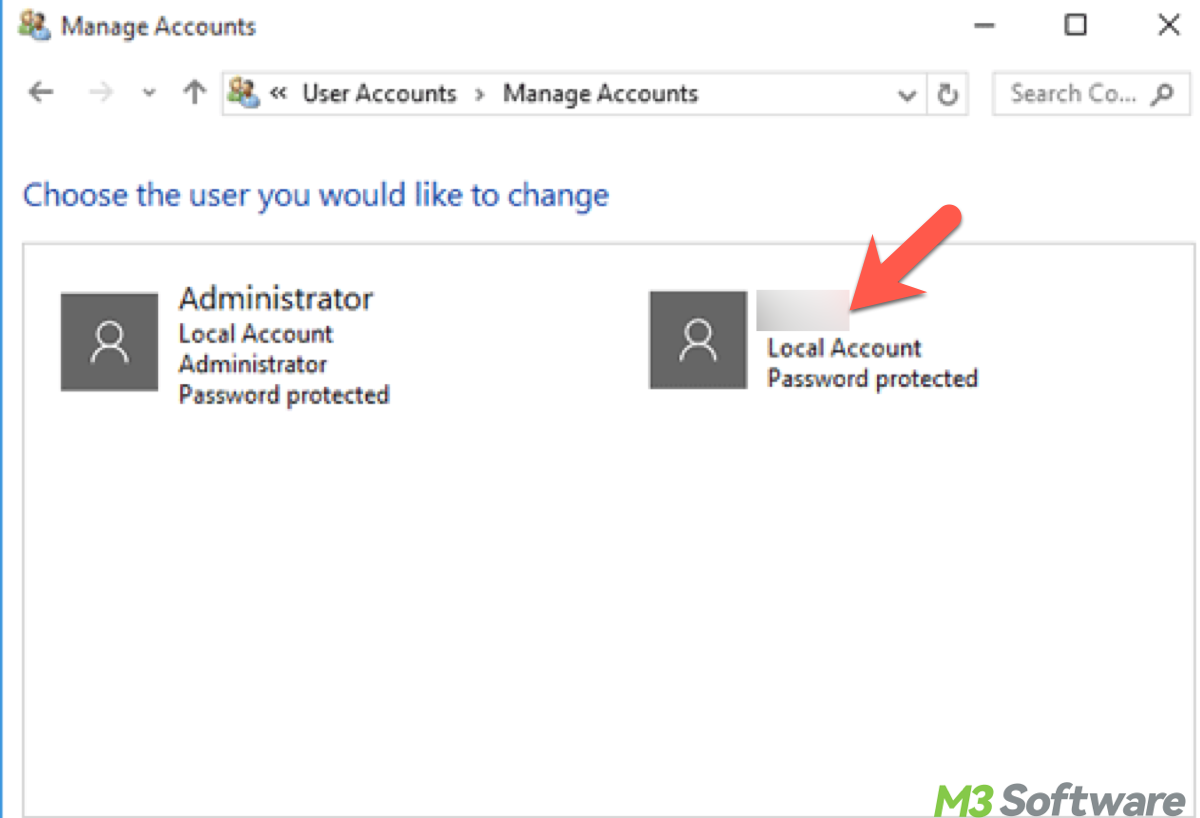
To verify if you have administrative rights, navigate to the Start menu, search for "Control Panel," and open User Accounts. Your account should show "Administrator" under your username.
PowerShell installation:
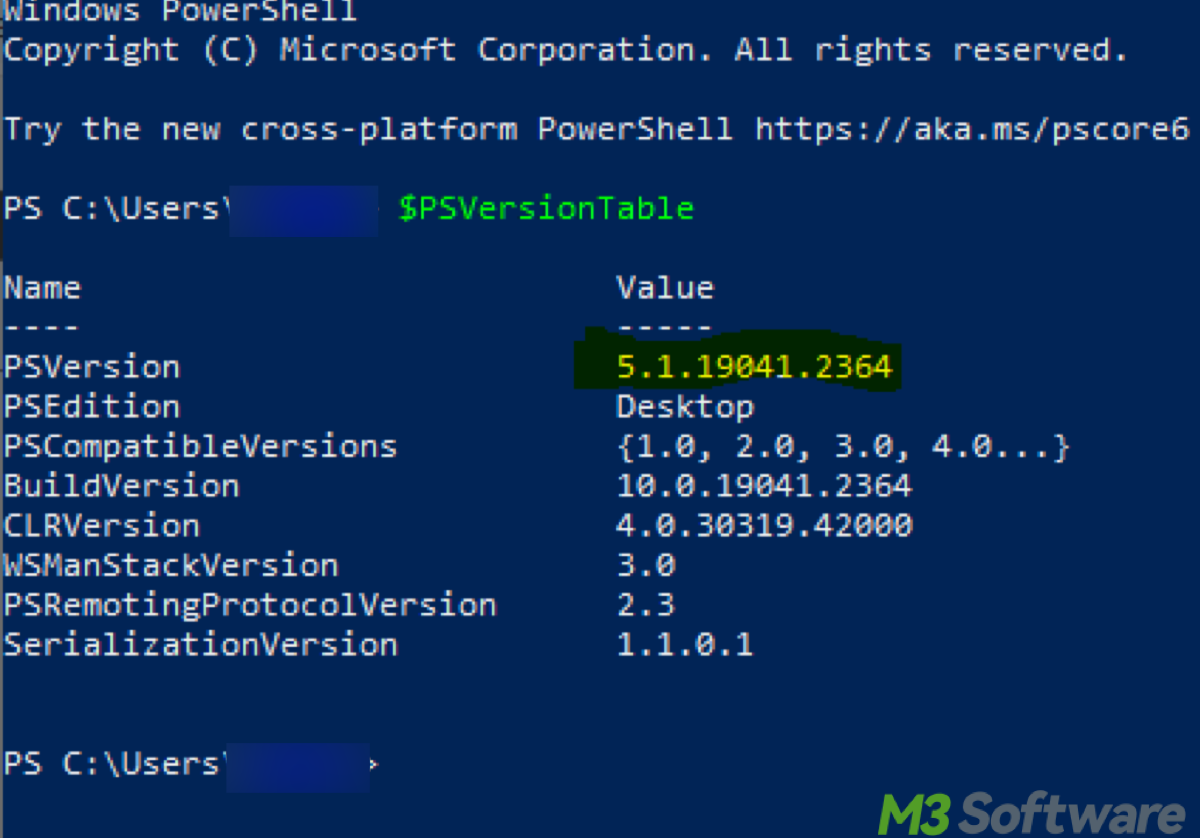
PowerShell is a task automation framework and configuration management tool that comes pre-installed on Windows 10 and Windows 11. To check if PowerShell is installed and which version is available:
- Press Windows + S, type "PowerShell," and click Windows PowerShell.
- In the PowerShell window, type the following command and press Enter:$PSVersionTable.PSVersion
This will display the installed PowerShell version. For BitLocker commands, PowerShell 5.0 or newer is recommended (Windows 10 and 11 already meet this requirement).

Drive protected by BitLocker:
BitLocker must be enabled on the drive from which you want to retrieve the recovery key. BitLocker is a full-disk encryption feature available in Windows Pro, Enterprise, and Education editions. To check if BitLocker is protecting a drive:
- Open File Explorer and navigate to This PC.
- Look for a padlock icon next to the drive, indicating that it is protected by BitLocker.
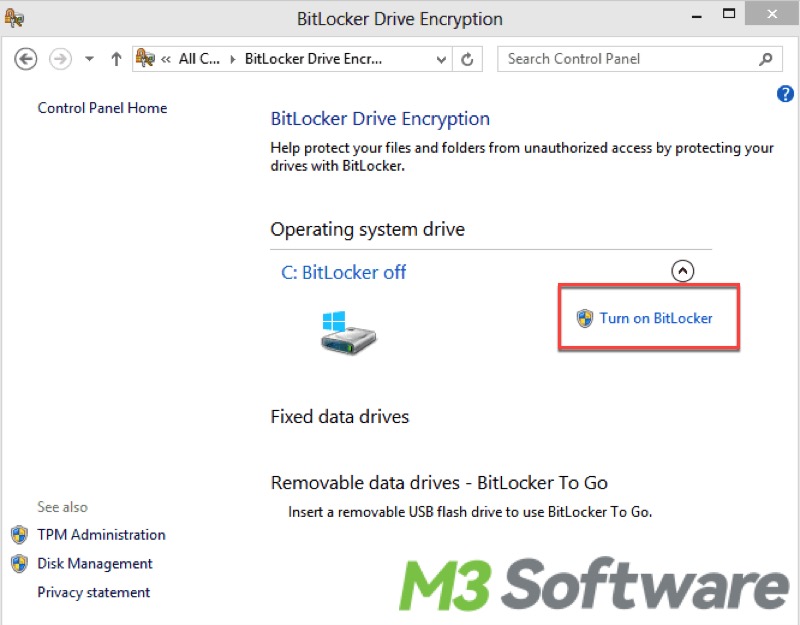
- Alternatively, you can open the Control Panel, select BitLocker Drive Encryption, and verify that your drive's protection status is turned On.
These conditions must be fulfilled to successfully run PowerShell commands and retrieve the BitLocker recovery key.
Share this to inform others of the precondition to use PowerShell to retrieve BitLocker recovery key.
How to use PowerShell to get BitLocker recovery key
Pay more attention to the following content, the respective cmdlets are coming in the way, which is of primary importance.
Step 1: Open PowerShell as Administrator
- Press Windows + X on your keyboard to open the Power User Menu.
- Select Windows PowerShell (Admin) or Terminal (Admin) from the list.
- If prompted by User Account Control (UAC), click Yes.
Step 2: Get the BitLocker volume information
To retrieve information about the BitLocker-protected drives on your system, use the following command:Get-BitLockerVolumeThis command will display a list of all volumes that are encrypted or protected by BitLocker. It will show key details such as the drive letter, protection status, and percentage of encryption completion.
Step 3: Retrieve the BitLocker recovery key
If your device is part of a corporate environment, and your organization uses Active Directory (AD) to manage devices, the recovery key may be backed up automatically to AD. In such cases, you can use the following cmdlet and click Enter to retrieve the recovery key from Active Directory (optional):BackupToActiveDirectory
If you are retrieving the recovery key on a personal or standalone system, you can use the following command and click Enter to view the key protector details, including the recovery password:(Get-BitLockerVolume -MountPoint "C").KeyProtector
This will output information about the recovery key protector, including the recovery password. The recovery password is essentially the BitLocker recovery key, which you can use to unlock your drive.
Note: Replace "C" with the drive letter of the BitLocker-encrypted volume for which you need the recovery key.
Step 4: Backup the recovery key
It's a good idea to back up your recovery key for future use. You can export the recovery key using PowerShell and save it in a secure location. Use the following command and click Enter to back up the recovery key to a text file:(Get-BitLockerVolume -MountPoint "C").KeyProtector | Out-File -FilePath "C:\BitLockerRecoveryKey.txt"
Tips: This command saves the recovery key for the specified volume into a text file at the specified path (e.g., C:\BitLockerRecoveryKey.txt). Remember to store this file in a safe and secure location.
Troubleshooting
If no recovery key is shown, ensure that the drive is encrypted and BitLocker is turned on. The Get-BitLockerVolume command should show a status of "Protection On" for the selected volume. If you are unable to run BitLocker-related PowerShell cmdlets, make sure that BitLocker is enabled in your version of Windows and that you're running PowerShell as an administrator.
Conclusion
Using PowerShell to retrieve the BitLocker recovery key is a simple and efficient method for system administrators and tech-savvy users alike. It eliminates the need to navigate through the graphical user interface and provides a powerful way to interact with BitLocker-protected volumes.
Backing up and managing your BitLocker recovery keys is crucial. PowerShell is an indispensable tool in your BitLocker management toolkit. If you unfortunately lost BitLocker encrypted data, there is also a feasible tool, iBoysoft Data Recovery for Windows, click the following green button to gain perfect data recovery.
Also read
How to Get BitLocker For Windows 7/8/10/11
How to Spot BitLocker Recovery Key Precisely
How to Use BitLocker with Ease
Share this article and get better at adept usage of PowerShell.
