Written by
Yuri ZhangBitLocker is an encryption feature in Windows that helps protect data. Properly storing and managing these recovery keys is crucial for IT administrators to ensure both security and business continuity. This guide addresses how to store, retrieve, and manage BitLocker recovery keys in Active Directory (AD), and Azure AD.
Where to store BitLocker recovery keys
This post focuses on AD and Azure AD methods as requested by many web browsers. As far as we know, you can store the BitLocker recovery key through the following channel:
- Microsoft Account: Save it online for easy access.
- USB Drive: Store it on a USB drive for physical backup.
- Printed Copy: Print and store it in a secure location.
- Azure Active Directory: For work or school devices (accessible by IT).
- Active Directory: For corporate network devices (retrievable by IT).
How to store BitLocker recovery keys in Active Directory (AD)
In a traditional on-premises Active Directory (AD) environment, BitLocker recovery keys can be automatically backed up to AD when a machine is domain-joined and BitLocker is enabled with the appropriate Group Policy settings. The recovery keys are stored in the msFVE-RecoveryInformation attribute of the computer object in the Active Directory.
1. Group Policy configuration for AD
For domain-joined devices, ensure that Group Policy is configured to automatically back up BitLocker recovery information to Active Directory. This configuration can be set as follows:
- Press Windows + R to open the Run dialog.
- Type gpmc.msc and press Enter. This opens Group Policy Management.
- In the Group Policy Management window, expand the Forest and Domains sections on the left.
- Right-click the Group Policy Object (GPO) you want to modify (or create a new one), then select Edit.
- In the Group Policy Management Editor window, follow this path: Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives.
- Find the policy titled “Store BitLocker recovery information in Active Directory Domain Services”.
- Double-click on the policy to open its settings.
- Select Enabled to enable the policy and click OK to apply the setting.
- (Optionally, configure additional settings to specify which type of recovery information (password or key) should be backed up. To do this, look for options like "Configure recovery information" in the same policy section and adjust settings as needed.
After configuring, click OK to save any changes.) - After applying the changes, close the Group Policy Management Editor and Group Policy Management windows.
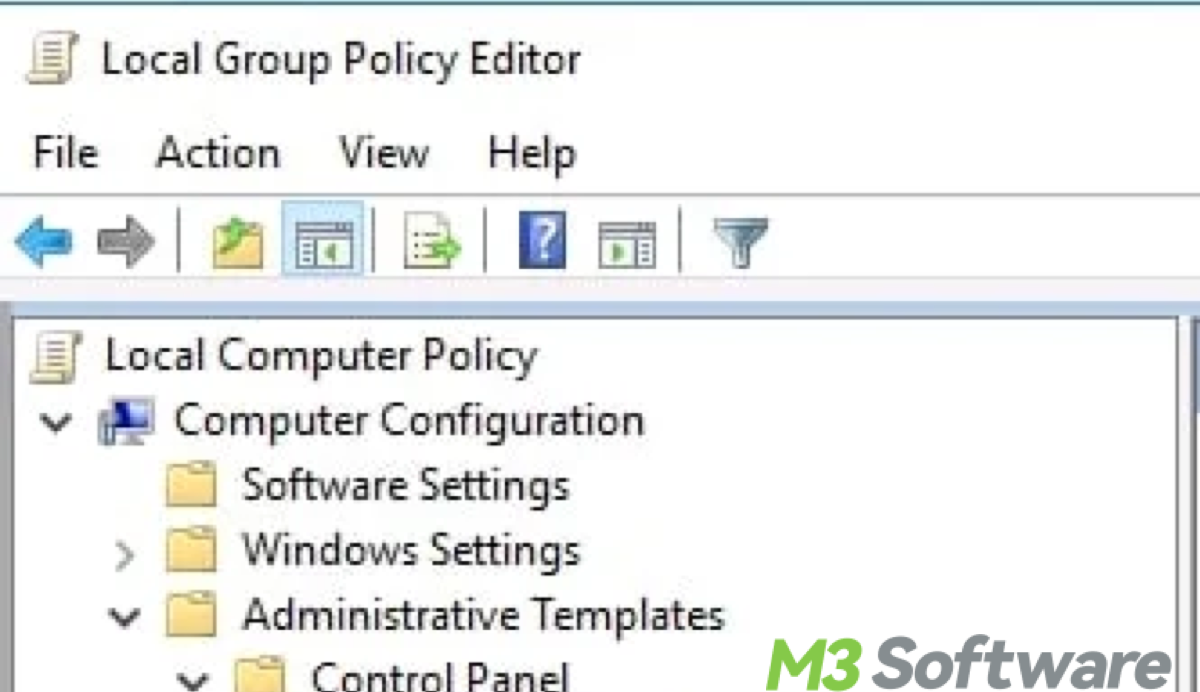
Once configured, this will automatically store the BitLocker recovery key in the Active Directory database whenever BitLocker is enabled on a device.
2. Verify BitLocker recovery key in AD
After BitLocker is enabled and recovery information is backed up, you can retrieve the recovery key from Active Directory Users and Computers (ADUC):
- Press Windows + R to open the Run dialog.
- Type dsa.msc and press Enter to open Active Directory Users and Computers.
- Navigate to the Organizational Unit (OU) or container where the computer object (the device you're looking for) is located.
- You may need to expand the domain tree on the left to find the correct OU.
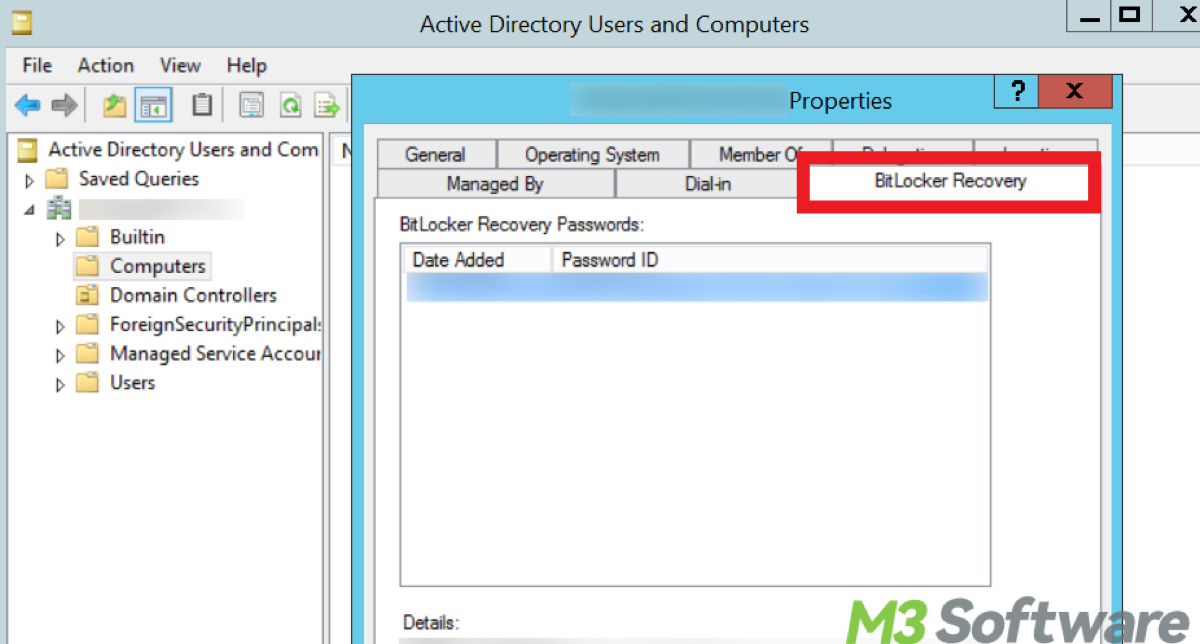
- Once you find the computer object (the device you need), right-click on it and select Properties from the context menu.
- Go to the BitLocker Recovery tab to view and copy the recovery key.
- By following these steps, you can view and retrieve the BitLocker recovery key from Active Directory for the specified computer.
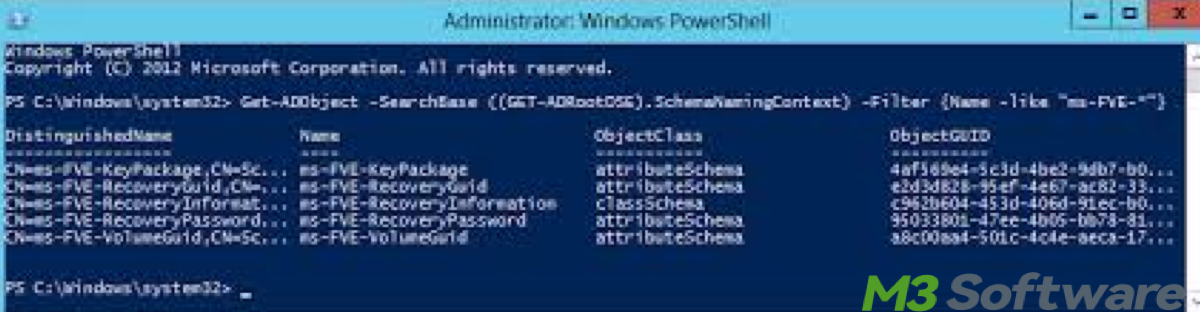
Alternatively, use PowerShell to query the msFVE-RecoveryInformation attribute, this method allows you to retrieve the BitLocker recovery key directly from Active Directory using PowerShell.
- Press Windows + X and select Windows PowerShell (Admin) or Command Prompt (Admin) from the menu.
- If PowerShell is not listed, you can search for it in the Start menu and right-click to select Run as Administrator.
- In the PowerShell window, type the following command, replacing "ComputerName" with the actual name of the computer you're querying:
Get-ADComputer -Filter {Name -eq "ComputerName"} -Property "msFVE-RecoveryInformation" | Select-Object -ExpandProperty "msFVE-RecoveryInformation"
- After running the command by pressing Enter, PowerShell will display the BitLocker recovery key associated with the specified computer.
Tips: Ensure you have the Active Directory module for PowerShell installed and you have the necessary permissions to query Active Directory for this information.
Share this to help more yearning for AD methods to store BitLocker recovery key.
How to store BitLocker recovery keys in Azure AD
For devices that are Azure AD-joined or Hybrid Azure AD-joined, recovery keys can be automatically stored in the Azure Active Directory. Azure AD is best suited for cloud-first environments. The recovery keys are stored in Azure AD and can be retrieved from the Azure portal or via PowerShell.
1. Azure AD and Hybrid Azure AD joins
For devices that are Azure AD-joined or Hybrid Azure AD-joined, the BitLocker recovery keys are automatically backed up to Azure AD by default. This happens without the need for additional configuration beyond ensuring that the device is properly joined to Azure AD.
To verify the device is registered in both Azure AD and your domain by checking Settings > Accounts > Access work or school in your Windows devices.
2. Verify recovery keys in Azure AD
You can verify whether the recovery key is stored in Azure AD via the Azure portal:
- Sign in to the Azure portal.
- In the left-hand navigation pane, select Azure Active Directory.
- In the Azure Active Directory section, click on Devices.
- Use the search box to find the device by its name or other identifiers.
- Click on the device name from the search results to open the device's details page.
- Under BitLocker recovery keys, you will find the associated recovery key.
Alternatively and likewise, you can retrieve the recovery key using PowerShell:
- Press Windows + X and select Windows PowerShell (Admin) or Command Prompt (Admin) from the menu.
- Type the following command and hit Enter:Get-AzureADDevice -SearchString "DeviceName"
- This will return the recovery information for the device, including the BitLocker recovery key if available.
Troubleshooting
If the recovery key is not found in AD or Azure AD, likely, that BitLocker was not properly configured to back up the key, and the device was not domain-joined when BitLocker was first enabled. Group Policy was not configured to back up recovery information to AD. To retrieve recovery keys from Active Directory, you need to have Domain Administrator or Enterprise Administrator privileges. For Azure AD, you need appropriate global administrator or device administrator permissions.
Note: In Intune-managed environments, BitLocker recovery keys can be backed up to Azure AD and managed via Intune policies. Ensure that Intune policies for BitLocker encryption and recovery key backup are properly configured.
Final thought
BitLocker recovery keys can be securely stored in either Active Directory (for domain-joined devices) or Azure AD (for Azure AD-joined devices). Group Policy in AD and Intune policies in Azure AD help manage and enforce the backup of recovery keys. By correctly configuring Group Policy, Azure AD settings, and Intune policies, organizations can ensure that BitLocker recovery keys are backed up securely and are easily accessible for device recovery.
Also read What Service does the Windows BitLocker Feature Provide?
Spread this post and keep tabs on the Windows news.
