Written by
Wilsey YoungThe built-in BitLocker encryption feature on Windows helps protect our data by encrypting the entire drive, securely safeguarding our system and data and making it extremely hard for unauthorized users to access, especially when the device is lost or stolen.
However, error messages about BitLocker feature abound, which may occur before or after the BitLocker encryption is complete, causing Windows users a lot of troubles and concerns.
This post offers a quick overview of the "BitLocker cannot use Secure Boot for integrity" error message appearing in Event Viewer after a BitLocker recovery blue screen during PC system boot. You can keep reading this post to understand the root cause and seek a solution.
You can share this post by clicking the buttons below!
Reddit discussions on "BitLocker cannot use Secure Boot for integrity"
There's a post on Reddit talking about the "BitLocker cannot use Secure Boot for integrity" error message. According to the description, two types of error messages begin in the same way but end up differently.
The BitLocker user in the post briefly introduces how the error messages are fixed, and the "Manage-bde" command lines were primarily mentioned for resolving the issues. You can check the Reddit post below for more details about it.
BitLocker cannot use Secure Boot for integrity because the UEFI variable Bitlocker / PK could not be read
by u/Nuitari8 in sysadmin
What is the "BitLocker cannot use Secure Boot for integrity" error message and what are the causes?
The "BitLocker cannot use Secure Boot for integrity" error message appears in the Event Viewer on Windows. It is reported that Windows users typically notice this error message in Event Viewer after a BitLocker recovery blue screen during system boot.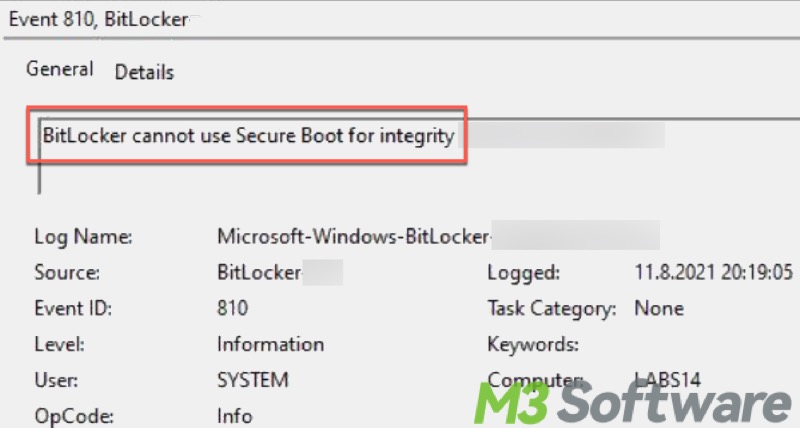
In general, you will encounter two types of "BitLocker cannot use Secure Boot for integrity" error messages that differ in ending:
- BitLocker cannot use Secure Boot for integrity because the UEFI variable 'SecureBoot' could not be read.
- BitLocker cannot use Secure Boot for integrity because the required UEFI variable 'PK' is not present.
BitLocker cannot use Secure Boot for integrity because the UEFI variable 'SecureBoot' could not be read
Some enterprises or institutions tend to have BitLocker encryption enabled across many devices without requiring each user to manually activate or configure, and this is where silent BitLocker drive encryption comes into play.
Silent BitLocker drive encryption won't take effect if Secure Boot is not enabled, thus the "BitLocker cannot use Secure Boot for integrity because the UEFI variable 'SecureBoot' could not be read" error message may arise.
BitLocker cannot use Secure Boot for integrity because the required UEFI variable 'PK' is not present.
PK refers to the Platform Key used in the UEFI Secure Boot process, ensuring that only signed or trusted software can be executed during the computer system boot, securely protecting the system from being tampered with.
The Platform Key is the root of the key chain that establishes trust. If the Secure Boot is not active, the PK will not be present and the "BitLocker cannot use Secure Boot for integrity" error will appear.
How to fix the "BitLocker cannot use Secure Boot for integrity" error?
Verifying the PCR validation profile of the TPM and the state of Secure Boot can fix both "BitLocker cannot use Secure Boot for integrity" error message types.
Step1: Verify the PCR validation profile
A PCR refers to a platform configuration register that is a memory location in TPM, and PCR 7 indicates the Secure Boot state. Here's how to verify the PCR validation profile:
- Type cmd in the start menu search bar and click "Run as administrator."
- Copy and paste the following command into the command window and hit the "Enter" key: manage-bde.exe -protectors -get %systemdrive%
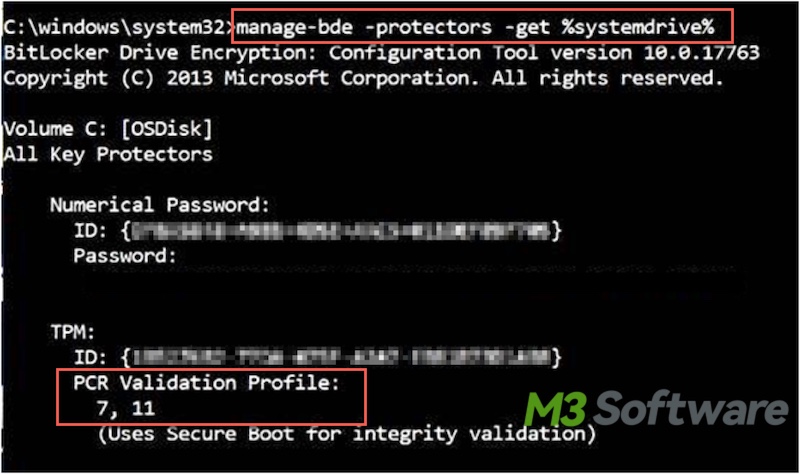
- Check whether the PCR validation profile shows 7. If 7 is not included in the PCR validation profile, it means the Secure Boot is not enabled.
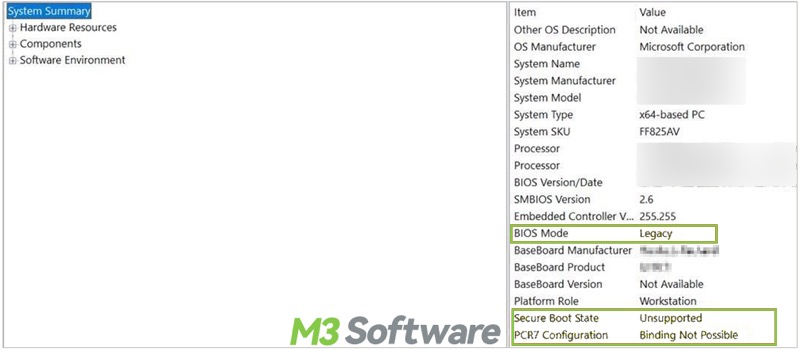
Step 2 Verify the Secure Boot state
- Type "msinfo32" in the start menu search bar and click the result to open.
- You can check the information for the Secure Boot state.
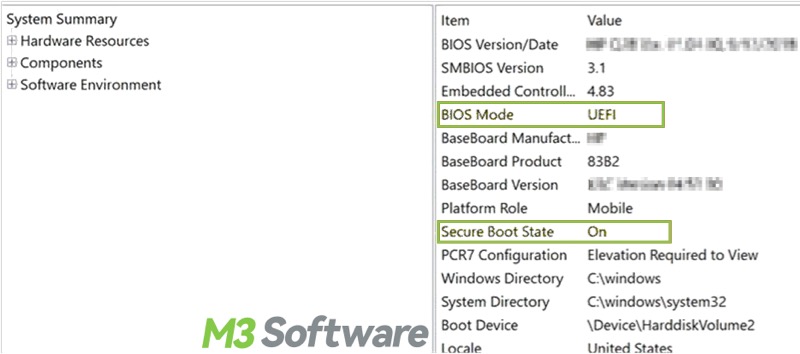
- If the Secure Boot State shows “Unsupported”, silent BitLocker Encryption can't be applied.
You can share this post if you find it helpful!
