Written by
Wilsey YoungSummary: This post sheds light on this BitLocker conflicting Group Policy error: BitLocker encryption cannot be applied to this drive because of conflicting Group Policy settings. iBoysoft DiskGeeker for Windows can help you easily encrypt disks or partitions with BitLocker on Windows OS.
BitLocker drive encryption is a security feature available in certain Windows editions. It aims to encrypt your drive and ensures that your data and sensitive information stored on the drive remain out of reach from unauthorized access, particularly when the device is lost or stolen.
However, when Windows users attempt to enable BitLocker on all devices by creating the Endpoint Protection policy or when the policy to enable BitLocker is set on Intune/Endpoint Configuration Manager, they may be confronted with the "BitLocker Group Policy conflict" error messages, leading to the failure to enable BitLocker.
In this post, we clarify the less common BitLocker-related error "BitLocker drive encryption cannot be applied to this drive because of conflicting Group Policy settings" and offer proven solutions.
You can share this post by clicking the buttons below:
Reddit discussions on "BitLocker conflicting group policy" error
The "BitLocker encryption cannot be applied to this drive because of conflicting Group Policy settings" is intensively discussed in the post on Reddit. The thread starter created an Endpoint Protection policy to enable BitLocker encryption on all his devices, and he got a specific BitLocker Group Policy conflict later on.
Netizens shared their experiences and solutions to this "BitLocker conflicting group policy" issue. The Reddit post below has more details.
Policy Conflict in Bitlocker policy
by u/JayG30 in Intune
“BitLocker conflicting group policy” errors and causes
The "BitLocker encryption cannot be applied to this drive because of conflicting group policy settings" is divided into two types, which begin with the same sentence, but the subsequent descriptions differ:
Full error message type 1:
BitLocker Drive Encryption cannot be applied to this drive because there are conflicting Group Policy settings for recovery options on fixed data drives. Storing recovery information to Active Directory Domain Services cannot be required when the generation of recovery passwords is not permitted. Please have your system administrator resolve these policy conflicts before attempting to enable BitLocker. 
Full error message type 2:
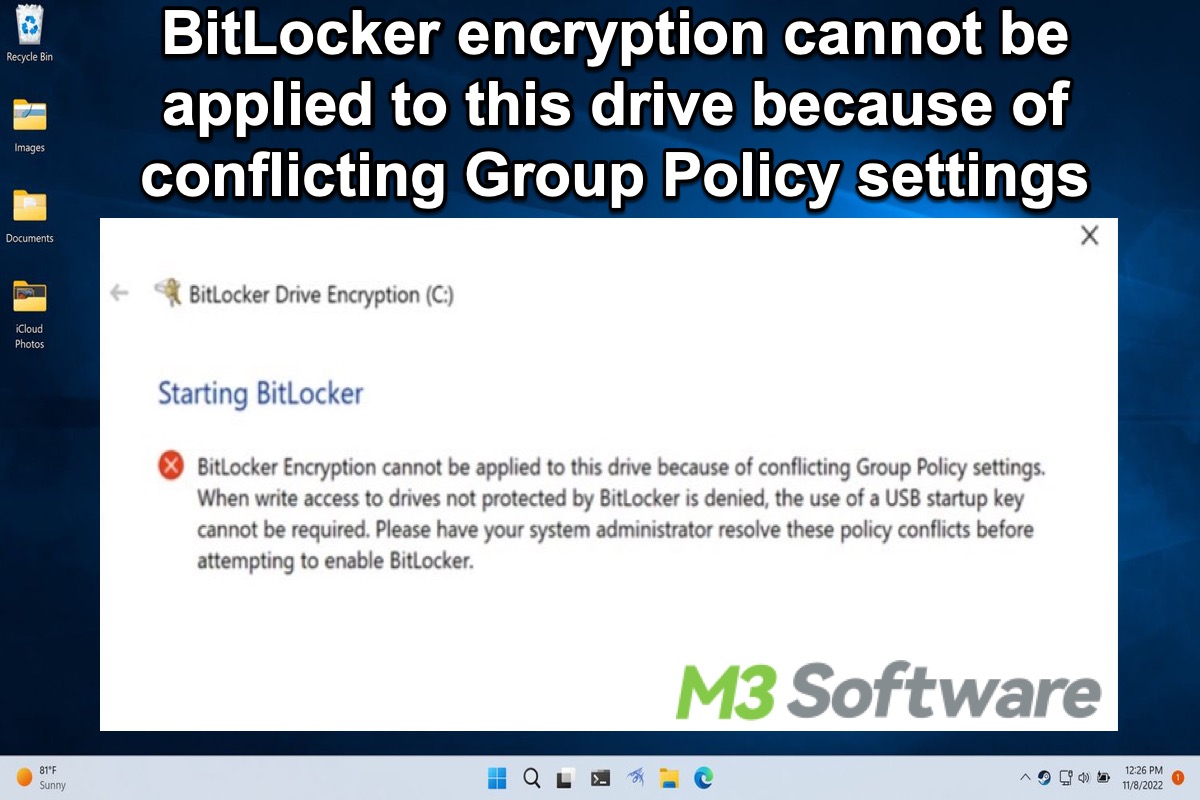
BitLocker Encryption cannot be applied to this drive because of conflicting Group Policy settings. When write access to drives not protected by BitLocker is denied, the use of a USB startup key cannot be required. Please have your system administrator resolve these policy conflicts before attempting to enable BitLocker. 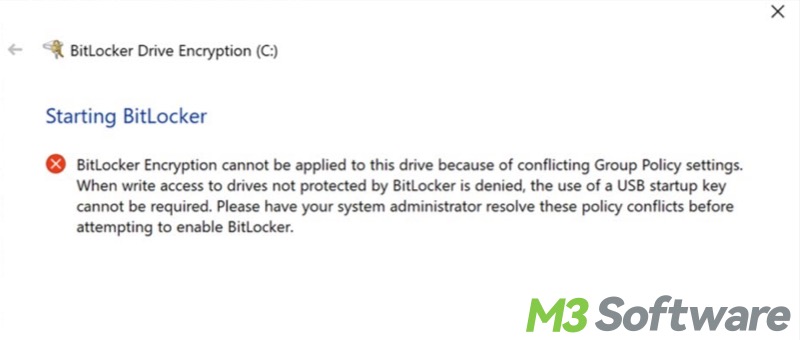
This "BitLocker encryption cannot be applied to this drive because of conflicting group policy settings" error message is caused by the FVE (Full Volume Encryption) registry key which has configurations or improperly configured BitLocker policies in Intune that may conflict with the silent encryption.
You can share this post with your friends!
Solutions to "BitLocker encryption cannot be applied to this drive because of conflicting group policy settings"
You can follow the steps below to delete the related FVE registry key or download the disk management tool to resolve the "BitLocker conflicting group policy" error.
Delete the FVE registry key via Registry Editor
You can delete the FVE (Full Volume Encryption) registry key that causes the conflicts. Here's how:
- Press the “Win+R” keys, type "regedit" in the run dialog box, and then hit the "Enter" key on your keyboard.
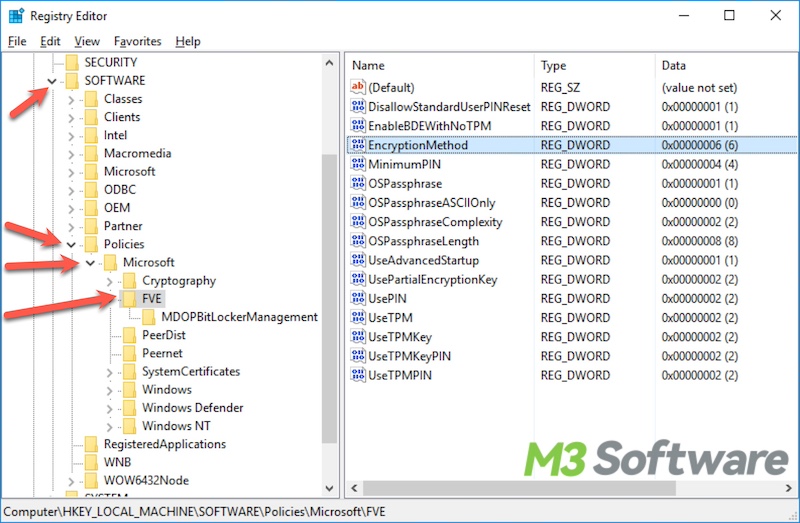
- Follow the path and expand the folder on the left: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE.
- If the FVE registry key exists, first of all, export the key for backup.
- Right-click on the entire FVE folder and delete it.
- Restart your PC and try BitLocker again.
Use BitLocker via iBoysoft DiskGeeker for Windows
iBoysoft DiskGeeker for Windows is an intuitive and professional Windows security tool. With this tool, you can easily encrypt NTFS, exFAT, and FAT32 partitions and disks using the BitLocker encryption feature.
In addition, iBoysoft DiskGeeker for Windows makes BitLocker available on Windows versions that do not support BitLocker feature by default, such as Windows 11/10/8.1/8/7 Home editions and Windows 7 Professional edition.
Most importantly, the BitLocker feature in this Windows security tool can save you the trouble of using the native BitLocker drive encryption feature built-in Windows, at the same time, some BitLocker group policy conflicts and error messages can be bypassed, such as "BitLocker encryption cannot be applied to this drive because of conflicting group policy settings" error.
When the encryption is complete, users can access the encrypted partitions with read-and-write support without any BitLocker third-party software.
You can follow the tutorial below to learn how to encrypt with BitLocker via iBoysoft DiskGeeker for Windows.
- Click the "Click to encrypt" button next to the partition from the BitLocker module in main interface.
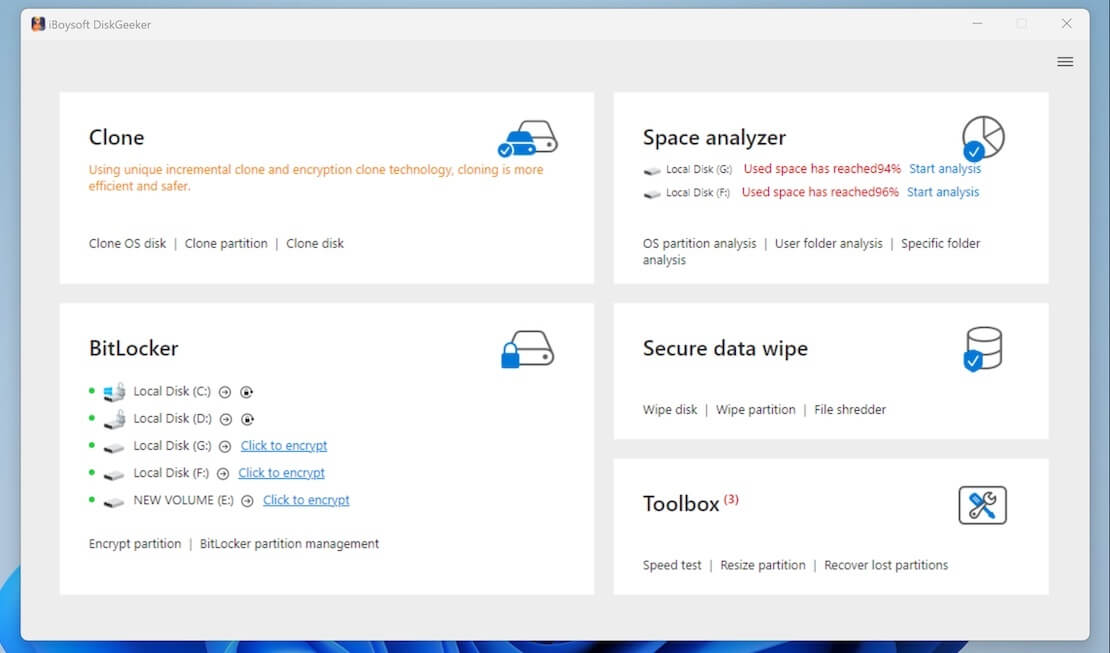
- Or, you can click "BitLocker" > "Encrypt partition" > select a targeted partition > click "Next."
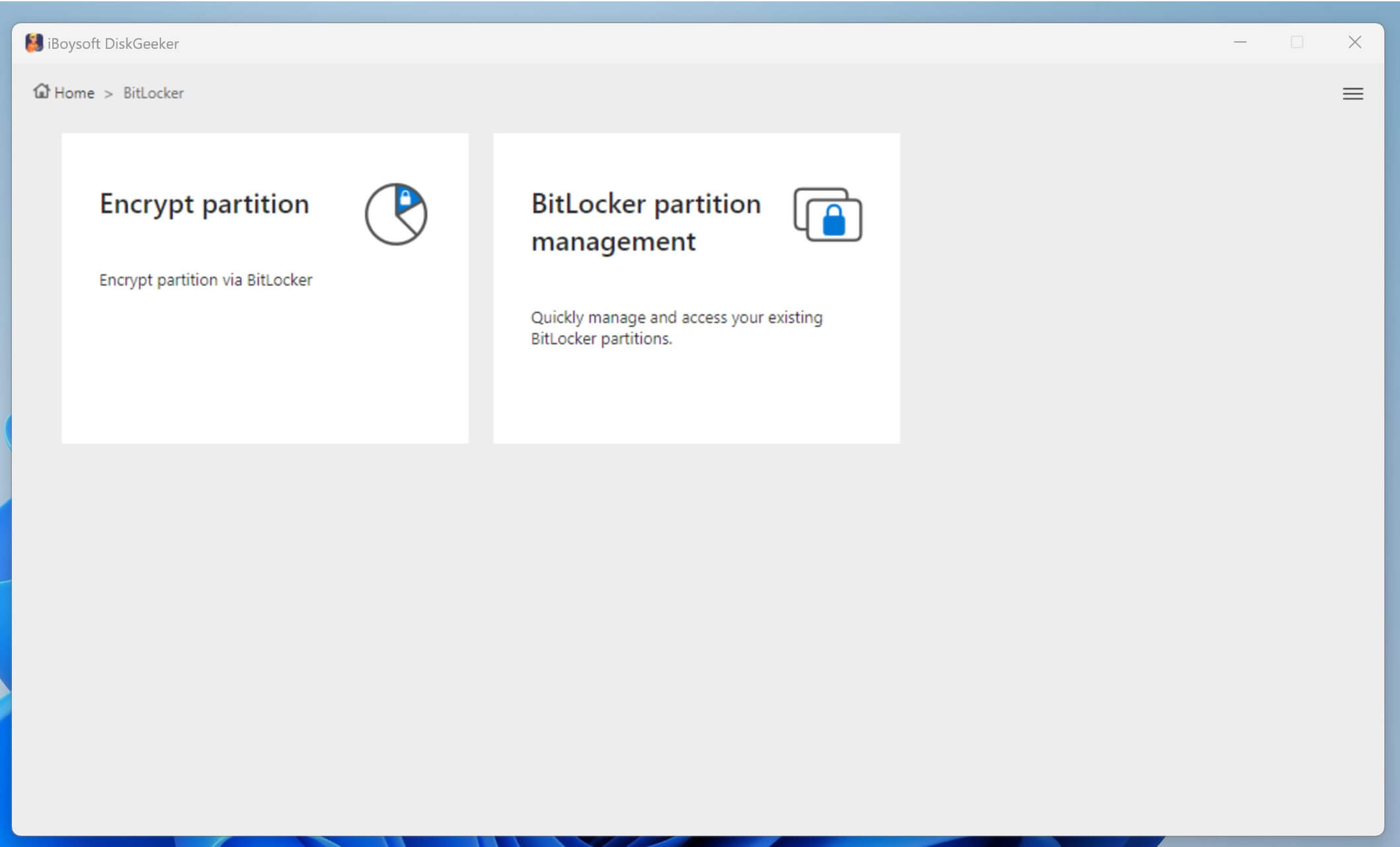
- You can only encrypt an NTFS, exFAT, and FAT32 partition. If you encrypt a partition not formatted as the NTFS, exFAT, or FAT32 file system, an error message will pop up saying "Partition type not supported."
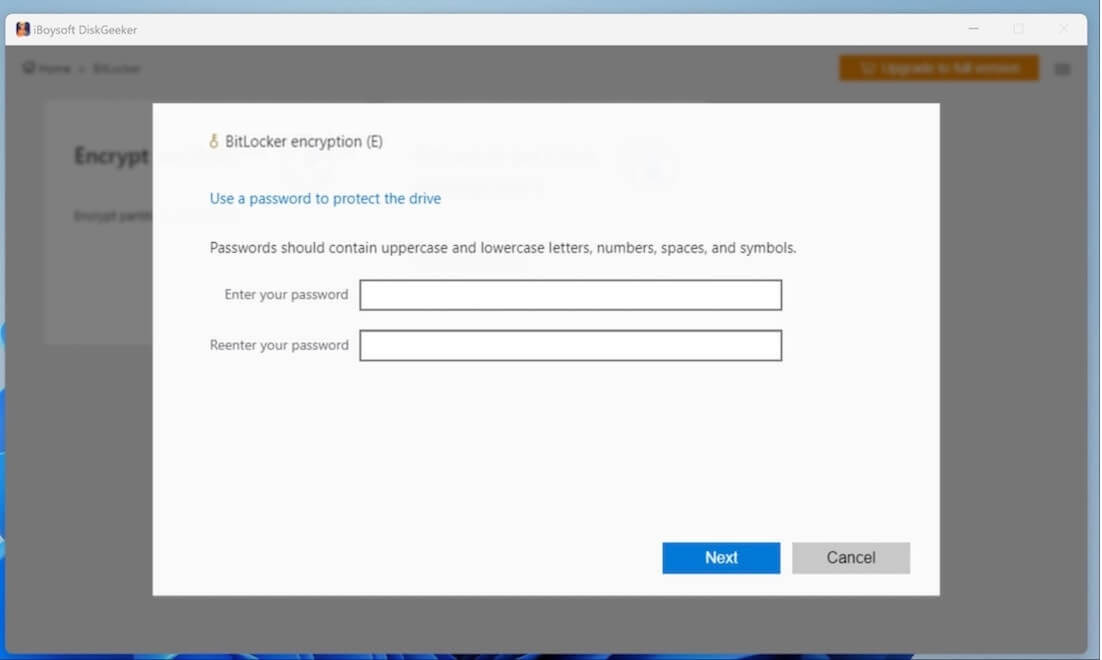
- Enter a password, enter it once again, and click "Next" to proceed.
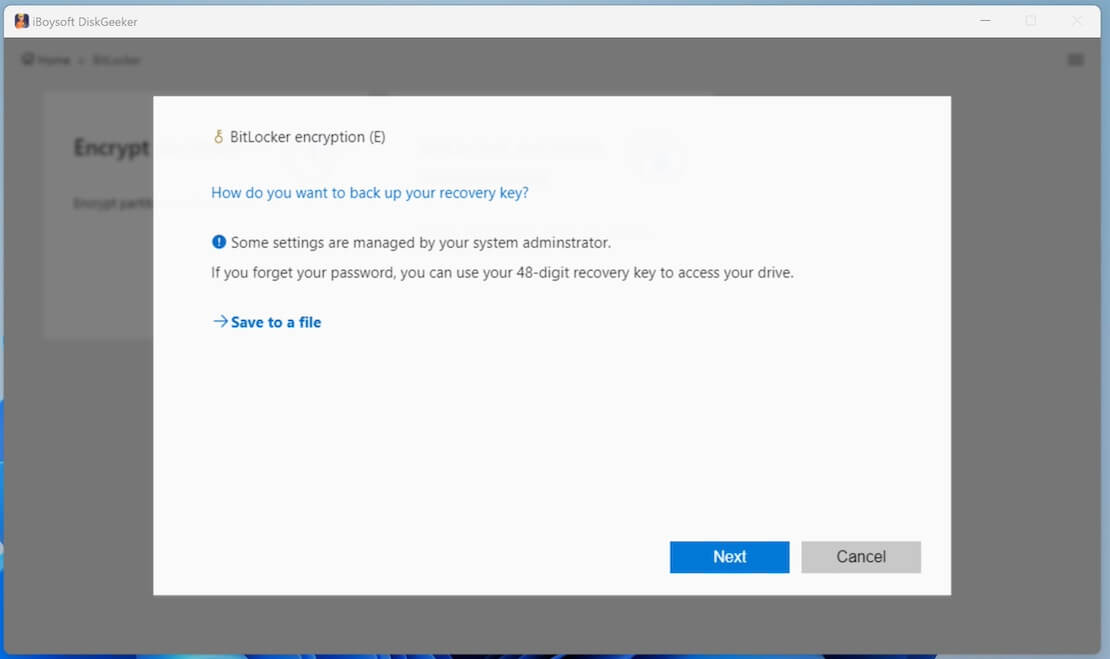
- Back up the BitLocker recovery key generated by this tool and click "Next." The recovery key is used to unlock the BitLocker-encrypted partitions or disks if you forget your password, you have to save it well before the encryption process starts.
- Click "Start encrypting" to confirm and let the encryption begin.
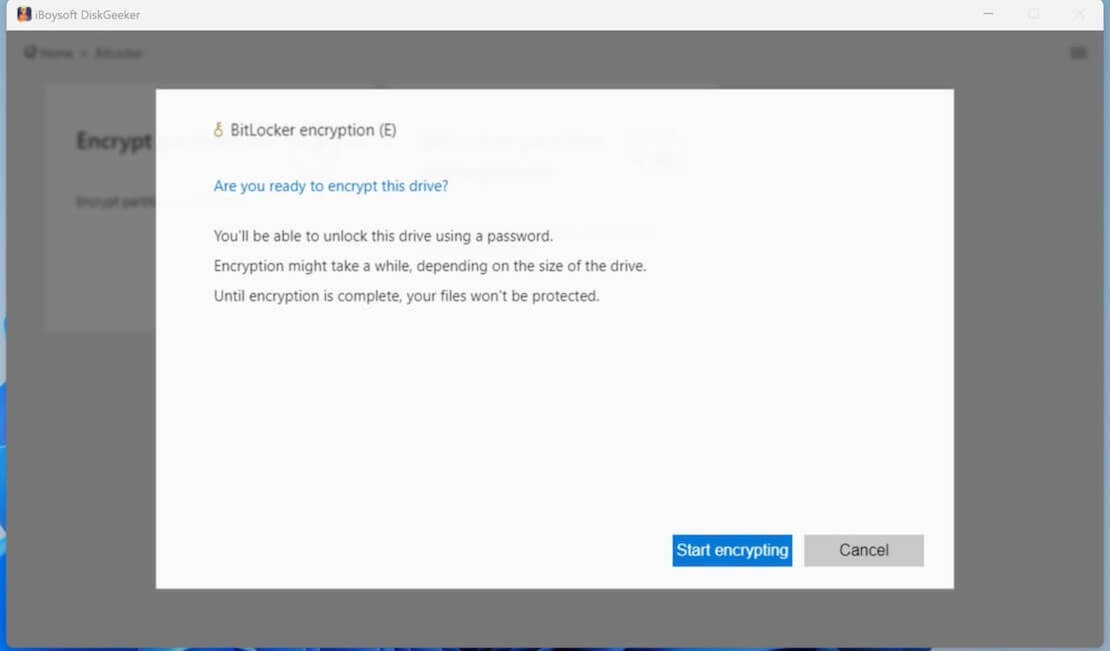
For Enterprise environment: Manage BitLocker policies via Microsoft Intune
If you come across the “BitLocker encryption cannot be applied to this drive because of conflicting group policy settings” error under the Enterprise environment, log into the Microsoft Endpoint Manager Admin Center and manage corresponding BitLocker policies via Security Baseline to resolve the conflicts.
- Go to the Microsoft Endpoint Manager Admin Center and sign in with your organization's admin credentials.
- Under Endpoint Security, you can configure policies for device security, including BitLocker.
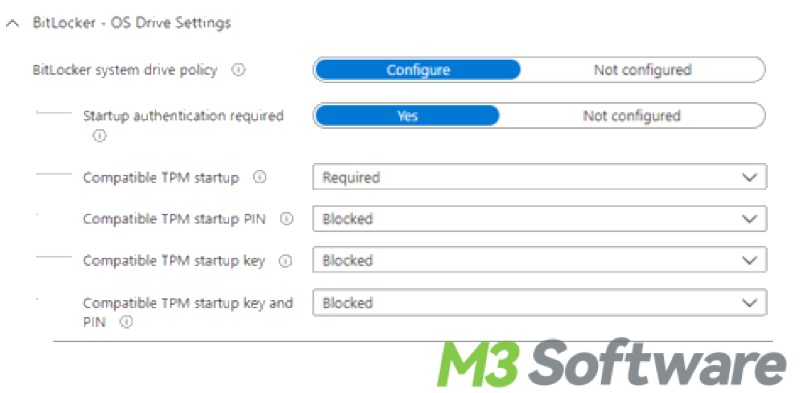
- Configure the compatible TPM startup PIN to Blocked. This will fix the BitLocker Group Policy conflicts when using silent encryption. If silent encryption is required, you must set the PIN and TPM startup key to Blocked.
- Configuring any of the compatible TPM settings to “Required” will cause silent encryption to fail.
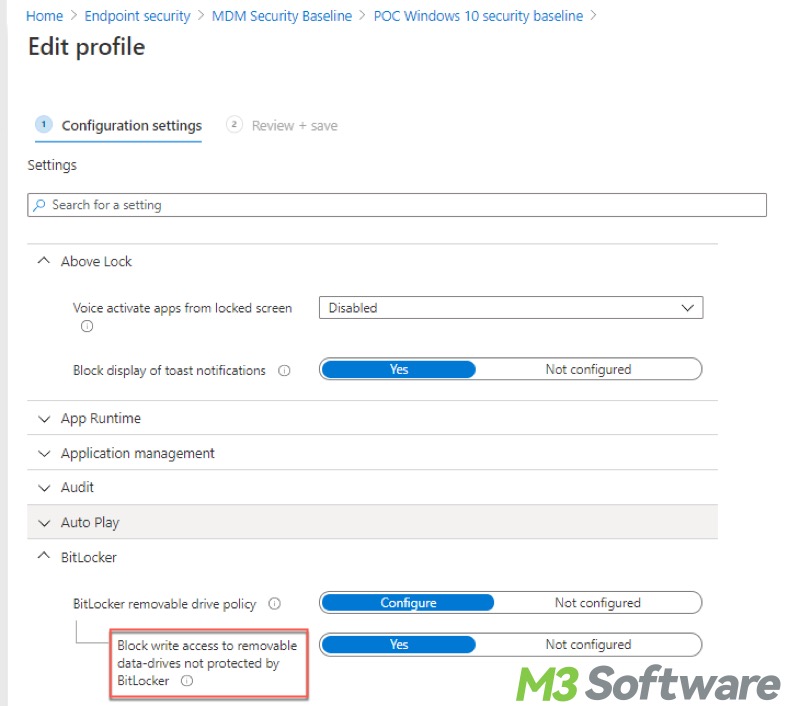
- You can also set the “Block write access to xxx drives not protected by BitLocker” to “Not configured.”
You can share this post if you find it helpful!
